
Let's say you have a Lambda Function in the us-east-1 region and when a request is received from a system in the USA, the response time is milliseconds, whereas when a request is received from a system in Asia, the response time is much slower, perhaps a few seconds. That's no good. Lambda@EDGE is meant to resolve this issue. Lambda@EDGE is used so that Lambda Functions are invoked in an AWS Region that is geographically close to the user or system invoking the Lambda Function.
Lambda@EDGE is part of CloudFront. Since this is just meant to be a simple Getting Started article, lets create a CloudFront Distributions with public S3 Bucket and verify you can retrieve the file in your S3 Bucket using the CloudFront Distribution URL.
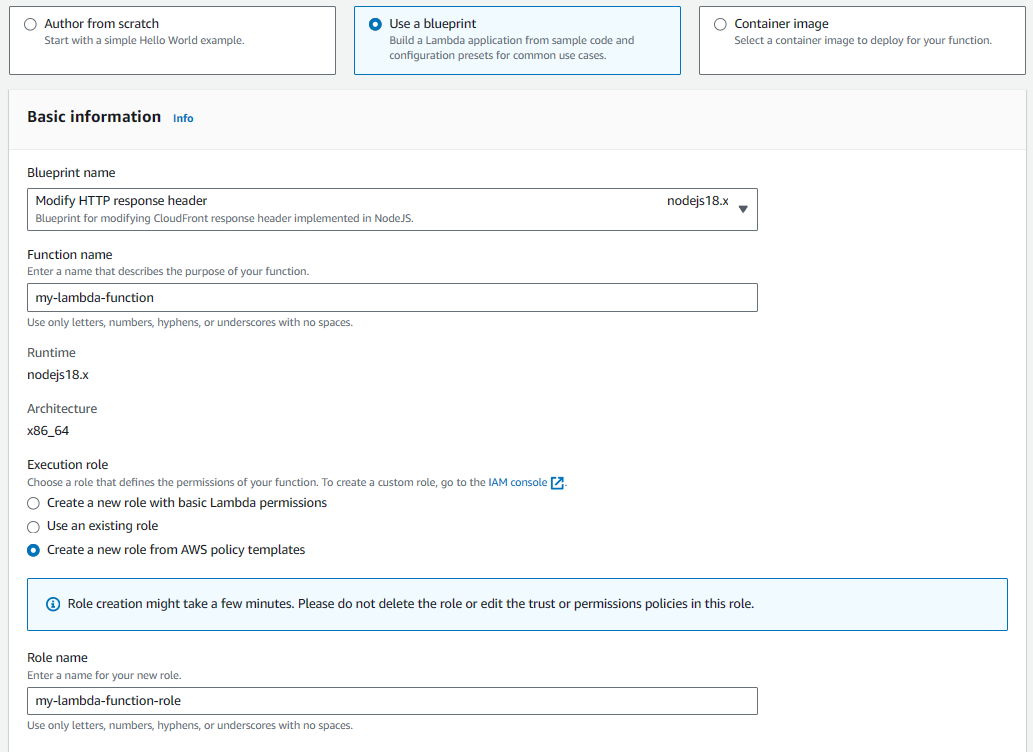
Next let's create a Lambda Function using the Modify HTTP response header blueprint. This Blueprint has the various pieces that are needed for the Lambda Function to work with CloudFront.
