
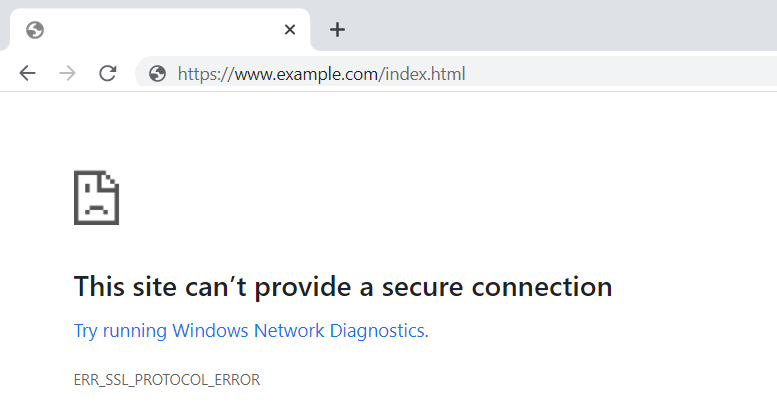
Let's say you get the following when attempt to request a web page from your Nginx web server over HTTPS.
Inside of the server block in your /etc/nginx/nginx.conf file will be SSL parameters. Ensure you have a listen directive for SSL. In this example, there is an SSL listen directive using port 443.
Notice in this example that the public certificate is located at /etc/pki/tls/foo.crt and the private key is located at /etc/pki/tls/foo.key.
server {
listen 80;
listen 443 ssl;
server_name www.example.com;
root /var/www/www;
index index.html;
ssl_certificate /etc/pki/tls/foo.crt;
ssl_certificate_key /etc/pki/tls/foo.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
}
Ensure the public certificate and private key exists.
~]# ll /etc/pki/tls
-rw-r--r--. 1 root root 1204 Jun 1 03:12 foo.crt
-rw-------. 1 root root 1679 Jun 1 03:12 foo.key
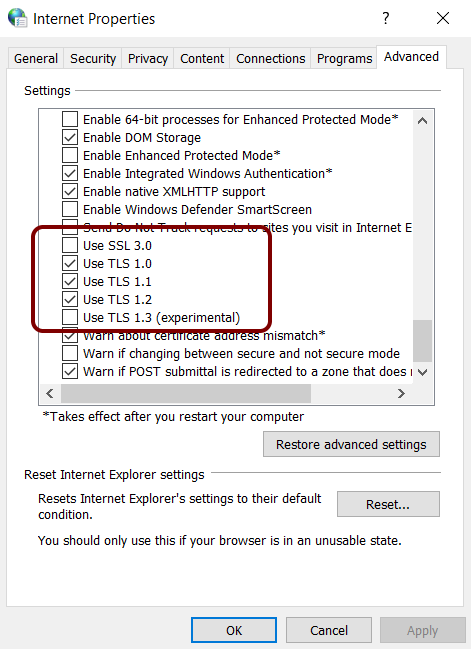
Notice also that SSL protocols TLSv1 TLSv1.1 and TLSV1.2 are being used. If you are using a Windows PC, ensure Internet Properties is configured to use one or more of these SSL protocols.
If you have two (or more) server blocks, each server will need a unique port for HTTP and HTTPS. Also, if you have a firewall, ensure the ports are allowed in the firewall. If SELinux is enabled (on Linux), ensure the http_port_t boolean allows the ports.
server {
listen 80;
listen 443 ssl;
server_name www.example.com;
root /var/www/www;
index index.html;
ssl_certificate /etc/pki/tls/foo.crt;
ssl_certificate_key /etc/pki/tls/foo.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
}
server {
listen 18084;
listen 18085 ssl;
server_name stage.example.com;
root /var/www/stage;
index index.html;
ssl_certificate /etc/pki/tls/foo.crt;
ssl_certificate_key /etc/pki/tls/foo.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
}
This error appears when attempting to request a resource from Nginx using HTTPS with Chrome.
