
There are two types of Policies.
- A identity-based policy is attached to a User, Group or Role.
- A resource-based policy is attached to a Resource, such as Simple Notification Service (SNS), S3 Bucket, EC2, et cetera
For example, let's say you used the aws iam create-user command to create a new user account.
aws iam create-user --user-name john.doe
The aws iam list-attached-user-policies command can be used to see that by default, no policies are attached to the newly created user.
~]$ aws iam list-attached-user-policies --user-name john.doe
{
"AttachedPolicies": []
}
Likewise, let's say you have an S3 Bucket that does not have a policy attached.
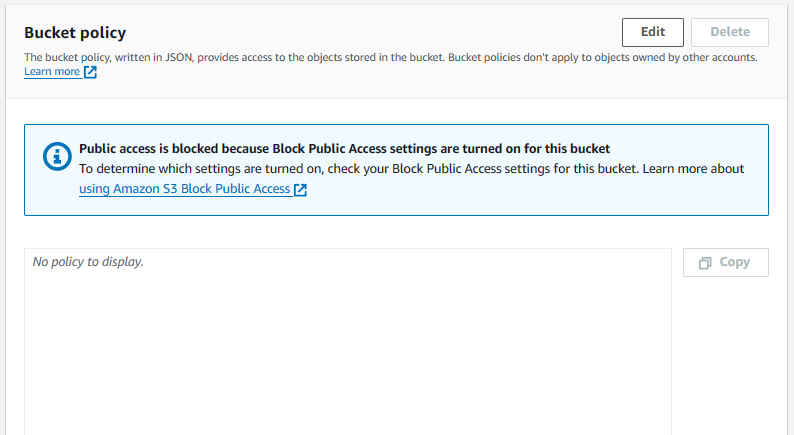
If we try to do something as the user, such as listing objects in one of our S3 Buckets using the aws s3api list-objects command, Access Denied should be returned.
~]$ aws s3api list-objects --bucket my-bucket-abc123 --profile johndoe
An error occurred (AccessDenied) when calling the ListObjects operation: Access Denied
Access Denied is being returned because:
- The User does NOT have an identity-based policy attached that allows the user to list objects in the Bucket
- The S3 Bucket does NOT have a resource-based policy attached that allows john.doe to list objects in the Bucket
Identity-Based Policy
Let's use the aws iam attach-user-policy command to attach the arn:aws:iam::aws:policy/AmazonS3FullAccess Policy so that john.doe can list objects in the S3 Buckets. Be aware that to do this, you will need to use some other profile that has the iam:AttachUserPolicy. For example, this could be done using the root profile which has AdministratorAccess. In this example, I used the root profile, which has AdministratorAccess.
aws iam attach-user-policy --user-name john.doe --policy-arn arn:aws:iam::aws:policy/AmazonS3FullAccess --profile root
Now john.doe can list the ojbects in the S3 Bucket.
~]$ aws s3api list-objects --bucket my-bucket-abc123 --profile johndoe
{
"Contents": [
{
"Key": "bar.txt",
"LastModified": "2024-04-16T01:32:17+00:00",
"ETag": "\"e65c918c98865ac528e2f2d0df0d8918\"",
"Size": 17,
"StorageClass": "STANDARD",
"Owner": {
"DisplayName": "jack.doe"
}
},
{
"Key": "foo.txt",
"LastModified": "2024-03-07T02:48:26+00:00",
"ETag": "\"bdb5c3c661744283fe90f16299244cd7\"",
"Size": 3,
"StorageClass": "STANDARD",
"Owner": {
"DisplayName": "jane.doe"
}
}
]
}
This is good. It totally works. But there is an issue with this. Let's say you have 100 Users. You would then have to attach the policy to all 100 User accounts. Ugh. This is where it probably makes more sense to go with a Resource-Based Policy.
Let's detach the arn:aws:iam::aws:policy/AmazonS3FullAccess policy from john.doe User account.
aws iam detach-user-policy --user-name john.doe --policy-arn arn:aws:iam::aws:policy/AmazonS3FullAccess
Resource-Based Policy
Let's say we have the following JSON which allows john.doe to perform any acction on the S3 Bucket. This still isn't ideal because then this policy would need to list all 100 Users, but this sure is better than having 100 separate policies attached to each individual user account.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:user/john.doe"
},
"Action": "s3:*",
"Resource": "arn:aws:s3:::my-bucket-abc123"
}
]
}
The aws s3api put-bucket-policy command can be used to attach the policy to the S3 Bucket. Be aware that to do this, you will need to use some other profile that has the iam:AttachResourcePolicy. For example, this could be done using the root profile which has AdministratorAccess. In this example, I used the root profile, which has AdministratorAccess.
aws s3api put-bucket-policy --bucket my-static-website-bucket-abc123 --policy file://policy.json
Now john.doe can list the ojbects in the S3 Bucket.
~]$ aws s3api list-objects --bucket my-bucket-abc123 --profile johndoe
{
"Contents": [
{
"Key": "bar.txt",
"LastModified": "2024-04-16T01:32:17+00:00",
"ETag": "\"e65c918c98865ac528e2f2d0df0d8918\"",
"Size": 17,
"StorageClass": "STANDARD",
"Owner": {
"DisplayName": "jack.doe"
}
},
{
"Key": "foo.txt",
"LastModified": "2024-03-07T02:48:26+00:00",
"ETag": "\"bdb5c3c661744283fe90f16299244cd7\"",
"Size": 3,
"StorageClass": "STANDARD",
"Owner": {
"DisplayName": "jane.doe"
}
}
]
}
Did you find this article helpful?
If so, consider buying me a coffee over at 