
In the WebSphere admin console, at Security > SSL certificate and key management > Key stores and certificates > keystore or truststore, two of the links displayed are Personal certificates and Signer Certificates. What's the difference, you ask?
After a clean install of WebSphere, two certificates will be created, default and root.
- "default" is the "Personal certificate" in the keystore (keys.p12)
- "root" is the "Signer certificate" in the truststore (trust.p12), and is chained to the "default" certificate
You may want to also check out my article on understanding the difference between a keystore and truststore.
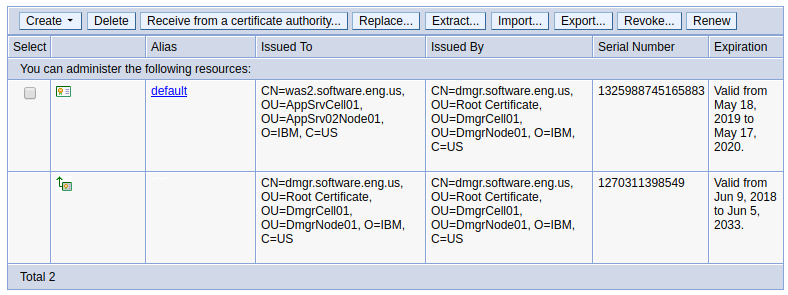
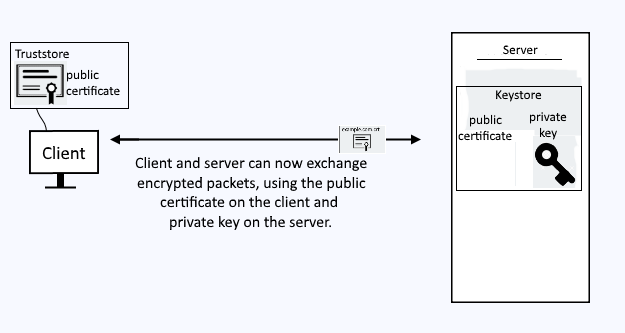
Personal certificate
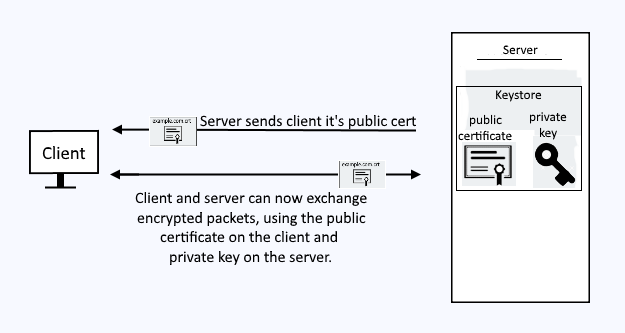
When a client submits a request to get a resource from your WebSphere application server over HTTPS, a Personal certificate (and it's private key) in your keystore will be used for SSL to encrypt the packets being exchanged between the client and the server.
Probably the easiest way to replicate this is to use your personal computer (e.g. your laptop) and navigate to the URL for the WebSphere admin console over HTTPS (https://<hostname>:9043/ibm/console). This will trigger the SSL negotation process, where the WebSphere application server will present to your laptops web browser the Personal certificate from the keystore.
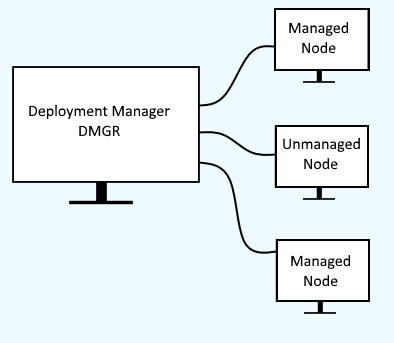
When a node server is fedrated into the dmgr, there will be two servers at play, the node server and the dmgr server.
Signer certificate
Trust must be established between the dmgr and node servers, so that packets can be exchanged over a secured channel, such as HTTPS. This is where Signer Certificates come into the picture. In this example, the hostname of the dmgr server is dmgr.software.eng.us and the hostname of the node server is was1.software.eng.us. When the was1.software.eng.us node server is federated into the dmgr, two certificates will be added to the NodeDefaultTrustStore Signer certificates, default and root. The default certificate is the dmgr certificate and the root certificate is the node server certificate. These certificates are then used when the dmgr and node server need to communicate over a secured channel.
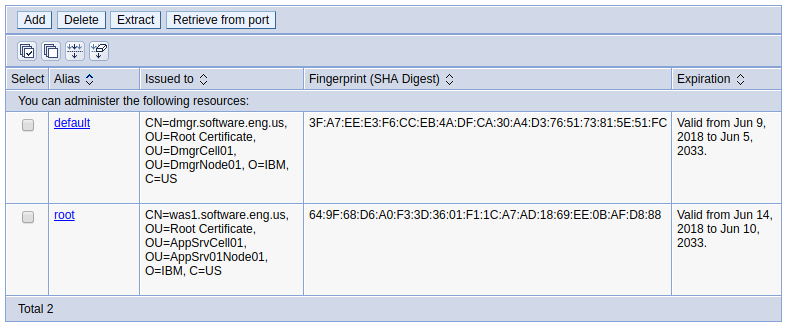
The default and root certificates are then used when the dmgr and node server need to communicate over a secured channel.
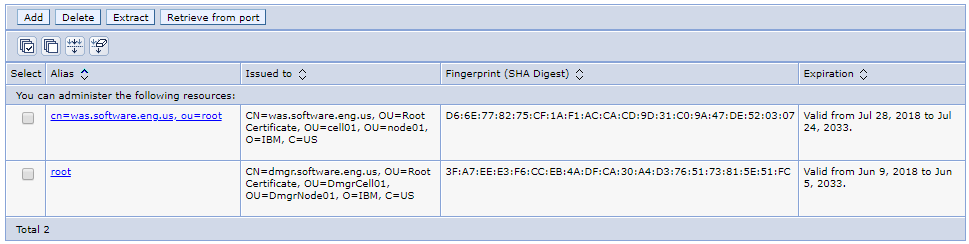
Likewise, if an IHS web server is added to the dmgr, then you would have the root dmgr certificate and the certificate from the IHS web server (was.software.eng.us in this example).
Did you find this article helpful?
If so, consider buying me a coffee over at 