
At a high level, setting up an Elastic Kubernetes Service (EKS) Cluster with Container Storage Interface (CSI) looks something like this.

Let's say you have the following files on your Terraform server.
├── required_providers.tf
├── elastic_kubernetes_service (directory)
│ ├── csi_driver.tf
│ ├── persistent_volumes.tf
│ ├── provider.tf
│ ├── storage_classes.tf
required_providers.tf will almost always have this.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
}
kubernetes = {
source = "hashicorp/kubernetes"
}
kubectl = {
source = "gavinbunney/kubectl"
}
helm = {
source = "hashicorp/helm"
}
}
}
Let's say provider.tf has the following. In this example, the "default" profile in /home/username/.aws/config and /home/username/.aws/credentials is being used. This assumes you have setup Terraform as described in Amazon Web Services (AWS) - Getting Started with Terraform.
data "aws_eks_cluster" "cluster" {
name = "my-cluster"
}
data "aws_eks_cluster_auth" "cluster_auth" {
name = "my-cluster"
}
provider "aws" {
alias = "default"
profile = "default"
region = "default"
}
provider "kubernetes" {
host = "https://123456789ABCDEFG123456789ABCDEFG.gr7.us-east-1.eks.amazonaws.com"
cluster_ca_certificate = base64decode(data.aws_eks_cluster.cluster.certificate_authority[0].data)
token = data.aws_eks_cluster_auth.cluster_auth.token
}
provider "kubectl" {
host = "https://123456789ABCDEFG123456789ABCDEFG.gr7.us-east-1.eks.amazonaws.com"
cluster_ca_certificate = base64decode(data.aws_eks_cluster.cluster.certificate_authority[0].data)
token = data.aws_eks_cluster_auth.cluster_auth.token
}
provider "helm" {
host = "https://123456789ABCDEFG123456789ABCDEFG.gr7.us-east-1.eks.amazonaws.com"
cluster_ca_certificate = base64decode(data.aws_eks_cluster.cluster.certificate_authority[0].data)
token = data.aws_eks_cluster_auth.cluster_auth.token
}
And csi_driver.tf could have something like this to create the Container Storage Interface (CSI) Driver.
resource "helm_release" "aws_efs_csi_driver" {
chart = "aws-efs-csi-driver"
name = "aws-efs-csi-driver"
namespace = "kube-system"
repository = "https://kubernetes-sigs.github.io/aws-efs-csi-driver/"
}
And storage_classes.tf could have something like this to create a Storage Class that uses the CSI Driver.
resource "kubernetes_storage_class" "csi" {
metadata {
name = "csi"
}
storage_provisioner = "efs.csi.aws.com"
}
And persistent_volumes.tf could have something like this to create a Persistent Volume that uses the CSI Driver and CSI Storage Class.
resource "kubernetes_persistent_volume" "csi_pv" {
metadata {
name = "csi-pv"
}
spec {
capacity = {
storage = "10M"
}
access_modes = ["ReadWriteMany"]
persistent_volume_source {
csi {
driver = "efs.csi.aws.com"
volume_handle = helm_release.aws_efs_csi_driver.id
}
}
storage_class_name = kubernetes_storage_class.csi.metadata.0.name
}
}
You may need to reissue the terraform init command.
terraform init
The terraform plan command can be used to see what Terraform will try to do.
terraform plan
The terraform apply command can be used to create or update the persistent volume.
terraform apply -auto-approve
kubectl get persistentvolumes can then be used to verify that the persistent volume exists. Most importantly, the STORAGECLASS should be csi.
~]$ kubectl get persistentvolumes
NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS REASON AGE
csi-pv 10M RWX Retain Available csi 12s
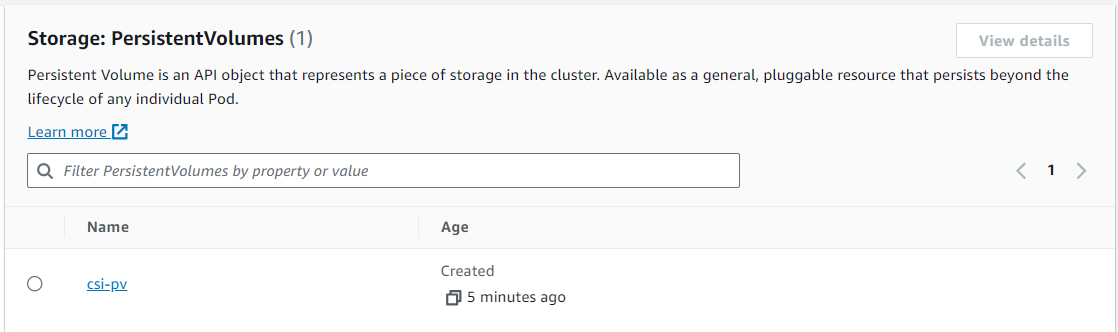
Or using the Elastic Kubernetes Services (EKS) console at Resources > Storage > Persistent Volumes.
Did you find this article helpful?
If so, consider buying me a coffee over at 