SSL - Client Certificate Authentication


by
Jeremy Canfield |
Updated: March 08 2022
| SSL articles
Simply put, Client Certificate Authentication, also know as Mutual Auth, is when a client and a server establish a secured connection using a public/private key pair on the server and a public certificate on the client.
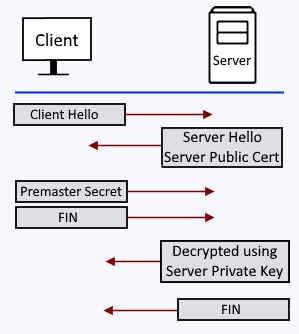
Let's say there is a web server that produces HTTPS web pages, such as https://www.example.com. When a client submits a request to get a web page from the web server, here is how the TLS handshake should occur without mutual auth.
- The client sends a "Client Hello" packet to the server.
- The server sends it's public certificate to the client (e.g. server.cer) in a "Server Hello" packet.
- The client validates the public certificate against it's list of trusted certificate authorities (CA), and if the servers public certificate has been issued by a trusted certificate authority, the client sends the server a premaster secret (random string of data). The premaster secret is encrypted with the servers public certificate (e.g. server.cer). The client adds the servers public certificate it its store of trusted public certificates.
- The server decrypts the premaster secret with the servers private key.
- The client generates a session key and sends the server a FIN (finished) packet.
- The server generates a session key and sends the client a FIN (finished) packet.
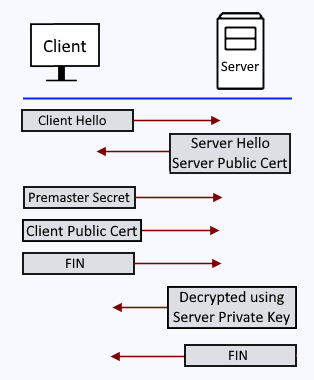
And here is how the TLS handshake should occur with Mutual Auth.
- The client sends a "Client Hello" packet to the server.
- The server sends it's public certificate to the client (e.g. server.cer) in a "Server Hello" packet.
- The client validates the public certificate against it's list of trusted certificate authorities (CA), and if the servers public certificate has been issued by a trusted certificate authority, the client sends it's public certificate to the server (e.g. client.cer). The client also sends the server a premaster secret (random string of data). The premaster secret is encrypted with the servers public certificate (e.g. server.cer). The client adds the servers public certificate it its store of trusted public certificates.
- The server decrypts the premaster secret with the servers private key. The server adds the clients public certificate it its store of trusted public certificates.
- The client generates a session key and sends the server a FIN (finished) packet.
- The server generates a session key and sends the client a FIN (finished) packet.
Did you find this article helpful?
If so, consider buying me a coffee over at 