
Let's say you have a database in an Amazon Web Services (AWS) private subnet (no Internet access) and you have a Lambda Function that connects to the database. By default, Lambda Functions running in their own, isolated Virtual Private Cloud (VPC) thus the Lambda Function will not be able to connect to the database in your private subnet. If you are not familiar with private subnets, check out my article Amazon Web Services (AWS) - Create Private Subnet (no Internet access).
What to do?
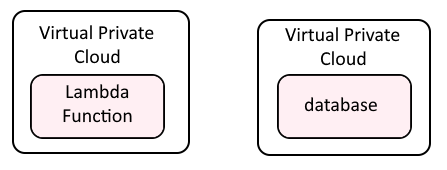
At a high level, you will do the following so that your Lambda Function can connect to your database in the private subnet.
- Update your Lambda Function IAM Role to include AWSLambdaVPCAccessExecutionRole.
- Create a Security Group that will be associated with your Lambda Functions to allow connections to the Security Group associated with your database in the private subnet
- Update the Security Group being used by your database in the private subnet to allow connections from the Security Group that will be associated with your Lambda Function
- Update your Lambda Function to be in the same Virtual Private Cloud (VPC) as your database in the private subnet
Update your Lambda Function IAM Role to include AWSLambdaVPCAccessExecutionRole
In the AWS console, pull up your Lambda Function, go to the Configuration tab, select Permissions, and select the Role name.
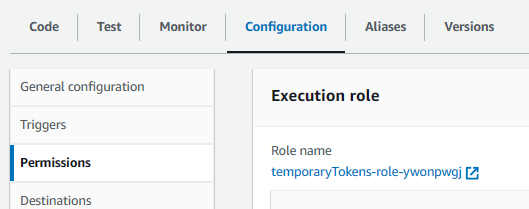
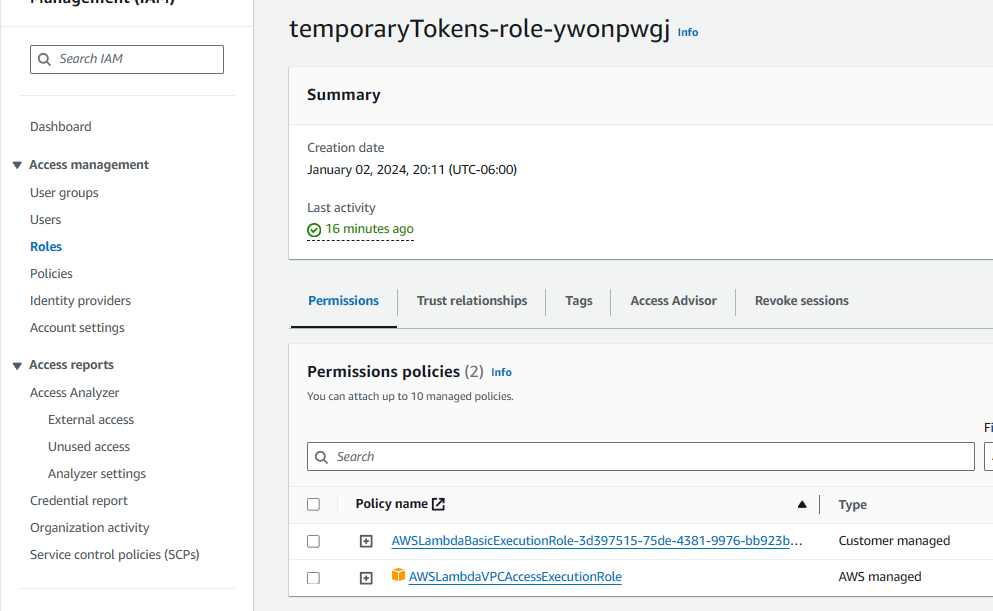
Update the Role Permission Policies to include AWSLambdaVPCAccessExecutionRole.
