
If you are unfamiliar with the difference between a keystore and a truststore, check out this article.
- In the WebSphere admin console, expand Security and select SSL certificate and key management.
- Select SSL configurations.
- Select key stores and certificates.
- Select a keystore.
- Select Personal certificates.
Note - private keys are found in the Personal certificates area of the WebSphere admin console, and public certificates are found in the Signer area of the WebSphere admin console. When working with IBM / WebSphere, keep in mind that instead of calling a private key a private key, it may be called a personal certificate, and a public certificate may be called a signer. Fun.
In this example, there are two entries. The first is the default certificate, and the second is the certificate chain. Probably the most important information displayed is the expiration date of the keys and certificates in the keystore.
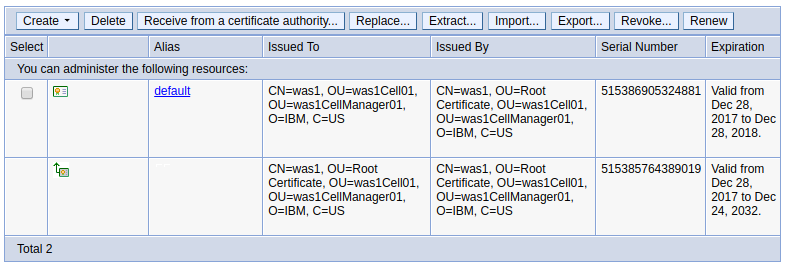
The keytool command can be used to view the keys and certificates in the keystore. When using the keytool command, the password for the default trust.p12 and key.p12 files created when WebSphere is installed is WebAS. If WebAS is not working, check the password for the keystore or truststore in the was_home/profiles/your_profile/config/cells/your_cell/security.xml file.
<Keystores xmi
id="KeyStore_1"
name="cellDefaultKeyStore"
password="{xor}CDo9Hgw="
When connecting to the WebSphere admin console, HTTPS can be used to encrypt the connection. The web browser will compalin that the site is not secure. This is the expected behavior when using the certificate in the default keystore that is created when WebSphere is installed, because the certificate in the default keystore is not trusted by a certificate authority (CA).
After letting the web browser know that you want to connect to the WebSphere admin console, the browser will get the certificate from the default keystore. In this example, a certificate with a SHA1 fingerprint ending in 4D is obtained from the default keystore.
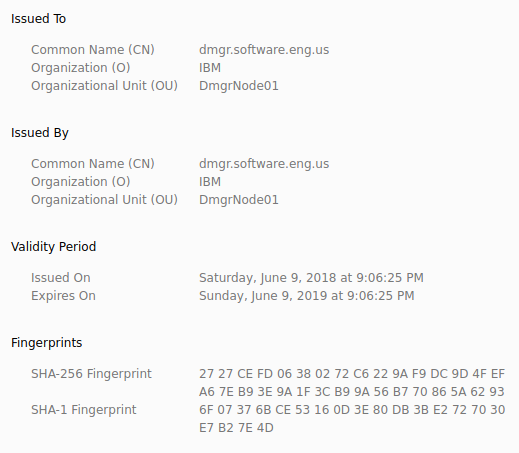
Likewise, the SHA1 fingerprint of the root certificate in the default keystore ends in 4D, which gives certaintly that the encryption was done via the public/private keypair in the default keystore.
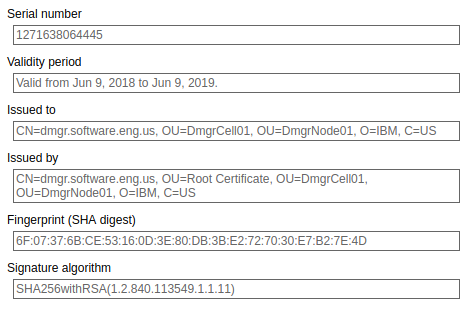
Likewise, if you have apps that are using the default keystore, the browser will complain that the site is not secure. This is perfectly OK in your development environment, but should never be used in a production environment. You can purchase a certificate from a trusted certificate authority (CA), such as www.verisign.com, and then the browser will no longer complain that the site is not secure.
Did you find this article helpful?
If so, consider buying me a coffee over at 