
Cognito is an Amazon Web Services (AWS) service that is often used for authenticating mobile users. The first step in setting up Cognito is to Create a User Pool. In the AWS Cognito console, let's start by selecting Create user pool.
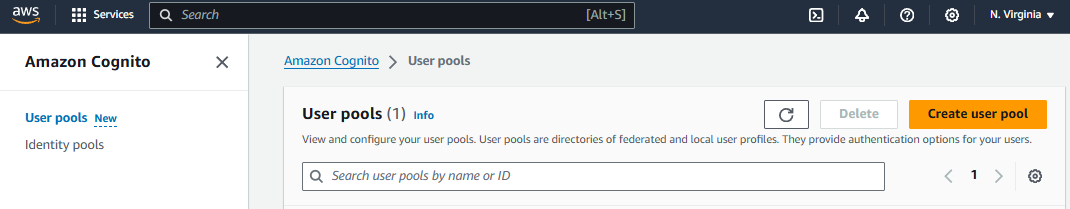
Since this is just meant to be a simple Getting Started article, we are going to go with the simplist setup just for proof of concept. Let's go with Cognito user pool and Email.
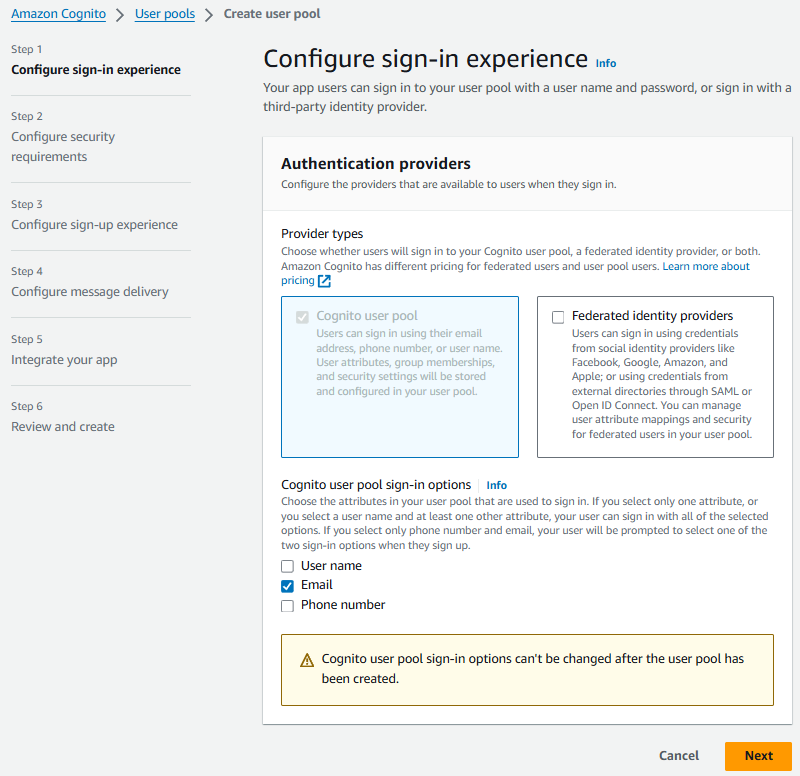
At the next page let's go with No MFA and select next.
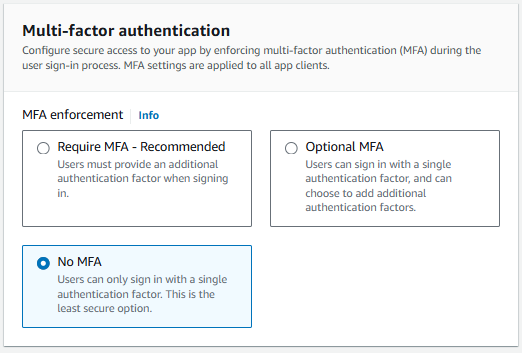
At the next page let's select one (or more attributes) and select next.
And let's go with Send email with Cognito as it's a much easier setup and select next.
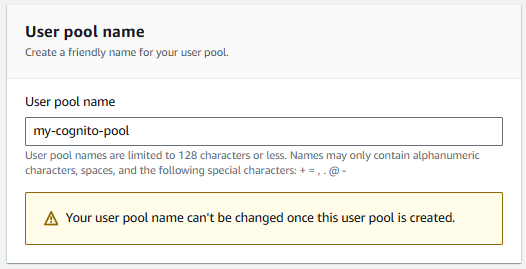
Let's give the pool a name.