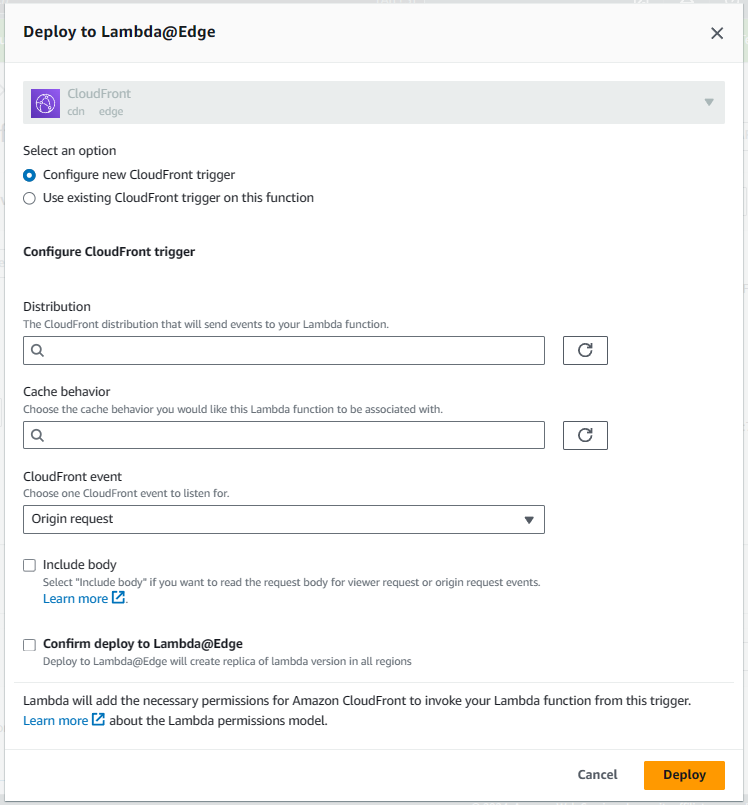
When prompted to Deploy to Lambda@EDGE, let's go with cancel because we are going to modify the Lambda Function.
On the Code tab of your Lambda Function, replace the code with the following and select Deploy.
'use strict';
exports.handler = (event, context, callback) => {
const response = event.Records[0].cf.request;
const headers = response.headers;
headers['strict-transport-security'] = [{key: 'Strict-Transport-Security', value: 'max-age= 63072000; includeSubdomains; preload'}];
headers['content-security-policy'] = [{key: 'Content-Security-Policy', value: "default-src 'none'; img-src 'self'; script-src 'self'; style-src 'self'; object-src 'none'"}];
headers['x-content-type-options'] = [{key: 'X-Content-Type-Options', value: 'nosniff'}];
headers['x-frame-options'] = [{key: 'X-Frame-Options', value: 'DENY'}];
headers['x-xss-protection'] = [{key: 'X-XSS-Protection', value: '1; mode=block'}];
headers['referrer-policy'] = [{key: 'Referrer-Policy', value: 'same-origin'}];
callback(null, response);
};
Now at Configuration > Triggers > Add Trigger notice this says
"Adding a CloudFront trigger to your function allows it to be executed at global AWS locations close to end users"
This is the piece that gets the Lambda Function to be geographically close to end users. Click the Deploy to Lambda@Edge button.
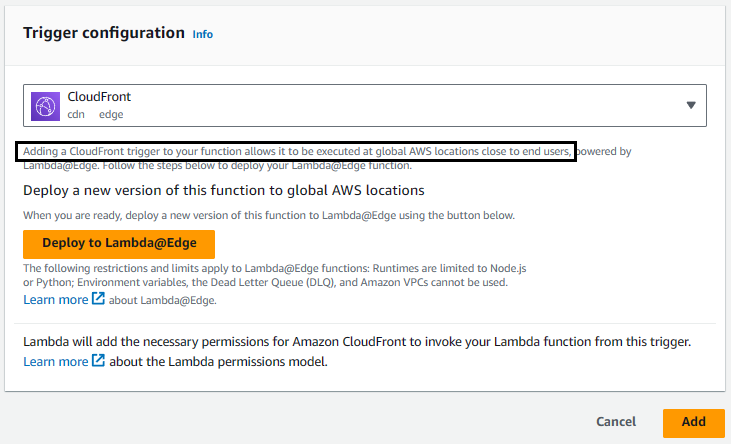
In the Deploy to Lambda@Edge pop-up box, select your CloudFront Distribution and change CloudFront event to Origin response and select Deploy. This displays the function worldwide! Wow!
