
This assumes that you have already installed OpenSSL on your system.
At a high level, there are two ways to go about creating a self signed RSA (Rivest Shamir Adlema) certificate.
- As a one liner
- First create private key, then create certificate signing request (CSR), then create self signed RSA public certificate
One Liner
This one liner can be used to create a self signed RSA public certificate. The -nodes option is used to create an unencrypted private key so that you are not prompted to create a pass phrase for the private key and the -subj option provides the Certificate Signing Request (CSR) so that this command creates the public certificate and private key without any interactive prompts, making this a good command to use in scripted automation.
openssl req -x509 -sha512 -nodes -days 365 -newkey rsa:4096 -keyout example.key -out example.cer -subj "/C=US/ST=California/L=Los Angeles/O=FreeKB/OU=IT/CN=example.com"
Let's say you want your public certificate to contains extensions, like this.
x509v3 extensions:
x509v3 Subject Alternative Name:
DNS:example.com
If you are at OpenSSL version 1.1.1 or higher, the -addext option can be used to create the extensions.
~]$ openssl version
OpenSSL 1.1.1k FIPS 25 Mar 2021
~]# openssl req -x509 -sha512 -nodes -days 365 -newkey rsa:4096 -keyout example.key -out example.cer -subj "/C=US/ST=California/L=Los Angeles/O=FreeKB/OU=IT/CN=example.com" -addext "subjectAltName=DNS: example.com,DNS: www.example.com,IP: 10.0.0.1"
If you are below version 1.1.1, create a configuration file such as my.config.
[SAN]
subjectAltName=IP:10.22.51.98,IP:172.31.19.227,DNS:example.com,DNS:www.example.com
[ dn ]
C=US
ST=California
L=Los Angeles
O=FreeKB
OU=IT
CN = www.example.com
Then use this one liner with the -extfile and -extensions options.
openssl req -x509 -sha512 -nodes -days 365 -newkey rsa:4096 -keyout example.key -out example.cer -subj "/C=US/ST=California/L=Los Angeles/O=FreeKB/OU=IT/CN=example.com" -extfile my.config -extensions SAN
Or with -config and -extensions options.
openssl req -x509 -sha512 -nodes -days 365 -newkey rsa:4096 -keyout example.key -out example.cer -config my.config -extensions SAN
Private Key / Certificate Signing Request (CSR)
To create a self signed RSA public certificate using a private key file (e.g. example.com.key, check out my article on creating a private key), there are 3 ways to go about providing the Certificate Signing Request (CSR) information. This is what it means to sign the certificate.
- Interactive Prompt
- Using the -subj command line option
- Using a CSR file
Interactive Prompt Method - If you have not created a CSR file, then you will prompted for the CSR values during the creation of the public certificate. .cer and .crt and .pem are valid file extensions for the certfificate.
openssl x509 -req -sha512 -days 365 -signkey example.com.key -out example.com.cer
And here is how you could provide the CSR information using the -subj command line option
openssl x509 -req -sha512 -days 365 -signkey example.com.key -out example.com.cer -subj "/C=US/ST=California/L=Los Angeles/O=FreeKB/OU=IT/CN=example.com"
And here is how you can provide the CSR information using a CSR file. Check out my article on creating a Certificate Signing Request (CSR).
openssl x509 -req -sha512 -days 365 -signkey example.com.key -in example.com.csr -out example.com.cer
Extensions
Let's say your CSR file contains extensions, like this.
x509v3 extensions:
x509v3 Subject Alternative Name:
DNS:example.com
The -extensions option will need to be included to pass the extensions from the CSR file to the public certificate file. In this example, the extensions in the CSR file are passed into the certificate.
openssl x509
-req
-sha512
-days 365
-signkey example.com.key
-in example.com.csr
-out example.com.crt
-extensions v3_ext
-extfile example.com.config
Validation
The x509 option with the -in -text and -noout flags can be used to view the contents of the public certificate file.
openssl x509 -in example.com.crt -text -noout
...
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, ST=WI, L=Appleton, O=Example, OU=Example, CN=www.example.com/emailAddress=johndoe@example.com
Not Before: Jul 15 03:06:31 2017 GMT
Not After: July 15 03:06:31 2018 GMT
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Using the public / private key pair
You can now use the public certificate and it's corresponding private key. In this example, the private key and public certificate are placed on the web server. The CSR file is not used by the web server.
Internet facing production applications should use a certificate from a trusted CA, such as verisign.com. For non-production applications, a self-signed certificate can be used. Applications, such as a web browser, will complain when a self-signed certificate is used.
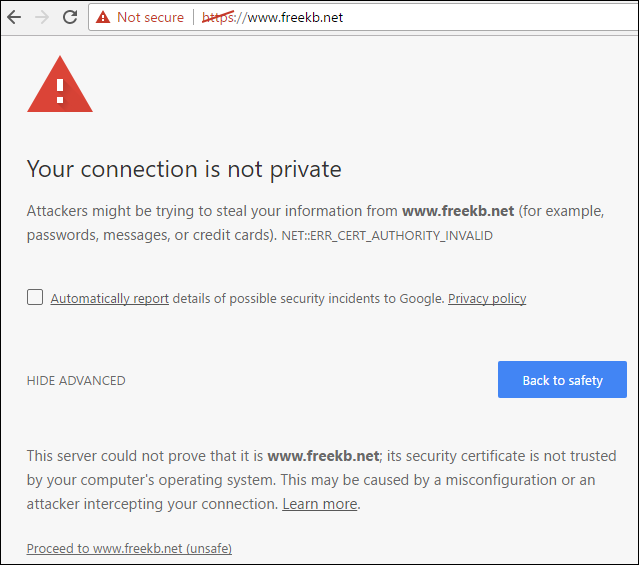
When the client navigates to an HTTPS page, the client will request the public certificate from the web server, and then the public certificate will reside on the clients browser for a period of time. The public certificate on the client and the private key on the server are what is used to encrypt the packets that are exchanged between the client and server over the internet.
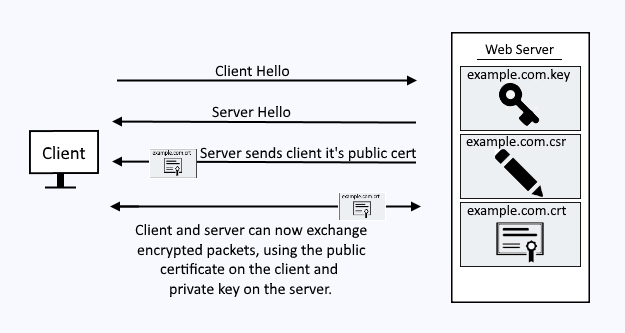
The certificate can be viewed by the client.
Did you find this article helpful?
If so, consider buying me a coffee over at 