
By default, after installing and setting up Shibboleth SP, the /etc/httpd/conf.d/shib.conf file will contain a control to handle requests to www.example.com/secure.
<Location /secure>
AuthType shibboleth
ShibRequestSetting requireSession 1
require shib-session
</Location>
Navigating to www.example.com/secure will display shibsp::ConfigurationException.
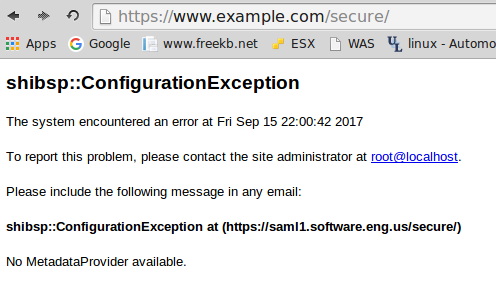
In the /etc/shibboleth/shibboleth2.xml file, in ApplicationDefaults, set entityID to the hostname of your SP.
<ApplicationDefaults entityID="https://<hostname of your SP>/shibboleth"
REMOTE_USER="eppn persistent-id targeted-id">
In SSO, set entityID to the hostname of your IdP and delete discoveryURL="https://ds.example.org/DS/WAYF".
<SSO entityID="https://<hostname of your IdP>/idp/shibboleth"
discoveryProtocol="SAMLDS">
SAML2 SAML1
</SSO>
Remove the comment from MetadataProvider, and adjust the file to point to the location of your idp-metadata.xml. This assumes that the SP and IdP are on the same server.
<MetadataProvider type="XML" validate="true" file="/opt/shibboleth-idp/metadata/idp-metadata.xml"/>
Ensure there are no syntax errors in the shibboleth2.xml file.
~]# shibd -tc /etc/shibboleth/shibboleth2.xml
. . .
overall configuration is loadable, check console for non-fatal problems
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to restart shibd and httpd.
systemctl restart shibd
systemctl restart httpd
If your system is using init, use the service command to restart shibd and httpd.
service shibd restart
service httpd restart
Did you find this article helpful?
If so, consider buying me a coffee over at 