
If you are not familiar with modules, check out Ansible - Getting Started with Modules.
The iptables module is used to modify iptables.
Important - This module will not save changes made to iptables. The changes will not persist when iptables is reloaded, or when the system that contains iptables is restarted. The shell or command modules can be used to save the change made to iptables.
Chains
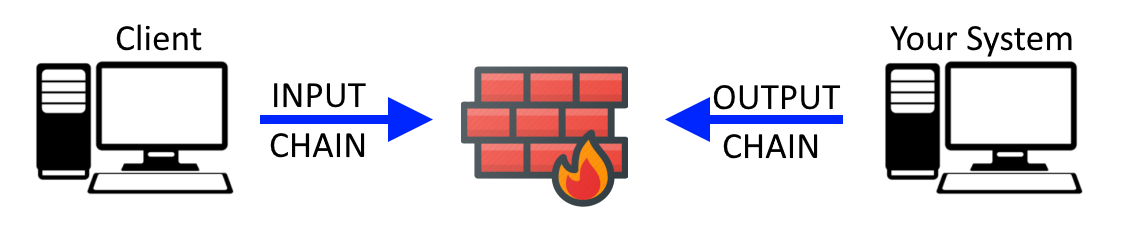
iptables uses chains to allow or deny certain types of requests. The default chains are:
- INPUT = Inbound request addressed to the host
- OUTPUT = Output request created by the host
- FORWARD = Neither addressed to the host nor created by the host. Forward is used to forward or route a packet to it's destination
Flushing Rules
Typically, after a clean install of iptables, iptables will already have default rules in place. The flush option is used to flush all rules. Refer to iptables - flush rules for a better understanding of flushing rules.
- name: "flush all iptables rules"
iptables:
flush: yes
Adding Rules
- If action is insert, the rule will be added at the beginning of the chain.
- If action is append, the rule will be added at the end of the chain.
If action not used, the default action will be append. This is important, because the order in which the rules are listed matters. iptables will read the rules from the top down, meaning the first rule listed will be read, then the second rule, and so on, until the last rule is read.
Allow lo interface
Typically, the first rule that is added is to allow traffic directed to the lo interface, which is the loopback interface, localhost, or 127.0.0.1.
- name: "allow connections on the lo interface on the input chain"
iptables:
chain: INPUT
in_interface: lo
jump: ACCEPT
Allow SSH
Often, the second rule that is added is to allow SSH connections. Assuming that you are using the default port 22 for SSH, the following command will allow SSH on the INPUT chain.
- Notice the match parameter contains a value of conntrack. conntrack stands for "connection tracking", which is the state of the SSH connection.
- Notice the ctstate parameter contains the NEW and ESTABLISHED values. ctstate stands for "connection state". ctstate is only used when the match: connstate parameter is used. NEW, ESTABLISHED, RELATED and INVALID are the possible states.
- Notice the source parameter contains 192.168.0.0/24, to only allow connections within the 192.168.0 subnet. This parameter is optional. If not used, connections will be allow from an source IP address.
The following will only allow NEW and ESTABLISHED SSH connections on the INPUT chain.
- name: "allow SSH on the input chain"
iptables:
chain: INPUT
protocol: tcp
destination_port: 22
match: conntrack
ctstate: NEW,ESTABLISHED
source: 192.168.0.0/24
jump: ACCEPT
And on the output chain.
- name: "allow SSH on the output chain"
iptables:
chain: OUTPUT
protocol: tcp
source_port: 22
match: conntrack
ctstate: ESTABLISHED
jump: ACCEPT
Allow ICMP ping
Before adding a rule to iptables to allow ICMP, it's important to recognize that there are different types of ICMP packets. Refer to iptables - allow ICMP to understand the different type of ICMP packets that can be specified. The following will allow any and all types of ICMP packets.
- name: "allow any and all types of ICMP packets on the input chain"
iptables:
chain: INPUT
protocol: icmp
jump: ACCEPT
Often, only ICMP echo requests are allow. The following command will allow only ICMP echo requests on the INPUT chain, so that the system running iptables can be pinged.
- Notice the icmp_type parameter contains a value of echo-request. Instead of using a value of echo-request, you could use a value of 8. This parameter accept either the numeric or literal name of the ICMP type.
- name: "allow ICMP echo requests on the input chain"
iptables:
chain: INPUT
protocol: icmp
icmp_type: echo-request
jump: ACCEPT
Drop
The last rule on the input chain should be drop, so that any connection not matching a rule in the chain is dropped. In other words, this is an explicit deny. Refer to iptables - drop rule for a better understanding of drop.
- name: "drop any connection that does not match a rule on the INPUT chain"
iptables:
chain: INPUT
jump: DROP
Inserting a rule on a specific line
Once you have the drop rule as the last rule, you would no longer use action: append, as this would append a rule after the drop rule. Recall that action: insert will insert a rule at the beginning of the chain. If you want to add a rule on a certain line, the rule_num parameter can be used. In this example, a rule to allow HTTP traffic on port 80 is inserted on line 4.
- name: "Allow HTTP on port 80"
iptables:
action: insert
chain: INPUT
protocol: tcp
destination_port: 80
rule_num: "4"
jump: ACCEPT
Saving changes
The iptables module will not save changes made to iptables. The changes will not persist when iptables is reloaded, or when the system that contains iptables is restarted. The iptables_state module can be used to save the change made to iptables.
- name: save iptables
community.general.iptables_state:
state: saved
path: /etc/sysconfig/iptables
Did you find this article helpful?
If so, consider buying me a coffee over at 