
This assumes:
- You have an ArgoCD server up and running. If not, check out my article Install Red Hat OpenShift GitOps Operator using the console (Argo CD)
- You have installed the ArgoCD CLI.
- You are able to log into ArgoCD using the CLI. If not, check out my article Log into ArgoCD using the CLI on OpenShift
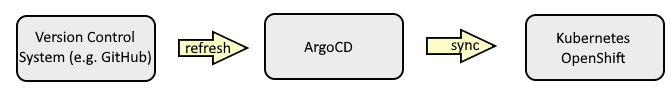
ArgoCD sits between your version control system (such as GitHub) and your Kubernetes or OpenShift clusters and is used to create resources (such as deployments, pods, services, routes, config maps and secrets) in a particular namespace in your Kubernetes or OpenShift clusters. Almost always, this means you will have YAML files for your various Kubernetes or OpenShift resources in your version control system, such as YAML files for your Kubernetes or OpenShift deployments, YAML files for your Kubernetes or OpenShift secrets, YAML files for your Kubernetes or OpenShift services, et cetera, and ArgoCD will create the corresponding resources in your Kubernetes or OpenShift clusters using the YAML files in your version control system. ArgoCD will also ensure the resources on your Kubernetes or OpenShift clusters remain in sync with their corresponding YAML files in your version control system.
The argocd repo list command can be used to list the repo's you have added to ArgoCD.
~]$ argocd repo list
TYPE NAME REPO INSECURE OCI LFS CREDS STATUS MESSAGE PROJECT
git argocd-example-apps https://github.com/argoproj/argocd-example-apps false false false false Successful default
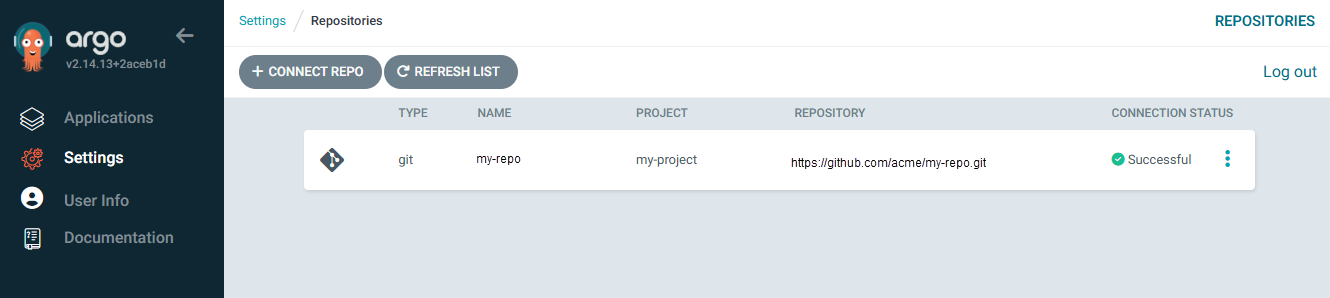
Or in the ArgoCD console at Settings > Repositories.
Or on the Kubernetes or OpenShift cluster that ArgoCD is in the kubectl (Kubernetes) or oc (OpenShift) get secret command can be used to list the secrets in the namespace ArgoCD is in. There should be a secret for each repo that has been added to ArgoCD.
~]$ oc get secrets --namespace openshift-gitops
NAME TYPE DATA AGE
repo-321785470 Opaque 4 24d
repo-38486771 Opaque 6 55d
The kubectl (Kubernetes) or oc (OpenShift) get secret command with the --output jsonpath and base64 --decode command can be used to display the name of the repo in ArgoCd, the ArgoCD project that the repo is configured to use, the repo type, the repo URL,
~]$ oc get secret repo-38486771 --namespace openshift-gitops --output jsonpath="{.data.name}" | base64 --decode
bar
~]$ oc get secret repo-38486771 --namespace openshift-gitops --output jsonpath="{.data.project}" | base64 --decode
default
~]$ oc get secret repo-38486771 --namespace openshift-gitops --output jsonpath="{.data.type}" | base64 --decode
git
~]$ oc get secret repo-38486771 --namespace openshift-gitops --output jsonpath="{.data.url}" | base64 --decode
https://github.com/foo/bar
Or on the Kubernetes or OpenShift cluster that ArgoCD is in the kubectl (Kubernetes) or oc (OpenShift) exec command can be used to run the argocd cluster list command in the ArgoCD server pod. It is noteworthy that by default the argocd login command will create the hidden .config file in the root directory of the operating system /.config and only root has permission to create files in the root directory of the operating system thus the --config /home/argocd/.config option is used so that the hidden .config file is create in our users home directory.