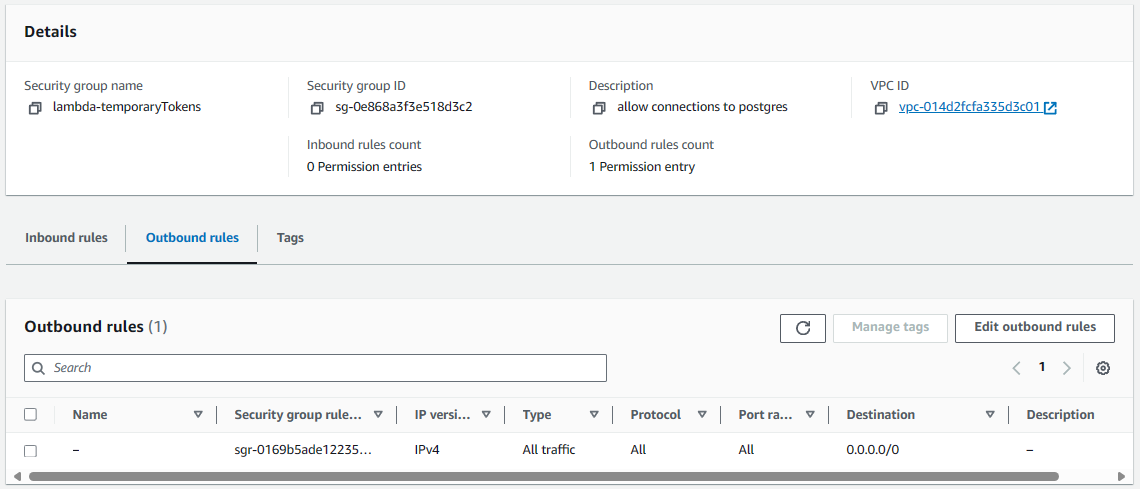
Create a Security Group that will be associated with your Lambda Functions to allow connections to the Security Group associated with your database in the private subnet
Let's create a Security Group that will be used by the Lambda Function for connections to your database in the private subnet. The Security Group does not need any Inbound Rules since the Lambda Function will be initiating the connection to the database in the private subnet, meaning the Security Group will only need an outbound rule that will allow connections to the database in the private subnet. Since this traffic should be totally internal to the private subnet, I would probably just keep the default output rule to allow all, so that if down the road your database is updated with a different Security Group or different port, then no changes will need to be made to the Security Group that will be associated wtih the Lambda Function, and will also prevent any sort issue with the Lambda Function connecting to the database.
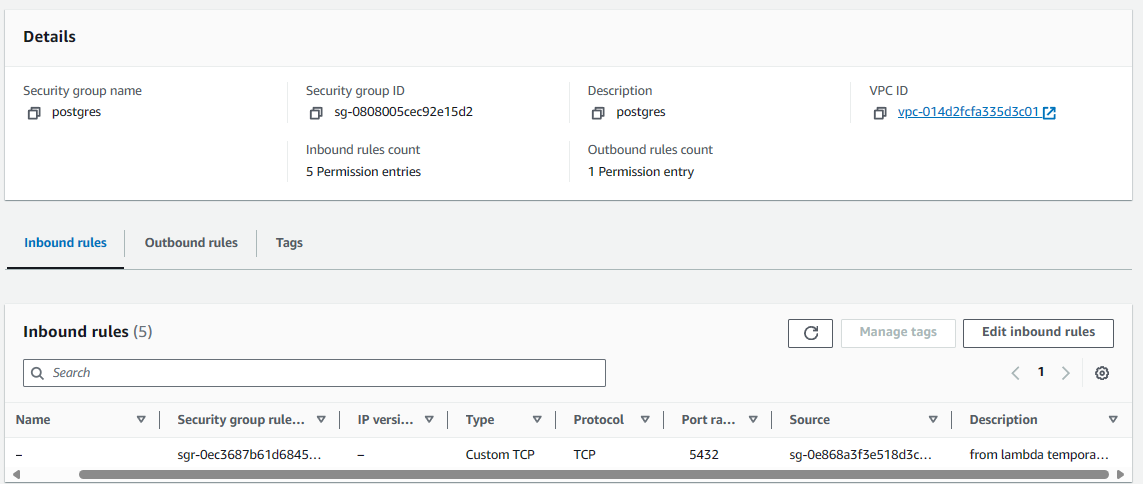
Update the Security Group being used by your database in the private subnet to allow connections from the Security Group that will be associated with your Lambda Function
Now that we have a Security Group that will be associated with the Lambda Function that will allow connections to the database in the private subnet, let's update the Security Group associated with the database in the private subnet with an inbound rule that allows connections from the Security Group that will be associated with the Lambda Function.
Update your Lambda Function to be in the same Virtual Private Cloud (VPC) as your database in the private subnet
Now that the Security Groups are configured to allow connections from the Lambda Function to the database in the private subnet, we can update the Lambda Function to be in the same Virtual Private Cloud (VPC) as the database.
Back in the Lambda console, go to the Configuration tab, select VPC, and select Edit. Select the VPC your database is in, with the same subnets being used by the database, and the Security Group that allows connections from the Lambda Function to the database in the private subnet.