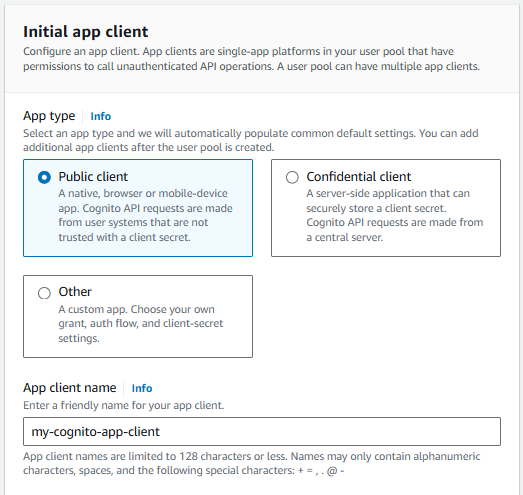
And let's go with a Public app client and give the app client a name and select next.
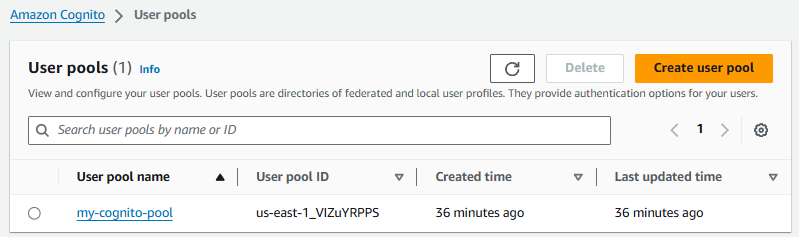
And then Create user pool. Nice. The User Pool has been created. Let's select the User Pool.
On the App Integration tab let's select Actions > Create Cognito domain.
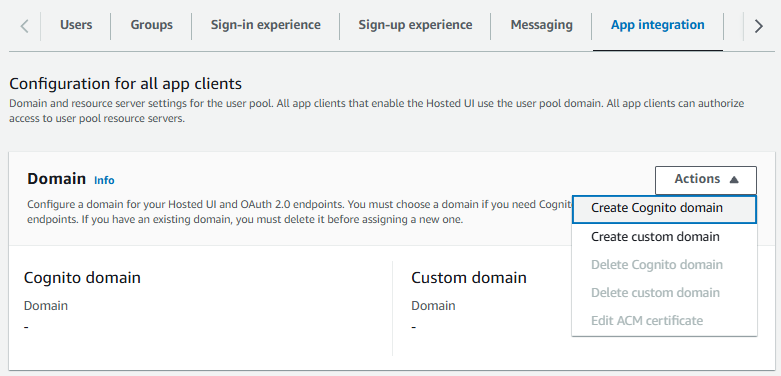
And let's enter some random string to create a unique domain name. I generated a random UUID.
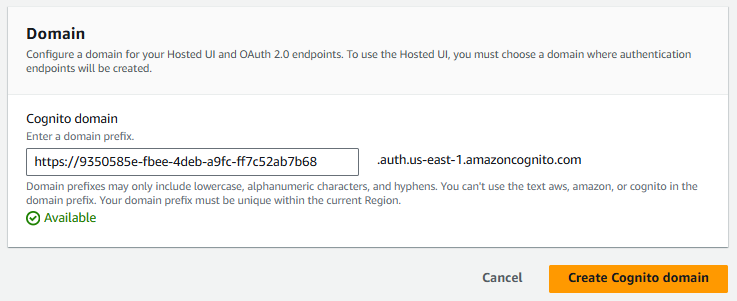
Still on the App Integration tab let's select your app client.
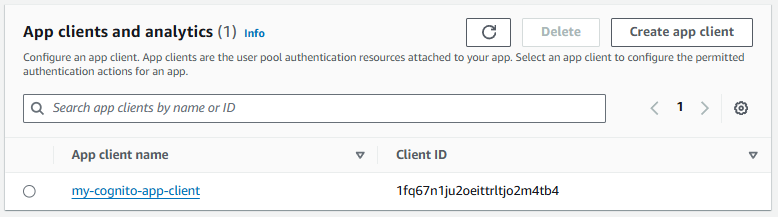
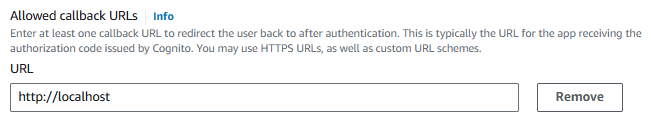
And let's add a callback URL.This will be the URL that folks will be redirected to after authenticating.
