
There are two ways to configure WebSphere to authenticate against LDAP. You can either configure WebSphere to authenticate against a standalone LDAP repository, or you can configure WebSphere to authenticate against a federated repository, and then add LDAP to the federated repository. Adding LDAP to a federated repository is usually preferred over a standalone LDAP repository, because a federated repository includes the ability to authenticate against LDAP, as well as other authentication systems, so there is an alternate authentication resource if authentication against LDAP fails.
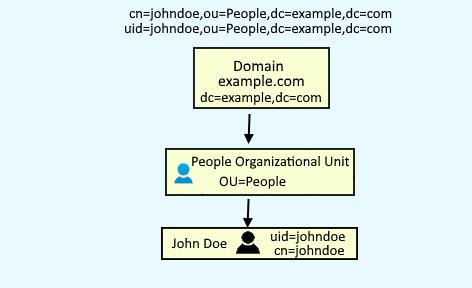
Let's take an example of a LDAP server with the following structure.
In the left panel of the WebSphere admin console, expand Security > Global Security. If you are going to configure a standalone LDAP repository, select Standalone LDAP repository and select Configure. If you are going to add LDAP to a federated repository, select Federated repository and select Configure.
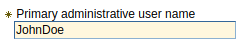
In primary administrative username, enter one of your LDAP users.
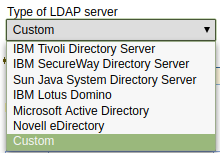
Select the type of LDAP server you are using. If your LDAP server is not listed, select Custom.
Enter the hostname and port of your primary LDAP server.

And your ${WAS_INSTALL_ROOT}/profiles/your_profile/config/cells/your_cell/security.xml file should contain something like this.
<userRegistries
xmi:type="security:LDAPUserRegistry"
xmi:id="LDAPUserRegistry_1"
serverId="cn=john.doe,ou=mgmt,ou=svcs,o=example"
serverPassword="{xor}ABCEjdtOGkOJWgMaXYZ"
realm="ldap.example.com:389"
ignoreCase="true"
useRegistryServerId="true"
primaryAdminId="cn=john.doe,ou=mgmt,ou=svcs,o=example"
type="NDS"
sslEnabled="false"
sslConfig=""
baseDN="o=example"
bindDN="cn=jane.doe,ou=mgmt,ou=svcs,o=example"
bindPassword="{xor}ABCtKxyz"
searchTimeout="120"
reuseConnection="true">
You can then test your LDAP connection and test an LDAP query.
Configure WebSphere to authenticate against LDAP
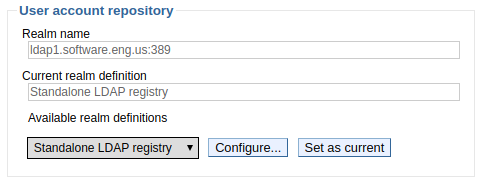
If you are setting up a standalone LDAP repository, select Standalone LDAP repository and select Set as current. The Realm name and Current realm definition should update to display LDAP. Select Apply, and then select Save.
If you are adding LDAP to a federated repository, select Federated repository and select Set as current. The Realm name and Current realm definition should update to display Federated Repository. Select Apply, and then select Save.

The following event should be recorded in ${was_install_root}/profiles/your_profile/logs/dmgr/SystemOut.log. Restart the dmgr for this change to take effect.
SECJ0419I: The user registry is currently connected to LDAP server ldap://ldap.example.com:389
Sign out of the WebSphere admin console, and you should now be able to sign in using your primary administrative LDAP user account.
Did you find this article helpful?
If so, consider buying me a coffee over at 