
An Internet Gateway is used to route traffic onto the Internet. This typically means configuring the Route Table in a Subnet with an Internet Gateway Route so that EC2 instances in a Virtual Private Cloud (VPC) can talk to systems outside of their VPC.
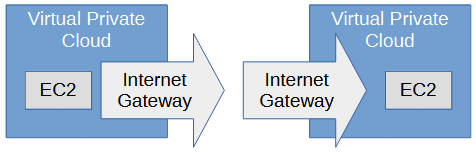
For example, let's create VPCs.
- foo-vpc
- bar-vpc
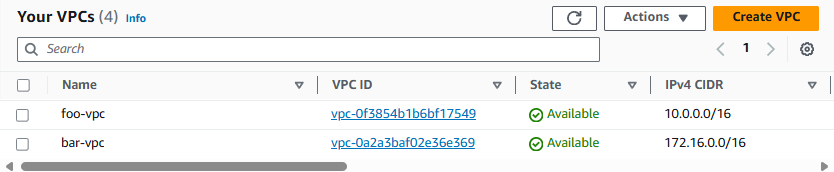
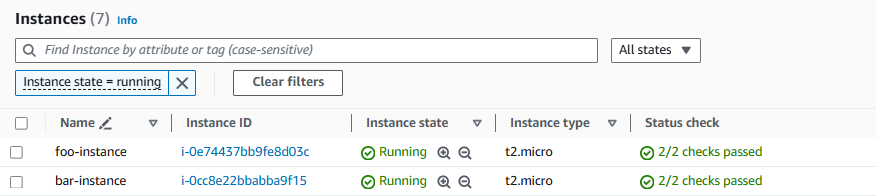
And let's create an EC2 instance in foo-vpc and bar-vpc. At this point, there will be no way to SSH onto either EC2 instance, because you don't have a route that can be used to reach either EC2 instance.
Because, by default, a VPC will only have a local route and no Internet Gateway.
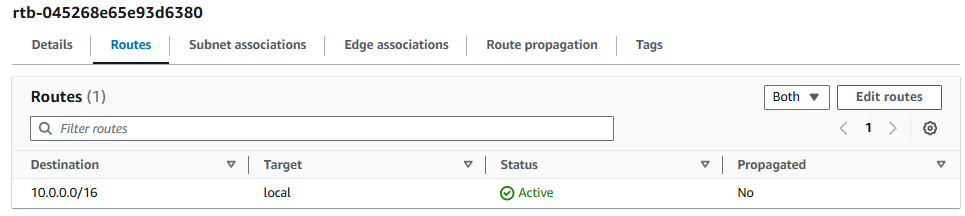
So let's create an Internet Gateway for foo-vpc and bar-vpc. By default, the Internet Gateways will not be attached to any VPCs.
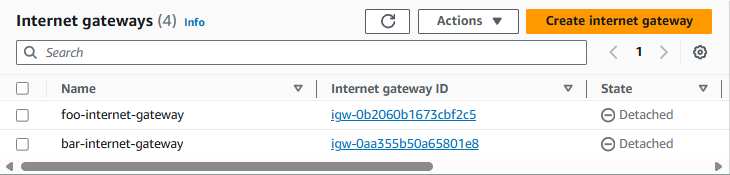
Let's attach the foo-internet-gateway to foo-vpc.
aws ec2 attach-internet-gateway --internet-gateway-id igw-0b2060b1673cbf2c5 --vpc-id vpc-0f3854b1b6bf17549
And attach the bar-internet-gateway to bar-vpc.
aws ec2 attach-internet-gateway --internet-gateway-id igw-0aa355b50a65801e8 --vpc-id vpc-0a2a3baf02e36e369
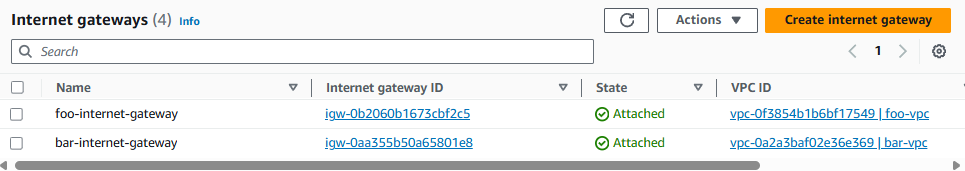
Now each Internet Gateway should be attached to each VPC.
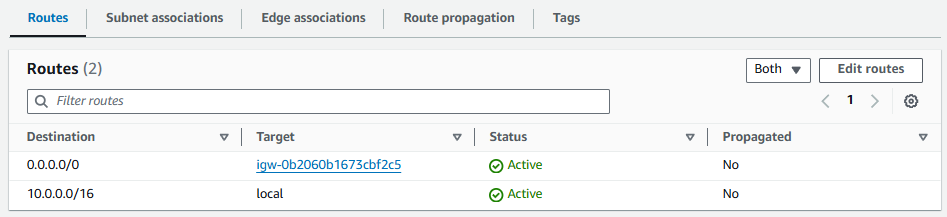
Let's update the Route Table being used by foo-vpc to have a route to the foo-internet-gateway.
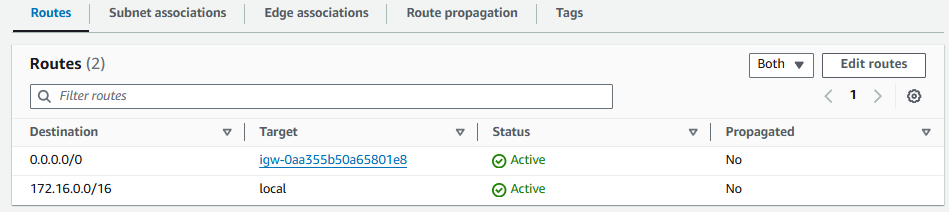
And let's update the Route Table being used by bar-vpc to have a route to the bar-internet-gateway.
And update the Security Group being used by each EC2 instance to allow SSH connections from your local public IP address. In this example, my local public IP address was 65.17.88.90. You would instead use your local public IP address.
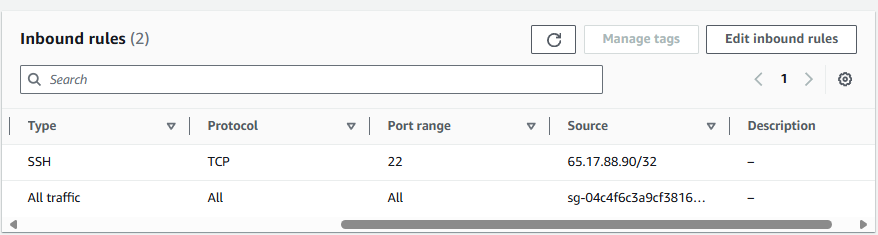
And you should now be able to SSH onto the EC2 instance in foo-vpc. Sweet!
Using username "ec2-user".
Authenticating with public key "aws"
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Wed May 1 00:12:12 2024 from 65.17.88.90
[ec2-user@ip-10-0-4-185 ~]$
Did you find this article helpful?
If so, consider buying me a coffee over at 