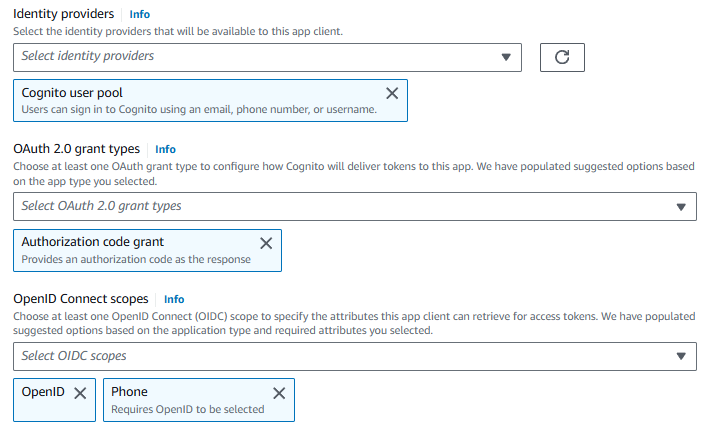
And since this is just meant to be a super simple Getting Started article, let's go with our Cognito user pool as the Identity Provider (IdP) with an authorization code for the OAuth 2.0 grant type and for this demo I'm using OpenID and Phone for the connect scopes.
All righty. Let's see if this works. In a browser let's go to https://<your cognito domain>.auth.us-east-1.amazoncognito.com/login?response_type=code&client_id=<your_app_client_id>&redirect_uri=<your_callback_url>. In this example, I would go to https://9350585e-fbee-4deb-a9fc-ff7c52ab7b68.auth.us-east-1.amazoncognito.com/login?response_type=code&client_id=1fq67n1ju2oeittrltjo2m4tb4&redirect_uri=http://localhost and, fingers crossed, you should be presented with a basic auth form. Awesome!
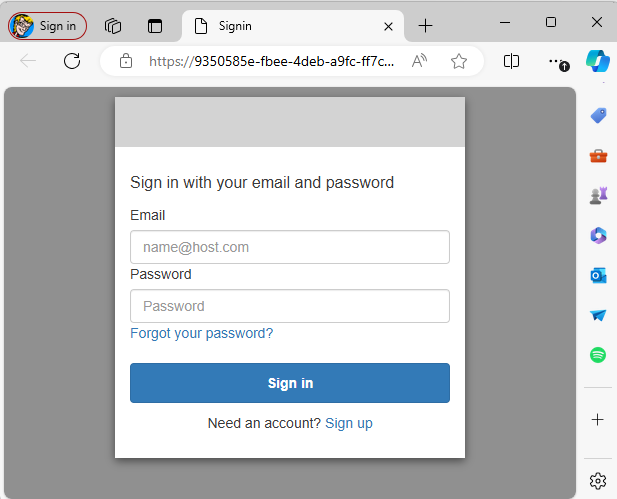
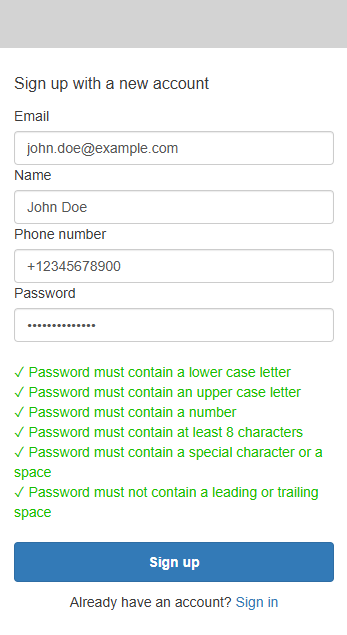
SInce we just set this up we don't have any users. Let's select Sign up and create a dummy user account.
Since this is a dummy email, the verification email would have been sent to the dummy email so we don't have a way to confirm the account via email.
