
If error The User Profile Service failed the logon appears when attempting to sign into Windows, hopefully there is a different user account you can use that will let you sign into Windows. It is noteworthy that the User Profile Service must be running in order for you to be able to sign in and sign out of Windows. Whatever you do, do not disable the User Profile Service. If you Disable the User Profile Service, you will be unable to sign in or sign out of Windows.
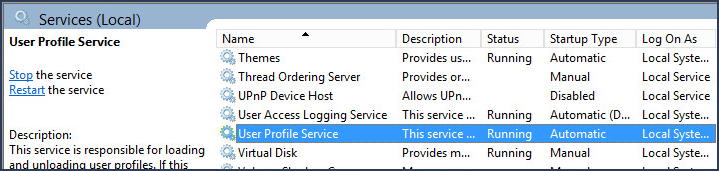
If you are able to sign into another Windows PC using a domain user account, this means the error is being produced due to some issue with the client PC. In this situation, make a copy of the C:\Users\Default folder on a PC that you are able to sign into using a domain user account. Then sign into the problem client PC with a local user account, and replace the C:\Users\Default folder.
If you are able to sign into Windows with a different user account, look for User Profile Service events in Event Viewer.
- Select the Windows Start icon, type event in search, and select Event Viewer.
- In Event Viewer, expland Windows Logs and select System.
- Search for error events where the Source is NETLOGON.
On the domain controller, ensure the status of the NETLOGON service is Running.
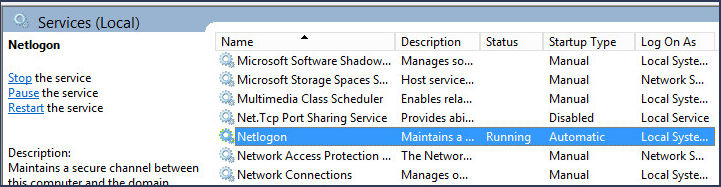
On the client machine, ensure that networking is started before logon:
- Select the Windows Start icon, type gpedit in search, and select Group Policy Editor.
- Expand Computer Configuration > Administrative Templates > System > Logon.
- Enable Always wait for the network at computer startup and logon.
On the client machine, delay the startup policy.
- Select the Windows Start icon, type gpedit in search, and select Group Policy Editor.
- Expand Computer Configuration > Administrative Templates > System > Logon > Group Policy.
- Set Startup policy processing wait time to 120.
To ensure the Domain Controller is receiving the request, in the Event Viewer on the Domain Controller, expland Windows Logs, select Security, and ensure there is a Kerberos service ticket requested with the account logon name. In this example, there is a Kerberos service ticket requested by john.doe@software.eng.apl.
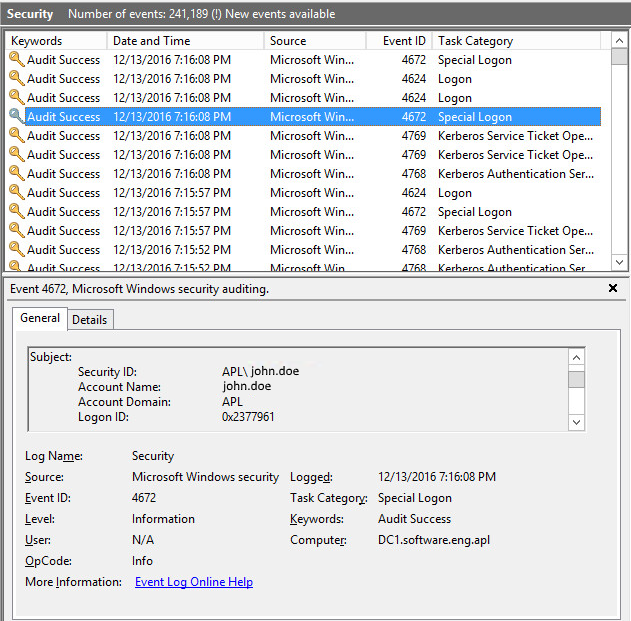
On the client machine, look for an event in Event Viewer > Windows Log > Security with Event ID 4624. 4624 signifies a successful logon. According to CompTIA Network+ by Mike Meyers, Kerberos "timestamping requires that all the clients and servers synchoronize their clocks". For this reason, it is important to ensure that both the Domain Controller and Windows client PCs or Linux client PCs are using the same NTP server. Notice in the Event Viewer on the Domain Controller and the client have the event at the same time, 1:07:56 AM. This ensures the time is in sync.
Did you find this article helpful?
If so, consider buying me a coffee over at 