
The keytool command is included with Java, thus you will need to install Java to use the keytool command.
keystore vs. truststore
First and foremost, it's important to recongize the difference between a keystore and a truststore. Let's consider a scenario where a Tomcat application server is being used. There will be both inbound and outbound requests. Typically, an inbound request is when a remote system makes a request for an app deployed to Tomcat. Typically, and outbound request is when an app deployed to Tomcat needs to go out, such as when making a query to a remote SQL database.
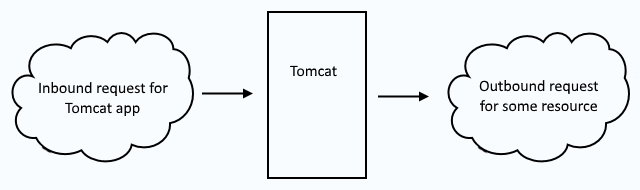
Inbound requests use a keystore to secure the requests. Outbound requests use a truststore to secure the request. So, when you see keystore, think "inbound" and when you see truststore think "outbound".
Create keystore
In this example, a keystore named keystore.jks is created, with a single PrivateKeyEntry with an alias of example.com.
- PrivateKeyEntry contains a private key and typically the public certificates that make up the certificate chain (the root certificate authority (CA) certificate, the intermediate certificate authority (CA) certifiate, and the server certificate).
- trustedCertEntry typically contains only the root certificate authority (CA) certificate but may contain the public certificates that make up the certificate chain (the root certificate authority (CA) certificate, the intermediate certificate authority (CA) certifiate, and the server certificate). A trustedCertEntry does not contain a private key.
keytool -genkey -alias example.com -keyalg RSA -keysize 2048 -keystore keystore.jks
In this example, a PKCS12 keystore is created.
keytool -genkey -alias example.com -keyalg RSA -keysize 2048 -keystore keystore.p12 -storetype PKCS12
Once the keystore has been created, the keytool command the -list option can be used to list the contents of the keystore, which should show that example.com is a PrivateKeyEntry.
~]# keytool -storetype pkcs12 -keystore /path/to/keystore.p12 -list
Keystore type: PKCS12
Keystore provider: SunJSSE
Your keystore contains 1 entry
example.com, May 12, 2023, PrivateKeyEntry,
Certificate fingerprint (SHA1): D0:80:B9:77:80:F9:DA:FF:77:54:4F:36:B1:A8:03:6F:25:EE:1C:72
The -v (verbose) option can be used to display the full details of each trustedCertEntry and PrivateKeyEntry in the keystore.
keytool -keystore /path/to/keystore.p12 -storetype pkcs12 -list -v
Or, the -alias option can be used to display the full details of a specific trustedCertEntry and PrivateKeyEntry in the keystore.
~]# keytool -keystore /path/to/keystore.p12 -storetype pkcs12 -list -v -alias www.example.com
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 1 entry
Alias name: example.com
Creation date: Feb 10, 2023
Entry type: PrivateKeyEntry
Certificate chain length: 3
Certificate[1]:
Owner: CN=www.example.com, OU=Information Technology, O=Acme, L=Appleton, ST=WI, C=US
Issuer: CN=IntermediateCA, DC=example, DC=com
Serial number: 3a000001d8af30a16a44402b790001000001d8
Valid from: Wed Jun 29 14:30:15 UTC 2022 until: Thu Jun 29 14:30:15 UTC 2023
Certificate fingerprints:
SHA1: D0:80:B9:77:80:F9:DA:FF:77:54:4F:36:B1:A8:03:6F:25:EE:1C:72
SHA256: 14:8C:CD:59:A9:C4:48:45:33:28:C3:AE:E7:6C:B6:1E:0A:F5:3B:9C:64:E5:BB:02:69:30:81:D9:6D:5F:06:AD
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Did you find this article helpful?
If so, consider buying me a coffee over at 