
This assumes you have already configured the aws command line tool. If not, check out my article on Getting Started with the AWS CLI.
The aws s3api get-bucket-ownership-controls command can be used to determine if your S3 Bucket is.
- BucketOwnerEnforced - only the owner of the S3 Bucket can list/read/write files in the S3 Bucket
- BucketOwnerPreferred - objects added to the S3 Bucket will be owned by the user adding the object to the S3 Bucket, however, if the Bucket Owner is set when uploading objects to the S3 Bucket, then the object will be owned by the Bucket Owner
- ObjectWriter - objects added to the S3 Bucket will be owned by the user adding the object to the S3 Bucket
~]$ aws s3api get-bucket-ownership-controls --bucket my-bucket-abc123
{
"OwnershipControls": {
"Rules": [
{
"ObjectOwnership": "BucketOwnerEnforced"
}
]
}
}
The aws s3api put-bucket-ownership-controls command can be used to set the S3 Bucket Ownership Control.
aws s3api put-bucket-ownership-controls \
--bucket my-bucket-abc123 \
--ownership-controls="Rules=[{ObjectOwnership=BucketOwnerPreferred}]"
If the Ownership Control is set to BucketOwnerEnforced, then the Access Control List (ACLs) cannot be changed (notice the Edit button is greyed out) and instead, the expectation is to use S3 Bucket Policies Instead.
- Amazon Web Services (AWS) - Get S3 Bucket Policy using AWS CLI
- Amazon Web Services (AWS) - Add Policy to an S3 Bucket using AWS CLI
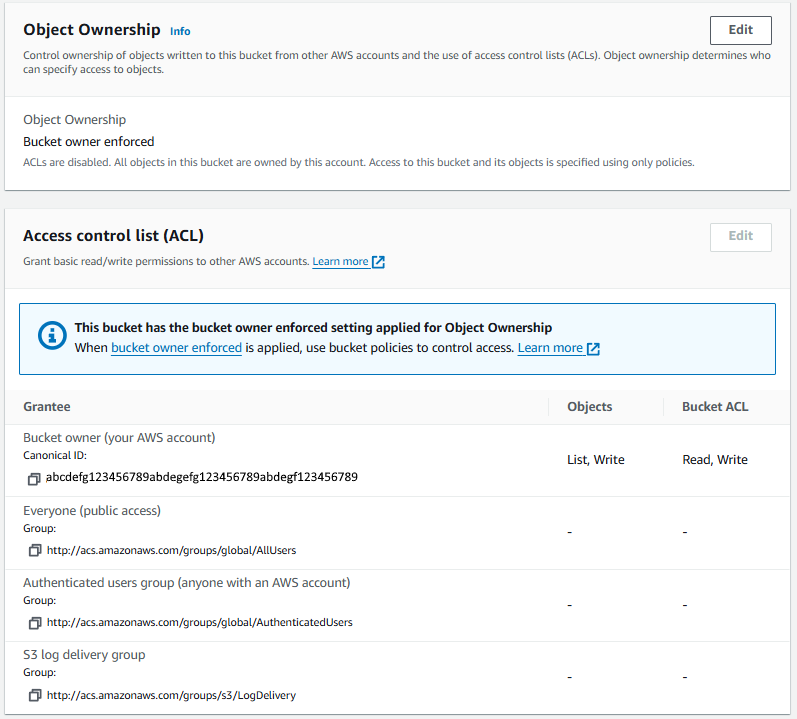
If the Ownership Control is set to BucketOwnerPreferred or ObjectWriter, then the Access Control List (ACLs) can be set.
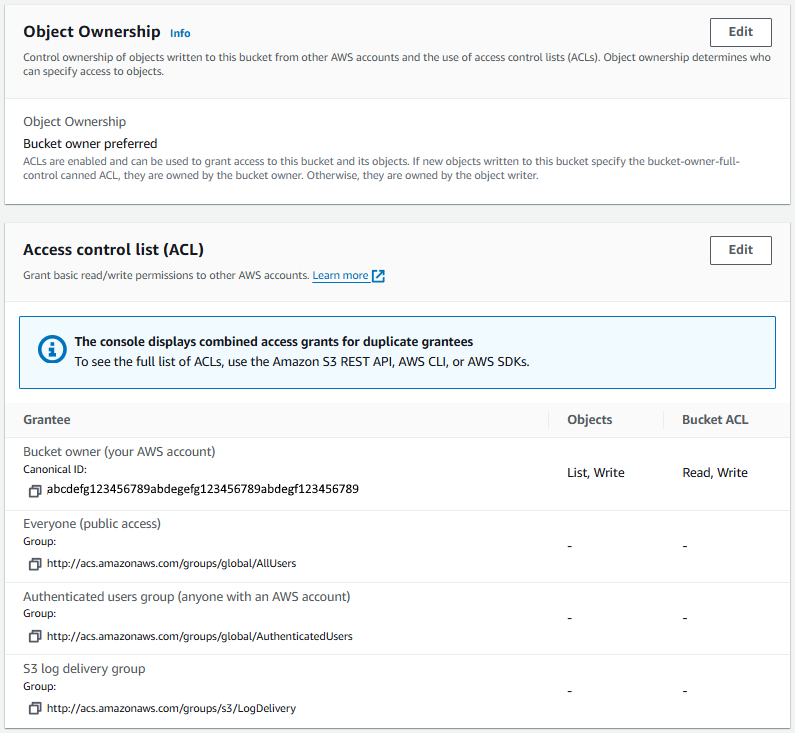
And the objects in the S3 Bucket will inherit the Ownership Control. In this example, index.html in the S3 Bucket inherited the Access Control List (ACL) from the S3 Bucket Ownership Control.