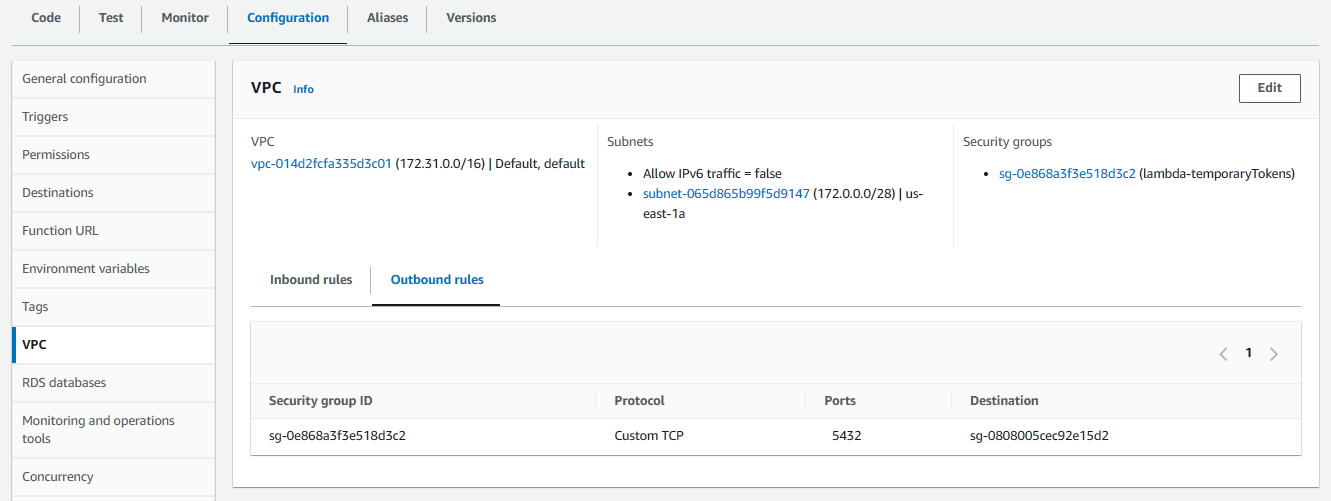
Now your Lambda Function and database are in the same Virtual Private Cloud (VPC). Your Lambda Function should now be able to connect to your database.
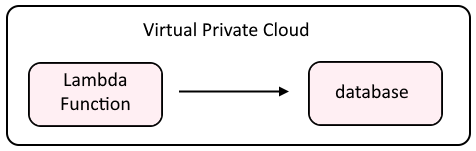
As an example, perhaps your Lambda Function uses Python psycopg2 to connect to a Postgres database in the private subnet.
import json
import psycopg2
def lambda_handler(event, context):
try:
connection = psycopg2.connect(database="mydb",
host="10.0.0.8",
user="john.doe",
password="itsasecret",
port="5432",
timeout=2)
except Exception:
return {'statusCode': 500, 'body': json.dumps({"result": "failed" })}
else:
connection.close()
return {'statusCode': 200, 'body': json.dumps({"result": "success" })}
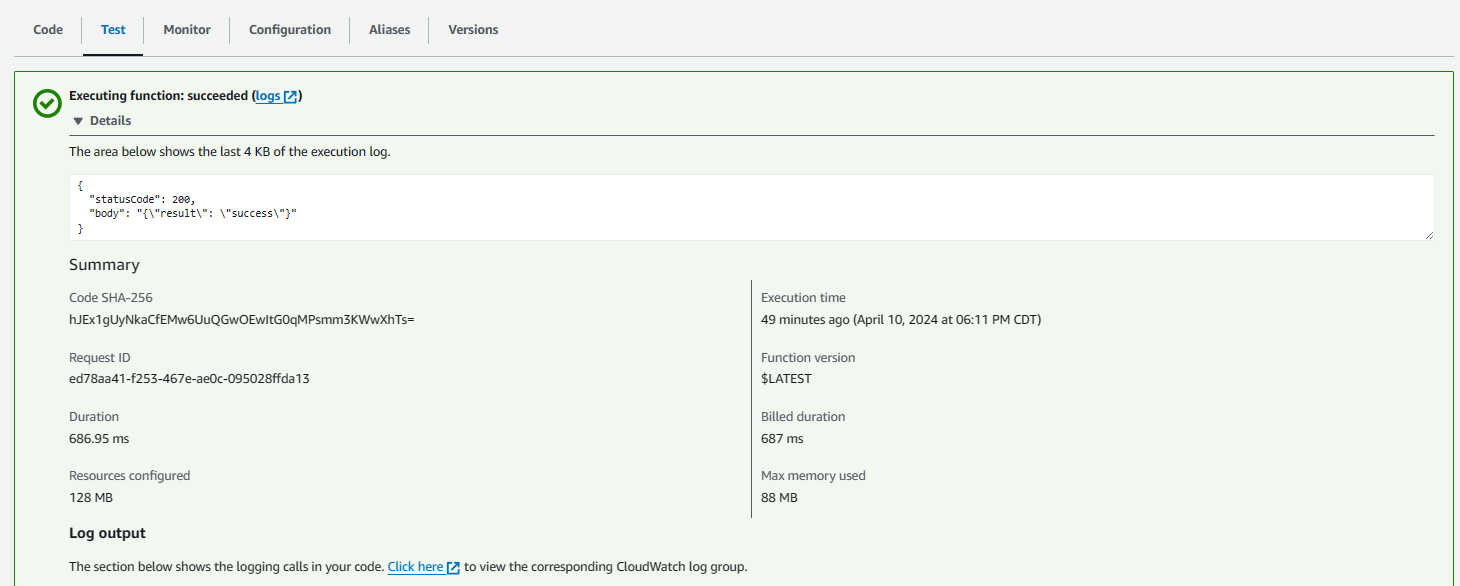
Using the Test tab in your Lambda Function, you could invoke the Lambda Function to see if the connection to the database in your private subnet did or did not raise an exception.
Did you find this article helpful?
If so, consider buying me a coffee over at 