
There are a few ways to configure HAProxy SSL. One way is that the HAProxy frontend would be configured with SSL, the backends would not be configured with SSL. This is known as SSL Termination or Edge SSL.
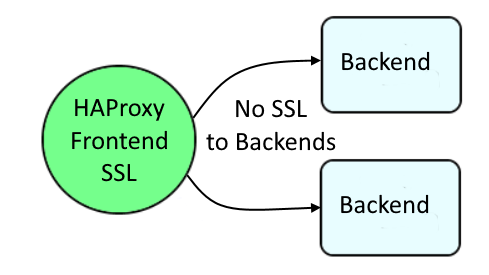
Another way is that the frontend would not be configured with SSL, and the backends would be configured with SSL.
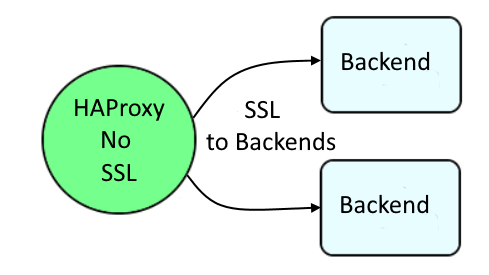
Or you could have any sort of mixture of the two, where some frontends are configured with SSL, others are not, some backends are configured with SSL, others are not.
This assume you have a PEM file that contains the public certificates and private key needed for SSL. Certbot can be used to create a wildcard public private key pair.
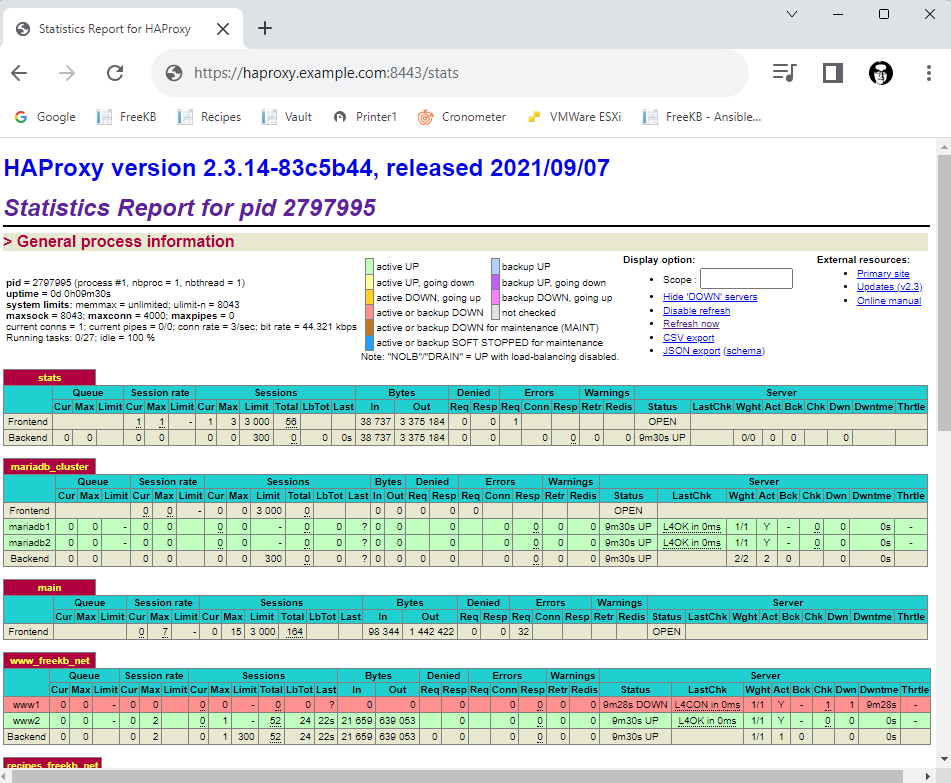
For testing purposes, the HAProxy stats endpoint can be setup for SSL. In this example, the /stats endpoint is setup for SSL on port 8443 using the haproxy.pem file that contains the public private SSL keys.
listen stats
bind *:8080
bind *:8443 ssl crt /etc/letsencrypt/archive/example.com/haproxy.pem
http-request redirect scheme https unless { ssl_fc } <- optional, to force HTTP to redirect to HTTPS
stats enable
stats refresh 10s
stats uri /stats
Or, better yet, you could store your PEM files in a directory such as /usr/local/certbot/pem and then set the ssl directive to point to the directory that contains that PEM files.
listen stats
bind *:8080
bind *:8443 ssl crt /usr/local/certbot/pem
http-request redirect scheme https unless { ssl_fc } <- optional, to force HTTP to redirect to HTTPS
stats enable
stats refresh 10s
stats uri /stats
If you have a firewall, such as iptables or firewalld, allow the SSL port (8443 in this example) in the firewall, just for testing purposes.
firewall-cmd --add-port=8443/tcp
Restart HAProxy.
systemctl restart haproxy
And you should now be able to request the /stats endpoint at https://<IP address or DNS name of your HAProxy>:8443/stats.
Did you find this article helpful?
If so, consider buying me a coffee over at 