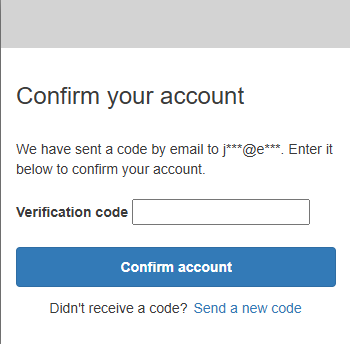
Not to worry. On the Users tab in the Cognito console we should see the user account we just created as Unconfirmed.
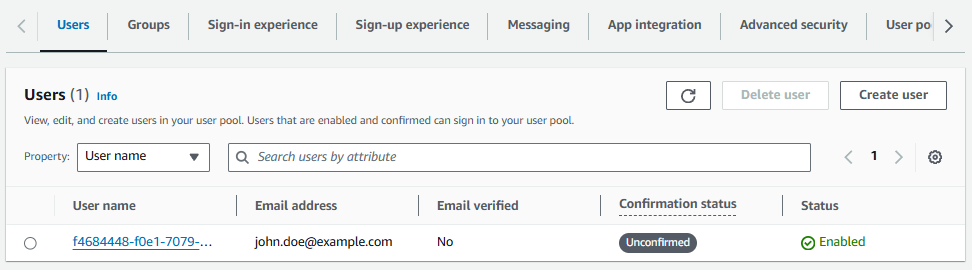
Let's select the users account and select Actions > Confirm account.
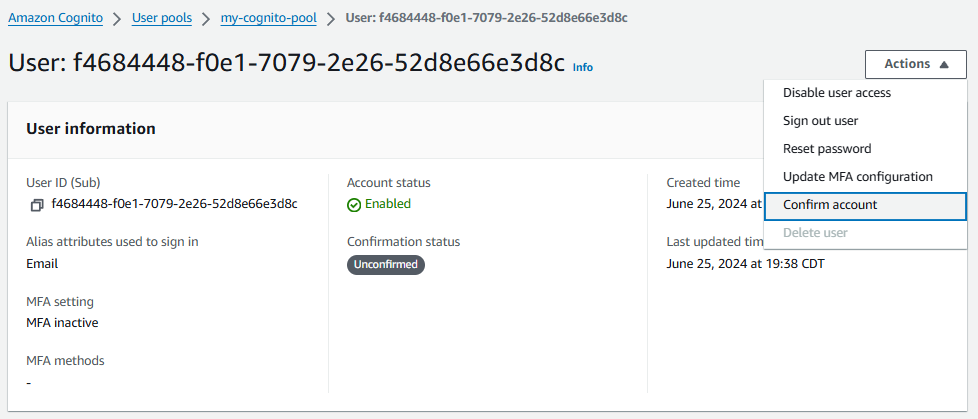
Let's go back to https://<your cognito domain>.auth.us-east-1.amazoncognito.com/login?response_type=code&client_id=<your_app_client_id>&redirect_uri=<your_callback_url> (https://9350585e-fbee-4deb-a9fc-ff7c52ab7b68.auth.us-east-1.amazoncognito.com/login?response_type=code&client_id=1fq67n1ju2oeittrltjo2m4tb4&redirect_uri=http://localhost in this example) and Sign in.
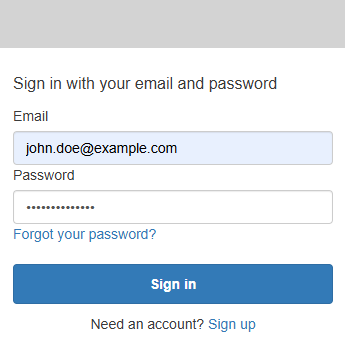
And if the authentication is successful we should be redirected to the callback URL which is http://localhost in this example with a "code". Don't worry if the browser shows something like "can't reach this page". Of course the browser can't reach http://localhost. We are just used this callback URL for proof of concept to see that we were able to authenticate and get a UUID code returned, an auth token.
