
Remote access to the machine can be refused to non-root users by creating the file /etc/nologin. Even if this file is empty, remote access will be denied to non-root users. Root will still be able to remotely access the machine.
[root@server1 ~]# touch /etc/nologin
This does not prevent physical access to the machine. If the machine is a laptop or tablet, or if the machine is a tower with a keyboard, mouse, and monitor connected, both root and non-root users will be able to sign into the machine.
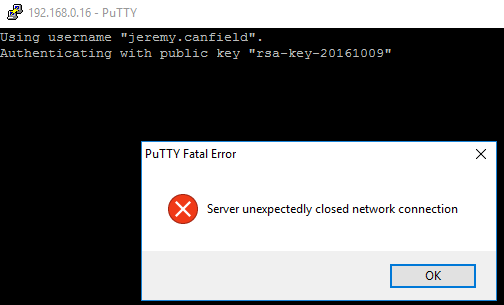
Once the /etc/nologin file is created, when attempting to make an SSH connection to the server with a non-root account, some type of connection failed message should be displayed. For example, Server unexpectedly closed network connection may be displayed.
Text can be added to the /etc/nologin file so that users recognize that only root is permitted remote access to the machine. For example, lets say the /etc/nologin file has the following:
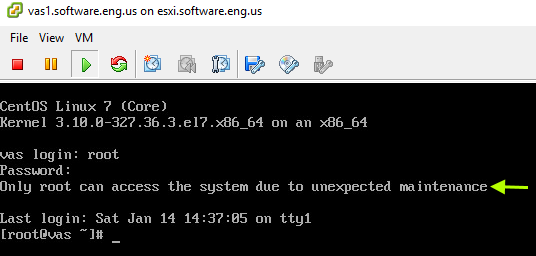
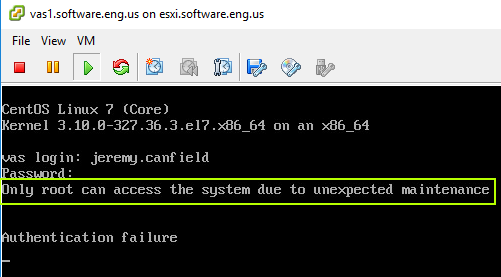
Only root can access the system due to unexpected maintenance
This message will be displayed when root connects to the machine. However, root will be able to login.
The message will be displayed when a non-root user connects to the machine, and the user will not be granted access.
Access can be denied for certain users. By default, a users shell is /bin/bash.
[root@server1 ~]# cat /etc/passwd | grep user1
user1:x:1002:1002:Example Comment:/var/user1:/bin/bash
The usermod -s command can be used to set a users default shell to /sbin/nologin (Red Hat) or /bin/false (Debian).
[root@server1 ~]# usermod -s /sbin/nologin user1
[root@server1 ~]# cat /etc/passwd | grep user1
user1:x:1002:1002:Example Comment:/var/user1:/sbin/nologin
Unlike /etc/nologin, this will deny access for both remote access and physical access. When user1 attempts to use the Terminal, some error message may be displayed.
[user1@server1 ~]#
This account is currently not available.
Did you find this article helpful?
If so, consider buying me a coffee over at 