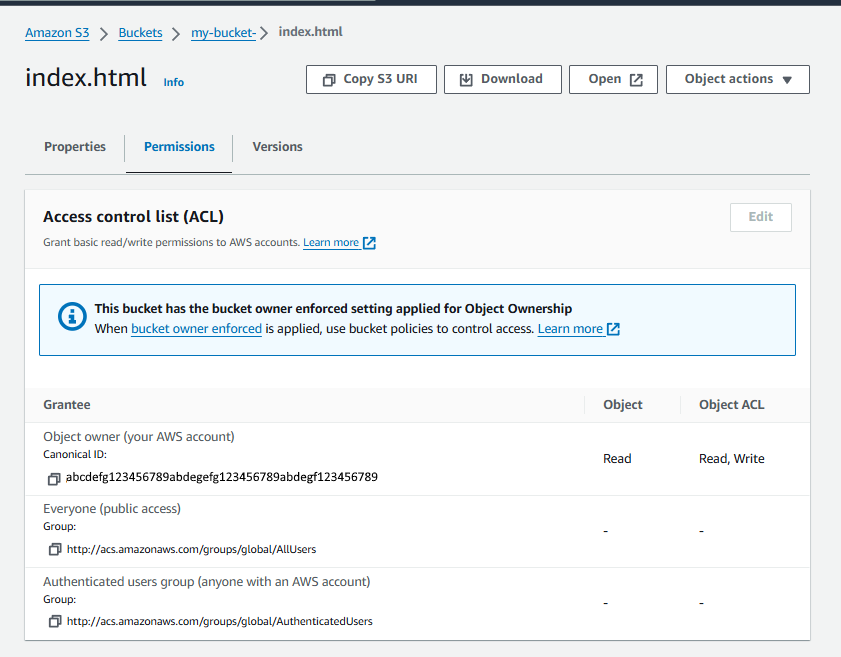
There are two similar (but unique) commands.
- aws s3api get-bucket-acl - to get the Access Control List (ACL) of the entire S3 Bucket
- aws s3api get-object-acl - to get the Access Control List (ACL) of a specific object in the S3 Bucket
By default, an S3 Bucket ACL will be set so that the Bucket Owner and list/read/write. This can also be seen with the aws s3api get-bucket-acl command.
The following permissions can be used:
- FULL_CONTROL
- READ
- READ_ACP
- WRITE
- WRITE_ACP
~]$ aws s3api get-bucket-acl --bucket my-bucket-abc123
{
"Owner": {
"DisplayName": "john.doe",
"ID": "ab0e0a12345678903a77c82240d5cb3fc41ff11cc312345678977a5f8e743743"
},
"Grants": [
{
"Grantee": {
"DisplayName": "john.doe",
"ID": "ab0e0a12345678903a77c82240d5cb3fc41ff11cc312345678977a5f8e743743",
"Type": "CanonicalUser"
},
"Permission": "FULL_CONTROL"
}
]
}
And likewise, each object in the S3 Bucket will inherit the Access Control List (ACL) from the S3 Bucket Ownership Control. The aws s3api get-object-acl command can be used to return the Access Control List (ACL) of a specific object in the S3 Bucket.
~]$ aws s3api get-object-acl --bucket my-bucket-abc123 --key index.html
{
"Owner": {
"DisplayName": "john.doe",
"ID": "ab0e0a12345678903a77c82240d5cb3fc41ff11cc312345678977a5f8e743743"
},
"Grants": [
{
"Grantee": {
"DisplayName": "john.doe",
"ID": "ab0e0a12345678903a77c82240d5cb3fc41ff11cc312345678977a5f8e743743",
"Type": "CanonicalUser"
},
"Permission": "FULL_CONTROL"
}
]
}
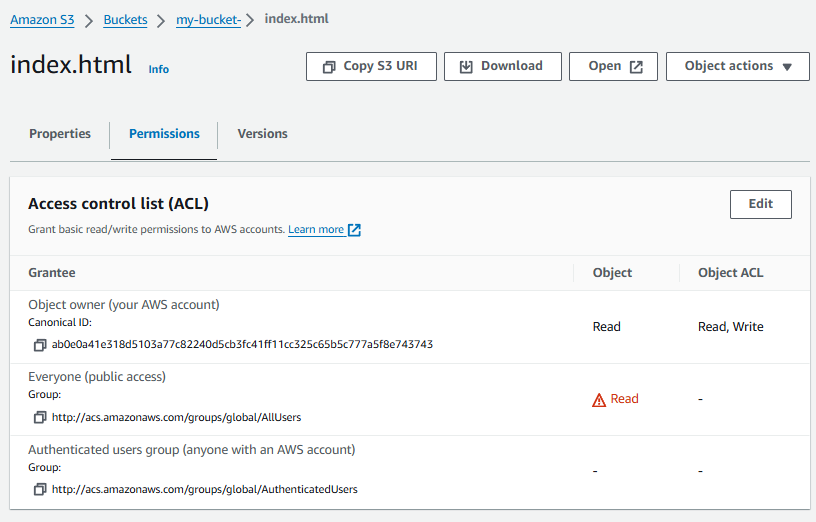
Likewise, in the AWS S3 Bucket console, the object should now have the Read ACL for AllUsers.
Did you find this article helpful?
If so, consider buying me a coffee over at 