
If you are not familiar with the Amazon Web Services (AWS) CLI, check out my article Getting Started with the AWS CLI.
In Build > Pipeline editor, update your .gitlab-ci.yml file to contain something like this. In this example, I'm testing the aws configure list command, as a super simple test just to see if the aws CLI is able to return output.
aws_cli_test:
image: registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest
script:
- aws configure list
The pipline job output should return something like this. In this example, the job passed, meaning the image (aws-base:latest) in this example is able to return output via the aws CLI.
Running with gitlab-runner 16.1.0~beta.59.g83c66823 (83c66823)
on blue-1.shared.runners-manager.gitlab.com/default j1aLDqxS, system ID: s_b437a71a38f9
feature flags: FF_USE_IMPROVED_URL_MASKING:true
Preparing the "docker+machine" executor
Using Docker executor with image registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest ...
Authenticating with credentials from job payload (GitLab Registry)
Pulling docker image registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest ...
Using docker image sha256:c92d24ce053e526269f814867ab9442ff17b30721f0691158a40abd7b67aead2 for registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest with digest registry.gitlab.com/gitlab-org/cloud-deploy/aws-base@sha256:91773d7cc5afdac8aa8a5c305ba2263fc76de483ba4b00a035cf71436f8ad2a0 ...
Preparing environment
00:03
Running on runner-j1aldqxs-project-46323147-concurrent-0 via runner-j1aldqxs-shared-1687844278-fb47c404...
Getting source from Git repository
00:01
Fetching changes with git depth set to 20...
Initialized empty Git repository in /builds/JohnDoe/demo/.git/
Created fresh repository.
Checking out 29968560 as detached HEAD (ref is main)...
Skipping Git submodules setup
$ git remote set-url origin "${CI_REPOSITORY_URL}"
Executing "step_script" stage of the job script
00:01
Using docker image sha256:c92d24ce053e526269f814867ab9442ff17b30721f0691158a40abd7b67aead2 for registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest with digest registry.gitlab.com/gitlab-org/cloud-deploy/aws-base@sha256:91773d7cc5afdac8aa8a5c305ba2263fc76de483ba4b00a035cf71436f8ad2a0 ...
$ aws configure list
Name Value Type Location
---- ----- ---- --------
profile <not set> None None
access_key <not set> None None
secret_key <not set> None None
region <not set> None None
Cleaning up project directory and file based variables
00:01
Job succeeded
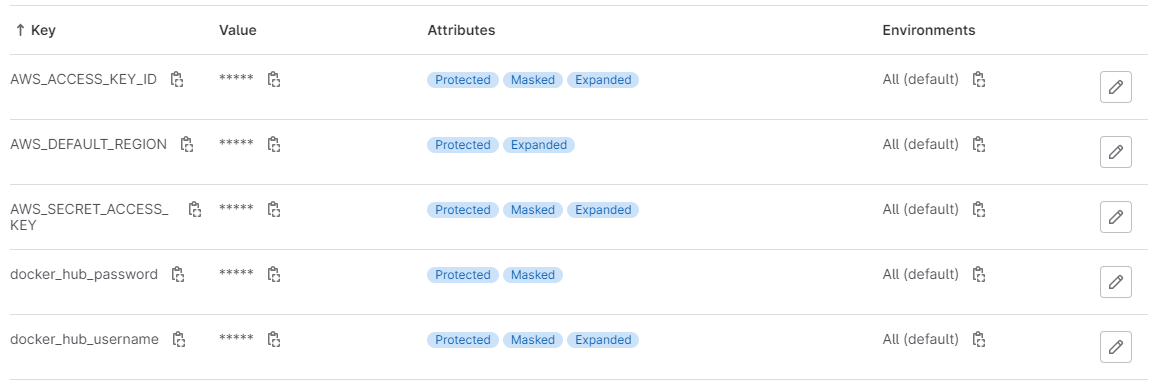
The prior test did not require authentication to Amazon Web Services. However, there are other tests that will first require you to authenticate. The AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY and AWS_DEFAULT_REGION variables can be set so that you can authenticate to Amazon Web Services.
Key and Region.
Then you could test something much more practical, such as using the aws ec2 start-instances command to start one of your EC2 instances.
aws_cli_test:
image: registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest
script:
- aws ec2 start-instances --instance-id i-041420e3b9fa55818
If the test is successful, something like this should be returned.
Running with gitlab-runner 16.1.0~beta.59.g83c66823 (83c66823)
on blue-3.shared.runners-manager.gitlab.com/default zxwgkjAP, system ID: s_284de3abf026
feature flags: FF_USE_IMPROVED_URL_MASKING:true
Preparing the "docker+machine" executor
00:18
Using Docker executor with image registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest ...
Authenticating with credentials from job payload (GitLab Registry)
Pulling docker image registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest ...
Using docker image sha256:c92d24ce053e526269f814867ab9442ff17b30721f0691158a40abd7b67aead2 for registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest with digest registry.gitlab.com/gitlab-org/cloud-deploy/aws-base@sha256:91773d71234fdac8aa8a5abcdba2263fc76d1234ba4b00a035abcd436f8ad2a0 ...
Preparing environment
00:04
Running on runner-zxwgkjap-project-46323147-concurrent-0 via runner-zxwgkjap-shared-1687845351-340a6755...
Getting source from Git repository
00:01
Fetching changes with git depth set to 20...
Initialized empty Git repository in /builds/JohnDoe/demo/.git/
Created fresh repository.
Checking out f4c244c4 as detached HEAD (ref is main)...
Skipping Git submodules setup
$ git remote set-url origin "${CI_REPOSITORY_URL}"
Executing "step_script" stage of the job script
00:02
Using docker image sha256:c92d2123453e526269fabcd67ab94421234b30721f0691abdd40abd7b67aead2 for registry.gitlab.com/gitlab-org/cloud-deploy/aws-base:latest with digest registry.gitlab.com/gitlab-org/cloud-deploy/aws-base@sha256:91773d71234fdac8aa8a5abcdba2263fc76d1234ba4b00a035abcd436f8ad2a0 ...
$ aws ec2 start-instances --instance-id i-041420e3b9fa55818
{
"StartingInstances": [
{
"CurrentState": {
"Code": 0,
"Name": "pending"
},
"InstanceId": "i-041420e3b9fa55818",
"PreviousState": {
"Code": 80,
"Name": "stopped"
}
}
]
}
Cleaning up project directory and file based variables
00:00
Job succeeded
Did you find this article helpful?
If so, consider buying me a coffee over at 