
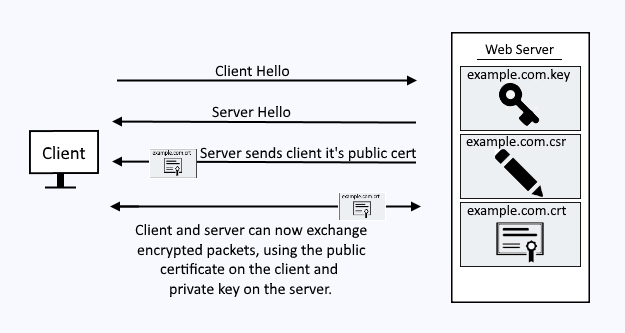
A public certificate and private key pair are used to encrypt packets being transmitted between a client and IBMs IHS web server.
Key Database
IBM stores the public certificate and private key in what is called a Key Database. The Key Database is a file that ends with the .kdb extension. There are a few different ways to create the public certificate and private key in the Key Database file.
For the sake of this article, let's say you have a Key Database file named example.kdb and a stash file named example.sth, and the Key Database contains a certificate, such as *.example.com.
${ihs_install_root}/gsk8/bin/gsk8capicmd_64 -cert -list -db /path/to/example.kdb -stashed
Certificates found
* default, - personal, ! trusted, # secret key
*- *.example.com
AVOID TROUBLE
The certificate Common Name (CN) will almost always need to match the DNS hostname of the web server the certificate is being used for. For example, if the certificate will be used for SSL / HTTPS on the web server producing www.freekb.net, then the certificates common name (CN) will need to be www.freekb.net or *.freekb.net.
IMPORTANT
The certificate in the Key Database must be proceeded by the - character, meaning the certificate is "personal". If the certificate is proceeded by the ! character, meaning the certificate is "trusted", the web server will fail to produce HTTPS web pages over SSL.
Configure IHS
At minimum, add the following to your IHS httpd.conf file. After modifying your httpd.conf file, restart the IHS web server.
LoadModule ibm_ssl_module modules/mod_ibm_ssl.so
Listen 443
<VirtualHost *:443>
SSLEnable
</VirtualHost>
SSLDisable
KeyFile "/path/to/example.kdb"
SSLStashFile "/path/to/example.sth"
If you have two or more server certificates in the Key Database file, by default, the default certificate in the Key Database file will be used. Or, you can use the SSLServerCert directive to specify the server certificate to use.
LoadModule ibm_ssl_module modules/mod_ibm_ssl.so
Listen 443
<VirtualHost *:443>
SSLEnable
SSLServerCert *.example.com
</VirtualHost>
KeyFile "/path/to/example.kdb"
SSLStashFile "/path/to/example.sth"
SSLDisable
You should now be able to get resources from your IHS web server over SSL. If you are using a self-signed certificate, your browser will complain that the certificate is invalid. This is fine if you are doing this in a development environment, but for production, you should use a certificate from a trusted certificate authority.
Did you find this article helpful?
If so, consider buying me a coffee over at 