OpenSSL - Create a public / private key pair


by
Jeremy Canfield |
Updated: May 25 2024
| OpenSSL articles
A trusted certificate is one that is purchased from a trusted certificate authority (CA), such as www.verisign.com. Internet facing production applications should use a certificate from a trusted CA. For non-production applications, a self-signed certificate can be used. Applications, such as a web browser, will complain when a self-signed certificate is used.
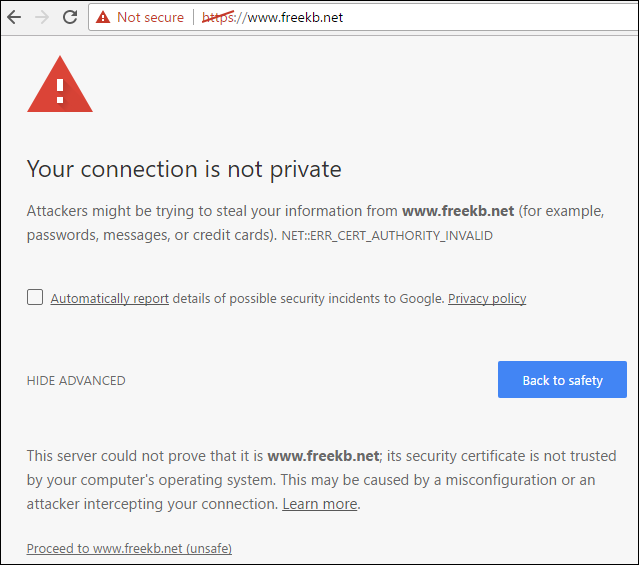
The folowing script will create the following files:
| Type of file | Location |
|---|---|
| Private Key | /etc/pki/tls/private/www.example.com.key |
| Public Certificate | /etc/pki/tls/certs/www.example.com.crt |
| Certificate Signing Request (CSR) | /etc/pki/tls/www.example.com.csr |
| Certificate Authority (CA) | /etc/pki/tls/www.example.com.pem |
| Personal Information Exchange (PFX) | /etc/pki/tls/www.example.com.pfx |
Use apt-get or yum to install OpenSSL.
[root@server1 ~]# apt-get install openssl
[root@server1 ~]# yum install openssl
The script
#!/bin/bash
# VARIABLES
date=$(date +%b-%d-%Y);
key=/etc/pki/tls/private/$myHostname.key;
crt=/etc/pki/tls/certs/$myHostname.crt;
csr=/etc/pki/tls/$myHostname.csr;
pem=/etc/pki/tls/$myHostname.pem;
echo "What would you like to do?"
read -rep $'\n1) Create new private key, public certificate, certificate signing request, and pem \n 2) Only create new public certificate \n ' answer
read -rep $'\n How many days should the public certificate be valid for?' -i '365' days
read -rep $'\n Enter the hostname of the server that will be using the public / private keypair : ' -i myHostname
# FUNCTIONS
function create_key {
chown root:root /etc/pki/tls/private
chmod 600 /etc/pki/tls/private
openssl genrsa -out /etc/pki/tls/private/$myHostname.key 2048
chmod 400 /etc/pki/tls/private/$myHostname.key
}
function create_csr {
openssl req -new -key /etc/pki/tls/private/$myHostname.key -out /etc/pki/tls/$myHostname.csr
}
function create_crt {
openssl x509 -req -days $days -in /etc/pki/tls/$myHostname.csr -signkey /etc/pki/tls/private/$myHostname.key -out /etc/pki/tls/certs/$myHostname.crt
}
function create_pem {
cat /etc/pki/tls/certs/$myHostname.crt > /etc/pki/tls/$myHostname.pem
}
# EXECUTION
if [ $answer -eq 1 ]
then
if [ -f $key ] || [ -f $crt ] || [ -f $csr ] || [ -f $pem ]
then
echo 'One or more of the public private keys already exists';
read -p 'Would you like to rename the current files to end with $date? (Y/N) ' rename
if [ $rename == "Y" ];
then
mv /etc/pki/tls/private/$myHostname.key /etc/pki/tls/private/$myHostname.key_$date
mv /etc/pki/tls/certs/$myHostname.crt /etc/pki/tls/certs/$myHostname.crt_$date
mv /etc/pki/tls/$myHostname.csr /etc/pki/tls/$myHostname.csr_$date
mv /etc/pki/tls/$myHostname.pem /etc/pki/tls/$myHostname.pem_$date
create_key
create_csr
create_crt
create_pem
else
echo 'Exiting'
fi
else
create_key
create_csr
create_crt
create_pem
fi
fi
if [ $answer -eq 2 ]
then
if [ -f $crt ]
then
echo 'The public certificate already exists';
read -p 'Would you like to rename the current public certificate to end with $date? (Y/N) ' rename
if [ $rename == "Y" ];
then
mv /etc/pki/tls/certs/$myHostname.crt /etc/pki/tls/certs/$myHostname.crt_$date
create_crt
else
echo 'Exiting'
fi
else
create_crt
fi
fi
Did you find this article helpful?
If so, consider buying me a coffee over at 