~]$ SERVER_POD=$(oc get pod --namespace openshift-gitops --selector=app.kubernetes.io/name=openshift-gitops-server --output custom-columns=POD:.metadata.name --no-headers)
~]$ ADMIN_PASSWD=$(oc get secret openshift-gitops-cluster --namespace openshift-gitops --output jsonpath='{.data.admin\.password}' | base64 --decode)
~]$ URL=$(oc get routes --namespace openshift-gitops --selector=app.kubernetes.io/name=openshift-gitops-server --output jsonpath="{.items[*].spec.host}")
~]$ oc exec $SERVER_POD --namespace openshift-gitops -- /bin/bash -c "argocd login --username admin --password $ADMIN_PASSWD $URL:443 --insecure --grpc-web --config /home/argocd/.config; argocd repo list --server $URL:443 --insecure --grpc-web --config /home/argocd/.config"
'admin:login' logged in successfully
TYPE NAME REPO INSECURE OCI LFS CREDS STATUS MESSAGE PROJECT
git argocd-example-apps https://github.com/argoproj/argocd-example-apps false false false false Successful default
Likewise the argocd repo get <repo url> command can be used to return a specific repo.
~]$ argocd repo get https://github.com/argoproj/argocd-example-apps
TYPE NAME REPO INSECURE OCI LFS CREDS STATUS MESSAGE PROJECT
git argocd-example-apps https://github.com/argoproj/argocd-example-apps false false false false Successful default
The --output json flag can be used to display output as JSON instead of YAML.
~]$ argocd repo get https://github.com/argoproj/argocd-example-apps --output json
{
"repo": "https://github.com/argoproj/argocd-example-apps",
"connectionState": {
"status": "Successful",
"message": "",
"attemptedAt": "2024-12-19T02:43:04Z"
},
"type": "git",
"name": "argocd-example-apps",
"project": "default"
}
Likewise, the kubectl (Kubernetes) or oc (OpenShift) get secrets command can be used to list the secrets in the namespace ArgoCD is installed in, which is typically argocd or openshift-gitops and there should be a secret for each repository you have added to ArgoCd.
~]$ oc get secrets --namespace openshift-gitops | grep -i repo
repo-321785470 Opaque 4 7d14h
repo-3598070695 Opaque 6 23h
repo-38486771 Opaque 6 37d
The --output yaml or --output json option can be used to display the JSON or YAML for the secret.
~]$ oc get secret repo-3598070695 --namespace openshift-gitops --output yaml
apiVersion: v1
data:
name: amVyZW1adsffYW5kYm94
password: Z2hwX2dnRVZaa1MwTjADSFVDSDzBwTzNDcU5tQ1NtUzBvRk5lWA==
project: bXktcHJvamVjdA==
type: Z2l0
url: aHR0cHM6LyADFBADSFY29tL3Rocml2ZW50L2plcmVteXMtc2FuZGJveC5naXQ=
username: Ia=
kind: Secret
metadata:
annotations:
managed-by: argocd.argoproj.io
creationTimestamp: "2025-01-23T02:08:59Z"
labels:
argocd.argoproj.io/secret-type: repository
name: repo-3598070695
namespace: openshift-gitops
resourceVersion: "432844381"
uid: 45a723c5-32ff-420e-b940-ba35074476c4
type: Opaque
And the jsonpath and base64 options can be used to return the cleartext values in the secret.
~]$ oc get secret repo-3598070695 --namespace openshift-gitops --output jsonpath="{.data.url}" | base64 --decode
https://github.com/foo/bar.git
Did you find this article helpful?
If so, consider buying me a coffee over at 