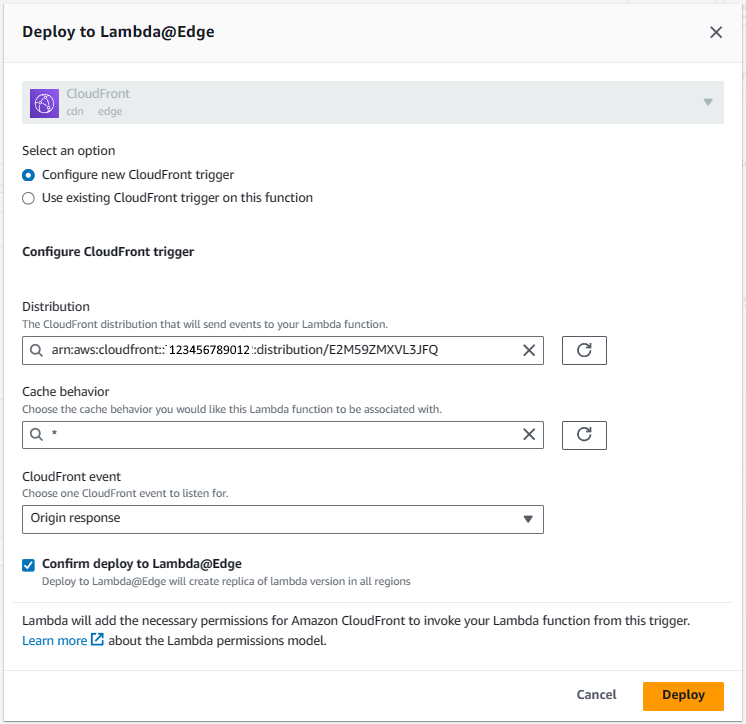
And your CloudFront Distribution should now be displayed in your Lambda Triggers. Check out my article Amazon Web Services (AWS) - Getting Started with Lambda Trigger for more details on Lambda Triggers.
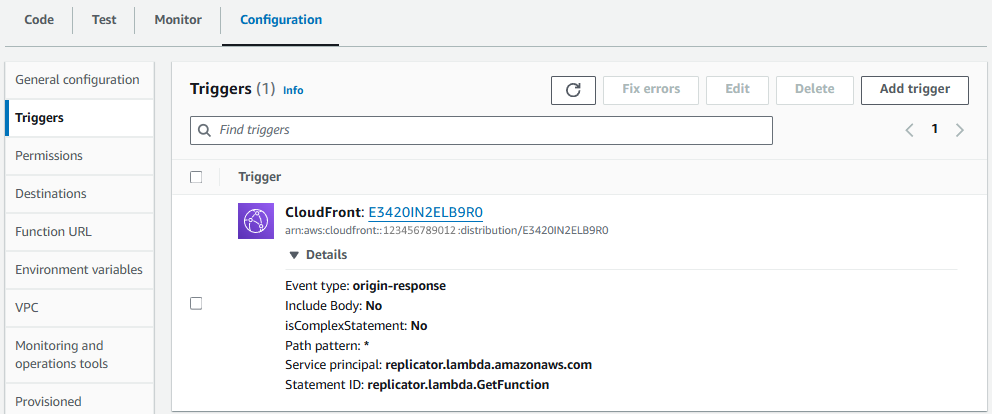
Your CloudFront Distribution should updated to Deploying and it should take a few minutes for the deploy to complete.
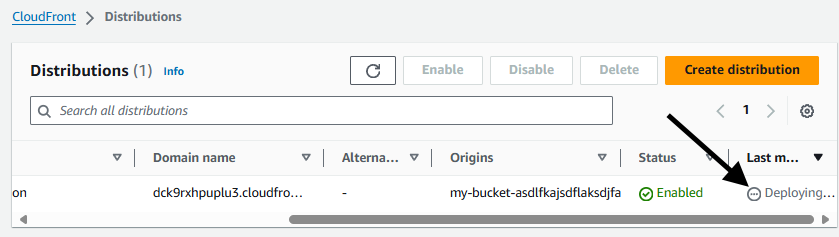
Once your CloudFront Distribution Last modified datetime has updated, this means the Lambda@Edge function should have been deployed worldwide. This blows my mind!
