
If you are not familiar with AWS Application Load Balancers, check out my article FreeKB - Amazon Web Services (AWS) - Getting Started with Application Load Balancer (ALB).
Let's say you have two or more EC2 instances that are producing web apps. An application load balancer can be used to load balance the requests for the web app.
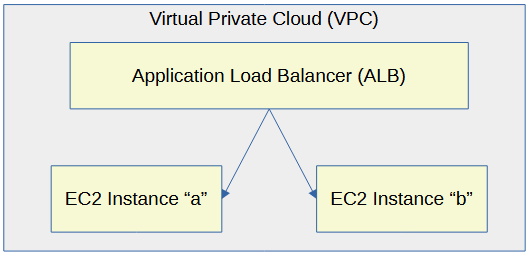
This assumes you have setup Terraform with the Amazon Web Services (AWS) provider. If not, check out my article Amazon Web Services (AWS) Getting Started with Terraform.
Let's say you have the following files on your Terraform server.
├── required_providers.tf
├── application_load_balancers (directory)
│ ├── acm_certificate.tf
│ ├── provider.tf
│ ├── listeners.tf
│ ├── load_balancers.tf
│ ├── target_groups.tf
│ ├── virtual_private_clouds.tf
required_providers.tf will almost always have this.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
}
}
}
Let's say provider.tf has the following. In this example, the "default" profile in /home/username/.aws/config and /home/username/.aws/credentials is being used. This assumes you have setup Terraform as described in Amazon Web Services (AWS) - Getting Started with Terraform.
provider "aws" {
alias = "default"
profile = "default"
region = "default"
}
And virtual_private_clouds.tf could have the following. Replace "my-vpc" with the name of your Virtual Private Cloud. Check out my articles list Virtual Private Cloud (VPC) using Terraform and list Virtual Private Cloud (VPC) Subnets using Terraform for more details on this.
data "aws_vpc" "my_vpc" {
filter {
name = "tag:Name"
values = ["my-vpc"]
}
}
data "aws_subnet" "my_aws_subnet" {
filter {
name = "tag:Name"
values = ["us-east-1a"]
}
}
And target_group.tf could have the following to create the application load balancer target group.
resource "aws_lb_target_group" "my-target-group" {
name = "my-target-group"
port = 443
protocol = "HTTPS"
vpc_id = data.aws_vpc.my_vpc.id
tags = {
Name = "my-target-group"
}
}
And acm_certificate.tf could have the following to create a SSL certificate with Subject Alternative Names (SAN) example.com and *.example.com. Check out my article create SSL certificate using Terraform for more details on this.
resource "aws_acm_certificate" "example_com_certificate" {
domain_name = "example.com"
validation_method = "DNS"
subject_alternative_names = ["example.com", "*.example.com"]
tags = {
environment = "staging"
}
lifecycle {
create_before_destroy = true
}
}
The List Elastic Load Balancer (ELB) SSL Policies using the AWS CLI command can be used to list the SSL policies that can be used by an Application Load Balancer.
~]# aws elbv2 describe-ssl-policies
[
{
"Name": "ELBSecurityPolicy-2016-08",
"SupportedLoadBalancerTypes": [
"application",
"network"
]
}
]
listeners.tf could have the following to create two Application Load Balancer Listeners, one that redirects HTTP to HTTPS and the other that forwards the HTTPS request onto a Target Group.
resource "aws_lb_listener" "https-listener" {
load_balancer_arn = aws_lb.application-load-balancer.arn
port = 443
protocol = "HTTPS"
ssl_policy = "ELBSecurityPolicy-TLS13-1-2-2021-06"
certificate_arn = aws_acm_certificate.example_com_certificate.arn
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.my-target-group.arn
}
tags = {
Name = "https-listener"
}
}
resource "aws_lb_listener" "redirect" {
load_balancer_arn = aws_lb.application-load-balancer.arn
port = 80
protocol = "HTTP"
default_action {
type = "redirect"
redirect {
port = "443"
protocol = "HTTPS"
status_code = "HTTP_301"
}
}
}
The terraform plan command can be used to see what Terraform will try to do.
terraform plan
And the terraform apply command can be used to create the Elastic Load balancer Target Group.
terraform apply
Did you find this article helpful?
If so, consider buying me a coffee over at 