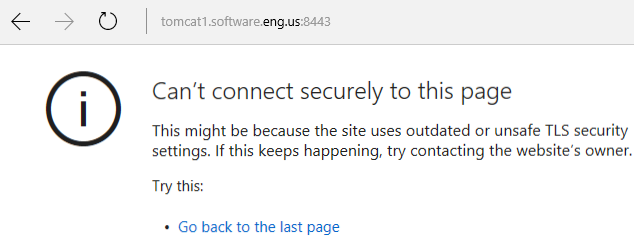
Likewise, Internet Explorer or Microsoft Edige should also display a similar message.
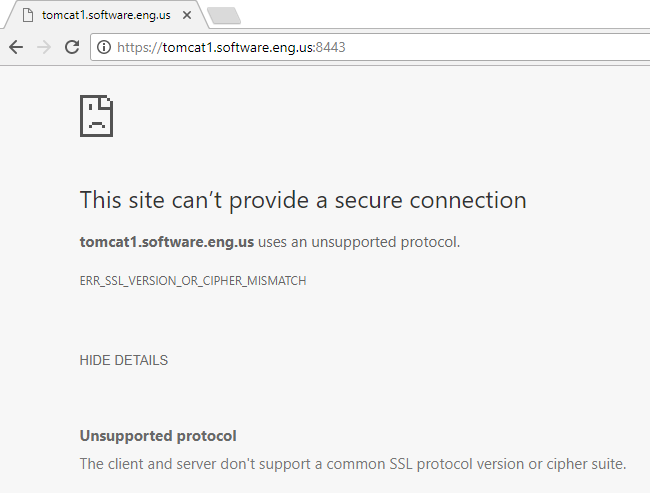
This error suggests some issue with the negotiation of the cipher between the client and server. Wireshark can be used to determine the ciphers that the client web browser can use, and the cipher being produced by Nginx.
Before modifying Nginx SSL/TLS settings, determine if the issue is client-side by navigating to https://badssl.com and selecting tests that are similar to your Nginx setup. For example, if your Nginx site is using a self-signed certificate, select the "self-signed" option at badssl.com. If "This site can’t provide a secure connection" appears on badssl.com, this suggests a client-side issue. For example, the client browser may be configured to refuse connections to sites using a self signed certificate.
Inside of the server block in the /etc/nginx/nginx.conf file will be SSL parameters. When creating the public certifcate and private key, a certain type of cipher will be used, such as RSA, DSA, or ECDSA. The browser will need to support the type of cipher being used by the public certificate and private key.
server {
. . .
ssl_certificate /etc/pki/tls/Certificate.crt;
ssl_certificate_key /etc/pki/tls/Private.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
}
In the prior markup, ssl_ciphers is set to High and not Null and not MD5. If you would rather specify the ciphers being used, you can use one or more of the following ciphers.
EECDH+ECDSA+AESGCM
EECDH+aRSA+AESGCM
EECDH+ECDSA+SHA384
EECDH+ECDSA+SHA256
EECDH+aRSA+SHA384
EECDH+aRSA+SHA256
EECDH+aRSA+RC4
EECDH
EDH+aRSA
RC4
In the log_format block in the /etc/nginx/nginx.conf file, add $ssl_protocol/$ssl_cipher. This will allow you to see what cipher was used.
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$ssl_protocol/$ssl_cipher'
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to restart nginx.
systemctl restart nginx
If your system is using init, use the chkconfig and service commands to restart nginx.
service nginx restart
The /var/log/nginx/access_log file will now include the SSL protocl and cipher that was used.
10.1.15.14 - - [14/Jul/2017:19:28:12 -0500] "GET /Signin HTTP/1.1" TLSv1.2/ECDHE-RSA-AES128-GCM-SHA256 . . .
Did you find this article helpful?
If so, consider buying me a coffee over at 