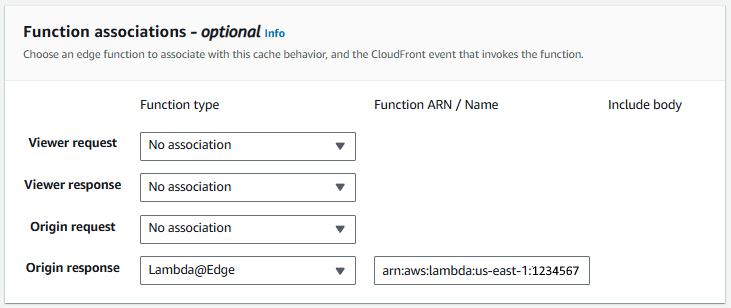
And if you select your CloudFront Distribution > Behaviors > Edit you should see your Lambda@Edge in Function associations.
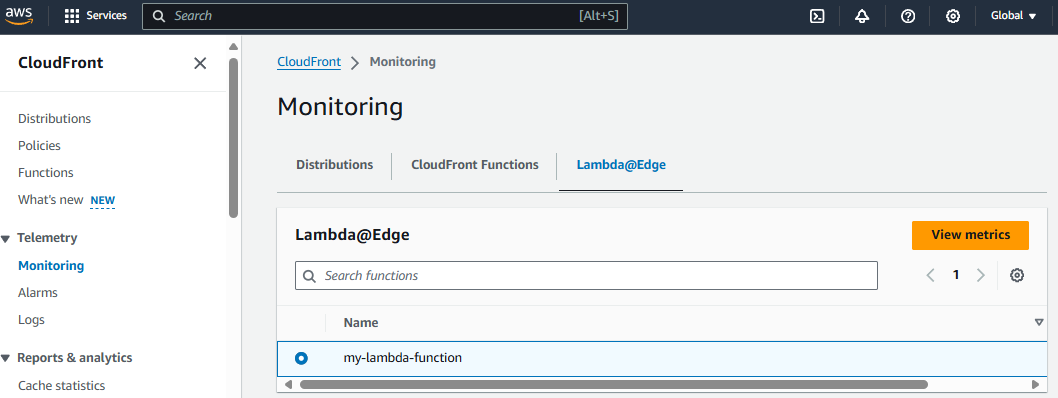
And at Monitoring in your CloudWatch Distribution, your Lambda@Edge function should be listed.
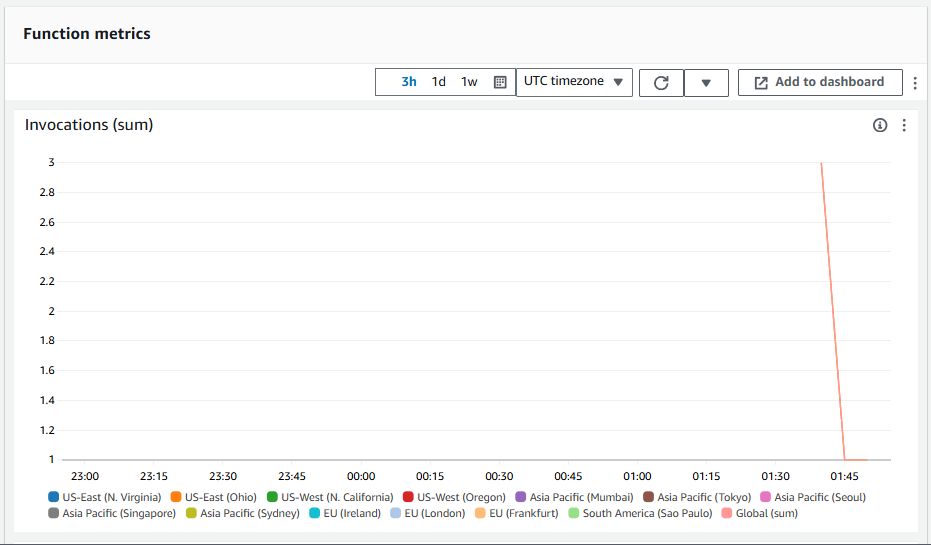
And in Monitoring you should be able to see the region where requests are coming from. That's neat!
Did you find this article helpful?
If so, consider buying me a coffee over at 