
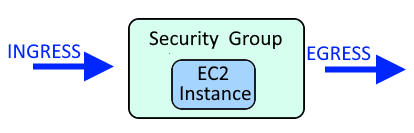
A Security Group is used to allow or deny requests coming in (ingress) and/or requests going out (egress). For example, a Security Group could be used to only allow requests within a certain IP address range to come in (ingress) and go out (egress) of an EC2 Instance.
This assumes you have already configured the aws command line tool. If not, check out my article on Getting Started with the AWS CLI.
The aws ec2 describe-security-group-rules command can be used to list the inbound and outbound rules associated with your EC2 security groups.
aws ec2 describe-security-groups
Something like this should be returned.
]$ aws ec2 describe-security-group-rules
{
"SecurityGroupRules": [
{
"SecurityGroupRuleId": "sgr-05ee7f82c0ae7578f",
"GroupId": "sg-0778124087b3d14d4",
"GroupOwnerId": "123456789012",
"IsEgress": false,
"IpProtocol": "tcp",
"FromPort": 22,
"ToPort": 22,
"CidrIpv4": "0.0.0.0/0",
"Description": "Allow SSH",
"Tags": []
}
]
}
The aws ec2 authorize-security-group-ingress command can be used to add a new Inbound / Ingress EC2 security group rule. If a rule already exists with the same exact protocol (TCP) and port (22) and CIDR, something like "InvalidPermission.Duplicate already exists" will be returned. You may want to instead use the aws ec2 modify-security-group-rules command to added CIDR's to the existing ingress Security Group Rule.
aws ec2 authorize-security-group-ingress --group-id sg-0778124087b3d14d4 --protocol tcp --port 22 --cidr 0.0.0.0/0
The aws ec2 authorize-security-group-egress command can be used to add a new Outbound / Egress EC2 security group rule. If a rule already exists with the same exact protocol (TCP) and port (22) and CIDR, something like "InvalidPermission.Duplicate already exists" will be returned. You may want to instead use the aws ec2 modify-security-group-rules command to added CIDR's to the existing egress Security Group Rule.
aws ec2 authorize-security-group-egress --group-id sg-0778124087b3d14d4 --protocol tcp --port 22 --cidr 0.0.0.0/0
Or, you can use this syntax, which allow you to set the port range and description.
aws ec2 authorize-security-group-egress --group-id sg-048cff9f4800618f4 --ip-permissions IpProtocol=tcp,FromPort=80,ToPort=80,IpRanges='[{CidrIp=0.0.0.0/0,Description='yo'}]'
More commonly, -1 is used to allow all outbound.
aws ec2 authorize-security-group-egress --group-id sg-abcdef012345678 --ip-permissions IpProtocol=-1,FromPort=-1,ToPort=-1,IpRanges='[{CidrIp=0.0.0.0/0,Description='Allow All'}]'
The aws ec2 modify-security-group-rules command can be used to modify your Inbound or Outbound EC2 security group rules that already exist. The Security Group Rule ID is used to match the inbound or outbound rule that will be updated.
~]$ aws ec2 modify-security-group-rules --group-id sg-0778124087b3d14d4 --security-group-rules SecurityGroupRuleId=sgr-05ee7f82c0ae7578f,SecurityGroupRule='{Description="Allow SSH from All",IpProtocol="TCP",FromPort=22,ToPort=22,CidrIpv4=0.0.0.0/0}'
Did you find this article helpful?
If so, consider buying me a coffee over at 