
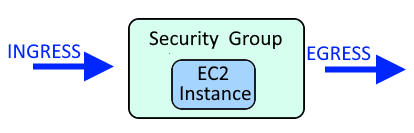
A Security Group is used to allow or deny requests coming in (ingress) and/or requests going out (egress). For example, a Security Group could be used to only allow requests within a certain IP address range to come in (ingress) and go out (egress) of an EC2 Instance.
Let's say you have the following files on your Terraform server.
├── required_providers.tf
├── security_groups (directory)
│ ├── data.tf
│ ├── outputs.tf
│ ├── resources.tf
├── virtual_private_clouds (directory)
│ ├── data.tf
│ ├── outputs.tf
│ ├── resources.tf
required_providers.tf will almost always have this.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
}
}
}
Let's say provider.tf has the following. In this example, the "default" profile in /home/username/.aws/config and /home/username/.aws/credentials is being used. This assumes you have setup Terraform as described in Amazon Web Services (AWS) - Getting Started with Terraform.
provider "aws" {
alias = "default"
profile = "default"
region = "default"
}
Let's say you have a Virtual Private Cloud (VPC) named my-vpc.
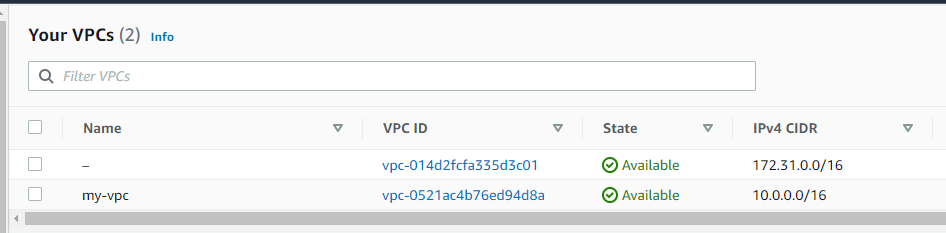
data.tf in your virtual_private_clouds directory could have something like this, where the "data" block is used to get the ID of my-vpc.
data "aws_vpc" "my-vpc" {
filter {
name = "tag-key"
values = ["Name"]
}
filter {
name = "tag-value"
values = ["my-vpc"]
}
}
And resources.tf in your security_groups directory could have something like this.
resource "aws_security_group" "my-security-group" {
name = "my security group for port 443"
description = "security group for port 443"
vpc_id = data.aws_vpc.my-vpc.id
ingress {
description = "Allow incoming (ingress) requests on port 443"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["10.0.0.0/16"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "security group for port 443"
}
}
You may need to reissue the terraform init command.
~]# terraform init
Initializing the backend...
Initializing modules...
Initializing provider plugins...
Terraform has been successfully initialized!
The terraform plan command can be used to see what Terraform will try to do.
terraform plan
By default, the terraform.tfstate file should be found in your root module directory (/usr/local/terraform/aws in this example).
- If the Security Group does not exist and the terraform.tfstate file does not contain the Security Group, Terraform will create the Security Group.
- If the Security Groupexists and the terraform.tfstate file contains the Security Group and a difference is found between the sg.tf file and the terraform.tfstate file, Terraform will update the Security Group.
- If the Security Groupexists and the terraform.tfstate file contains the Security Group and the Security Group is removed from the sg.tf file, Terraform will destroy (delete) the Security Groups.
The terraform apply command can be used to create, update or delete the Security Group.
terraform apply
Did you find this article helpful?
If so, consider buying me a coffee over at 