
This assumes you have already configured the aws command line tool. If not, check out my article on Getting Started with the AWS CLI.
Let's say you used the aws sns create-topic command to create a Simple Notification Service (SNS) Topic.
~]$ aws sns create-topic --name my-topic
{
"TopicArn": "arn:aws:sns:us-east-1:123456789012:my-topic"
}
And then you used the aws sns subscribe command to subscribe one of your Lambda Functions to the topic.
~]$ aws sns subscribe --topic-arn arn:aws:sns:us-east-1:123456789012:my-topic --protocol lambda --notification-endpoint arn:aws:lambda:us-east-1:123456789012:function:my-lambda-function
{
"SubscriptionArn": "arn:aws:sns:us-east-1:123456789012:my-topic:e68a4a47-ce56-48a5-865d-31f5920c4355"
}
And then you used the aws sns publish command to publish a message to the topic, which in this example should deliver the message to the Lambda Function.
~]$ aws sns publish --subject Hello --message World --topic-arn arn:aws:sns:us-east-1:123456789012:my-topic
{
"MessageId": "3756dea6-80cd-5e4a-ba9a-80a33a856481"
}
But the Lambda Function does not appear to have been invoked. You can configure the Simple Notification Service (SNS) Topic with Delivery Status Logging which can be helpful in viewing successful and failed deliveries.
Here is what you should see in the AWS console after configuring your Simple Notification Service (SNS) Topic with Delivery Status Logging.
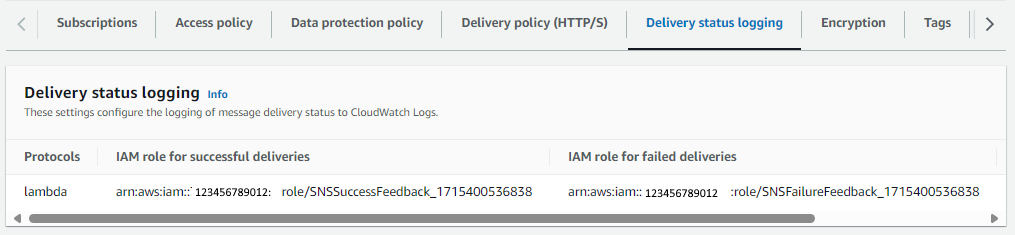
Then publish another message to your Topic.
aws sns publish --subject Hello2 --message World2 --topic-arn arn:aws:sns:us-east-1:123456789012:my-topic
And then over in CloudWatch, you should have a log group for the Success or Failure deliveries.
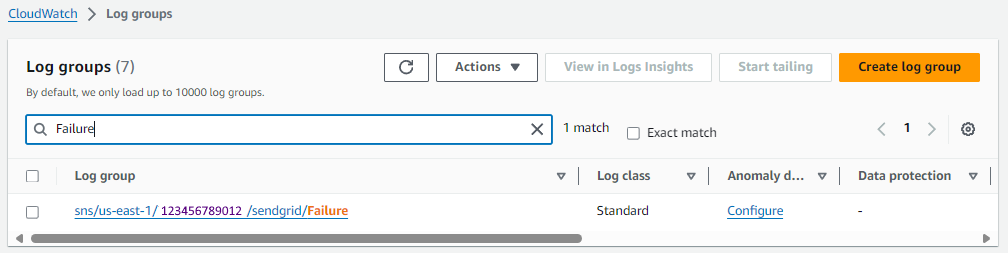
Or the aws logs describe-log-groups command can be used.
~]$ aws logs describe-log-groups
{
"logGroups": [
{
"logGroupName": "sns/us-east-1/123456789012/my-topic",
"creationTime": 1596419769060,
"metricFilterCount": 0,
"arn": "arn:aws:logs:us-east-1:123456789012:log-group:sns/us-east-1/123456789012/my-topic:*",
"storedBytes": 956
}
]
}
In this example, when I looked at the Failure, I saw the following.
User: sns.amazonaws.com is not authorized to perform: lambda:InvokeFunction on resource: arn:aws:lambda:us-east-1:123456789012:function:sendgrid because no resource-based policy allows the lambda:InvokeFunction action
In this scenario, the aws lambda add-permission command can be used to allow the SNS Topic to invoke the Lambda Function.
aws lambda add-permission \
--function-name sendgrid \
--source-arn arn:aws:sns:us-east-1:12346789012:my-topic \
--statement-id allow-sns-to-invoke-lambda \
--action "lambda:InvokeFunction" \
--principal sns.amazonaws.com
This command attaches the following IAM Policy to the Lambda Function, allowing the SNS Topic to invoke the Lambda Function.
{
"Version": "2012-10-17",
"Id": "default",
"Statement": [
{
"Sid": "allow-sns-to-invoke-lambda",
"Effect": "Allow",
"Principal": {
"Service": "sns.amazonaws.com"
},
"Action": "lambda:InvokeFunction",
"Resource": "arn:aws:lambda:us-east-1:123456789012:function:my-lambda-function",
"Condition": {
"ArnLike": {
"AWS:SourceArn": "arn:aws:sns:us-east-1:123456789012:my-sns-topic"
}
}
}
]
}
Did you find this article helpful?
If so, consider buying me a coffee over at 