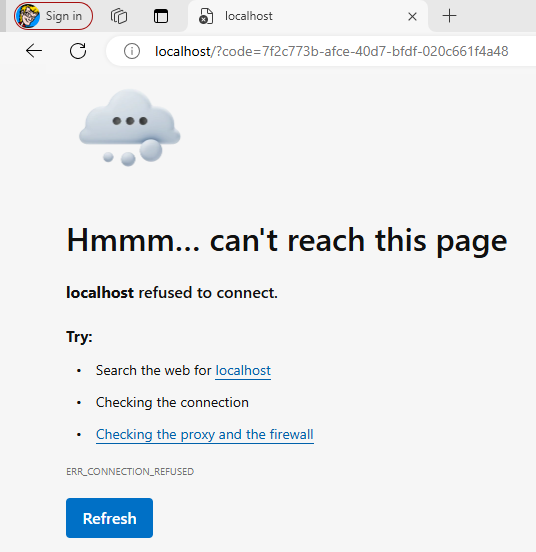
Cool. But what do we do with the token? Let's try to authenticate using the aws cognito-idp initiate-auth command.
aws cognito-idp initiate-auth \
--region us-east-1 \
--auth-flow USER_PASSWORD_AUTH \
--client-id 1fq67n1ju2oeittrltjo2m4tb4 \
--auth-parameters USERNAME=john.doe@example.com,PASSWORD=itsasecret\!1A
Since we have not setup our app integration to allow basic auth (username/password) something like this should be returned.
An error occurred (InvalidParameterException) when calling the InitiateAuth operation: USER_PASSWORD_AUTH flow not enabled for this client
Back in the Cognito App Integration we should see that indeed ALLOW_USER_PASSWORD_AUTH is not listed.
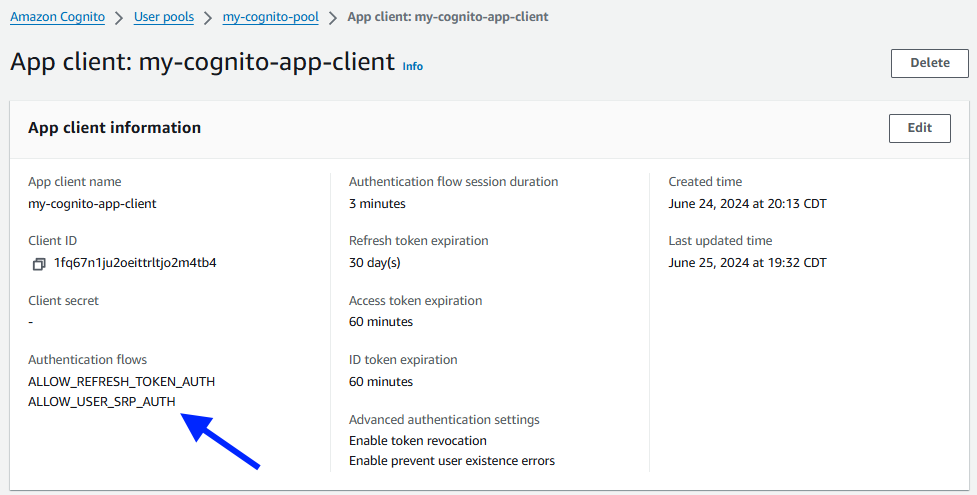
Let's select Edit and add ALLOW_USER_PASSWORD_AUTH.
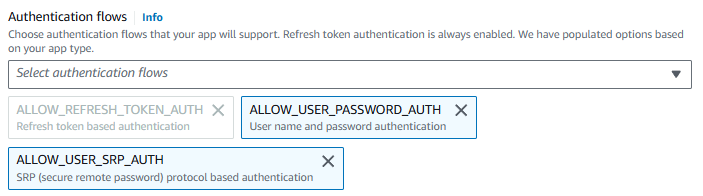
Let's try again to authenticate using the aws cognito-idp initiate-auth command and this time we should get a token returned. Nice!
~]$ aws cognito-idp initiate-auth --region us-east-1 --auth-flow USER_PASSWORD_AUTH --client-id 1fq67n1ju2oeittrltjo2m4tb4 --auth-parameters USERNAME=john.doe@example.com,PASSWORD=itsasecret\!1A
{
"ChallengeParameters": {},
"AuthenticationResult": {
"AccessToken": "eyJraWQiOiJSbitJUXFheX...T5h02w",
"ExpiresIn": 3600,
"TokenType": "Bearer",
"RefreshToken": "eyJjdHkiOiJKV1Qi...GKlS4GaA",
"IdToken": "eyJraWQiOiJ4N...IvQwcCxsWL9_9w"
}
}
Did you find this article helpful?
If so, consider buying me a coffee over at 