
A trusted certificate is one that is purchased from a trusted CA (certificate authority) such as www.verisign.com. For non-production applications, a self-signed certificate can be used to encrypt the traffic.
Four files will be created:
| Type of file | Location |
|---|---|
| Private Key | /etc/pki/tls/private/example.key |
| Public Certificate | /etc/pki/tls/certs/example.crt |
| Certificate Signing Request (CSR) | /etc/pki/tls/example.csr |
| Certificate Authority (CA) | /etc/pki/tls/example.pem |
Use apt-get or yum to install crypto-utils.
[root@server1 ~]# apt-get install crypto-utils
[root@server1 ~]# yum install crypto-utils
The crypto-utils depends on the mod_ssl package.
[root@server1 ~]# apt-get install mod_ssl
[root@server1 ~]# yum install mod_ssl
Use the genkey command followed by the name of the public/private key pair.
[root@server1 ~]# genkey myKeypair
Select Next.
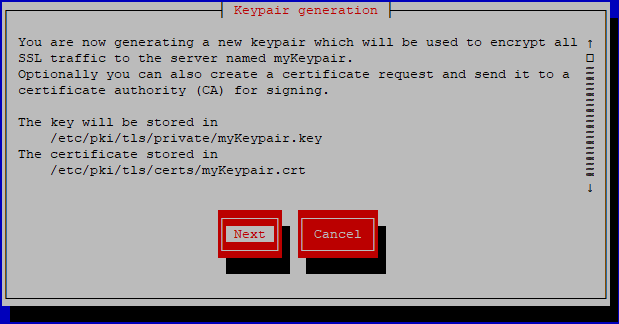
Select the key size and select next.

Wait for the random bit generate.
Wait for the random data to generate.
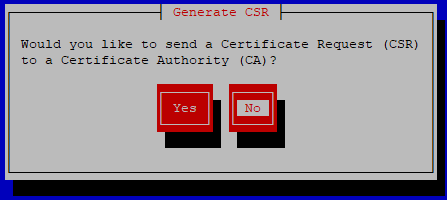
If creating a self-signed certificate, select No.
Select Next.
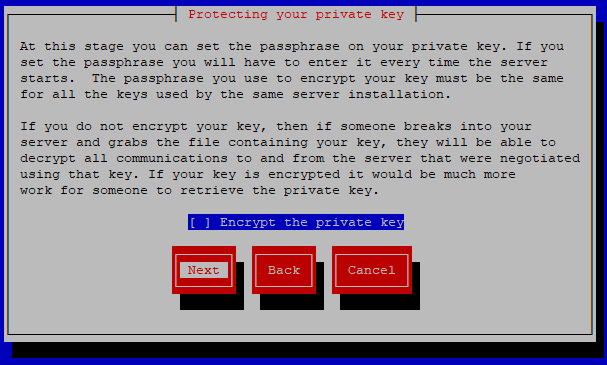
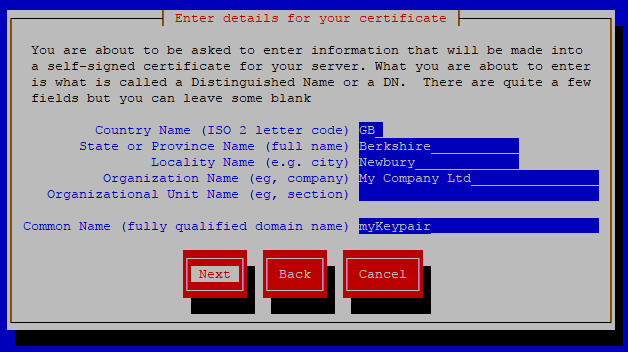
Complete the form and select Next.
The certificate will be in the /etc/pki/tls/certs/ directory, and the private key will be in the /etc/pki/tls/private directory.
Due to the sensitive nature of the private key, ensure that root owns the directory where the private key is stored. Also ensure that only root is allowed to read and write to the directory that contains the private key.
[root@server1 ~]# chown root:root /etc/pki/tls/private
[root@server1 ~]# chmod 400 /etc/pki/tls/private
Did you find this article helpful?
If so, consider buying me a coffee over at 