
Let's say the following is in the HPEL or SystemOut log.This error occurs when attempting to configure WebSphere to authenticate against a repository, such as LDAP.

This event should be recorded in your was_home/profiles/your_profile/logs/dmgr/SystemErr.log.
CWWIM5020E Could not connect to ldap://ldap.example.com:389 repository using properties:
...
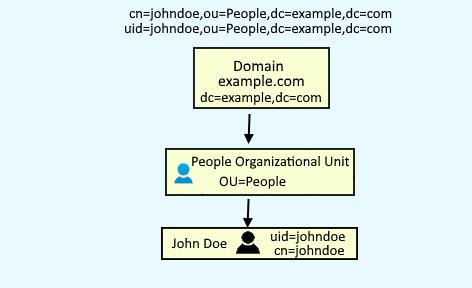
Let's take an example of a LDAP server with the following structure.
To configure LDAP
- In the WebSphere admin console, expand Security > Global Security.
- In the User account repository section, select Standalone LDAP repository and select Configure.
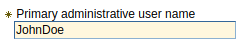
In primary administrative username, enter one of your LDAP users.
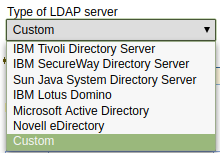
Select the type of LDAP server you are using. If your LDAP server is not listed, select Custom.
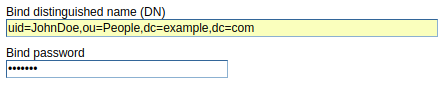
Enter the hostname and port of your primary LDAP server.

In Base distinguished name, enter only your LDAP domain.

In Bind distinguished name, enter your main LDAP user, the organization unit (OU) the user is in (usually People), and the domain name. Some LDAP servers will use common name (cn) and some will use user id (uid). For example, these two entries are completely different records in LDAP.
cn=johndoe,ou=people,dc=example,dc=com
uid=johndoe,ou=people,dc=example,dc=com
Use cn or uid based on how your LDAP server is configured.
Select OK. Select Save.
If you selected a custom LDAP server type, you will probably need to update the user filter field. Select Advanced Lightweight Directory Access Protocol (LDAP) user registry settings. By default, the User filter field will have (&(uid=%v)(objectclass=ePerson)). Update the User filter field to mirror how your LDAP server is configured. For example, OpenLDAP uses "uid" and "inetOrgPerson".
~]# ldapsearch -x -b dc=example,dc=com
dn: uid=JohnDoe,ou=People,dc=example,dc=com
objectClass: inetOrgPerson
In this example, the User filter field would be updated to be (&(uid=%v)(objectclass=inetOrgPerson)). If User filter is updated to have cn=%v, you should also updated the User ID map to be *:cn.
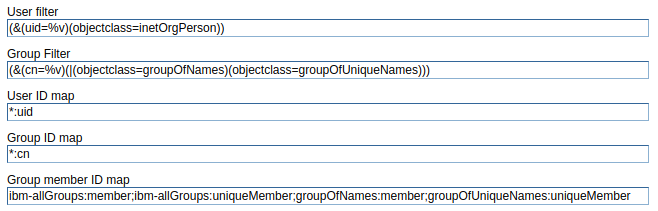
Making a change to the advanced LDAP user registry settings will create this event in was_home/profiles/your_profile/logs/dmgr/SystemOut.log.
ADMR0016I: User defaultWIMFileBasedRealm/your_username modified document cells/your_cell/security.xml
Test LDAP connection
- In the WebSphere admin console, select Security > Global security.
- In the User Account Repository section, select Standalone LDAP registry and select Configure.
- Select Test connection.
The result of the test connection must be successful. If the test connection is not successful, you either provided an invalid ldap hostname or port, or there is some issue between WebSphere and LDAP (eg. LDAP is down, firewall refusing connection, et cetera).
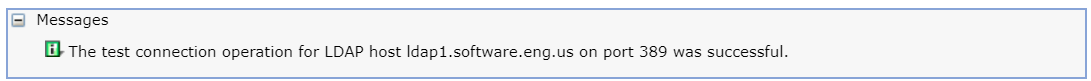
Test LDAP Query
- In the WebSphere admin console, expand Security > Global Security.
- In the User account repository section, select Standalone LDAP repository and select Configure.
- Select LDAP Test Query.
In this example, a query is done for user JohnDoe in the ldap.example.com server. Remember to use cn or uid based on how your LDAP server and WebSphere are setup. Instead of searching for a specific user, uid=* or cd=* can be used to search for every LDAP user.
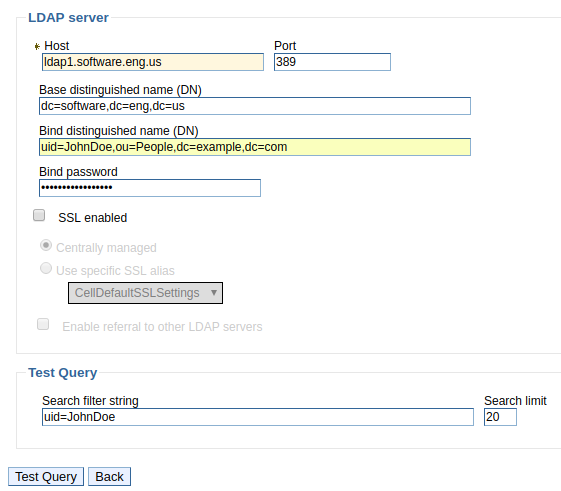
In this example, the test query was successful.

Configure WebSphere to authenticate against LDAP
There are two ways to configure WebSphere to authenticate LDAP. You can either configure WebSphere to authenticate against LDAP and only LDAP, or you can configure WebSphere to authenticate against a federated repository. Configuring WebSphere to authenticate against a federated repository may be preferred over LDAP repository, because a federated repository includes the ability to authenticate against LDAP, as well as other systems, so there is an alternate authentication resource if authentication against LDAP fails.
To configure WebSphere to authenticate against LDAP and only LDAP
- In the WebSphere admin console, expand Security > Global Security.
- In the User account repository section, select Standalone LDAP repository and select Set as current. The Realm name and Current realm definition should update to display LDAP.
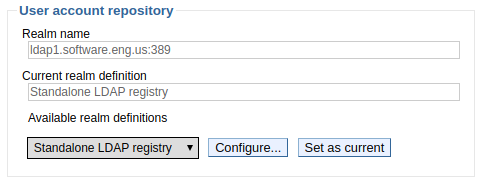
Select Apply, and then select Save. The following event should be recorded in was_home/profiles/your_profile/logs/dmgr/SystemOut.log. Restart the dmgr for this change to take effect.
SECJ0419I: The user registry is currently connected to LDAP server ldap://ldap.example.com:389
Sign out of the WebSphere admin console, and you should now be able to sign in using your primary administrative LDAP user account.
Did you find this article helpful?
If so, consider buying me a coffee over at 