
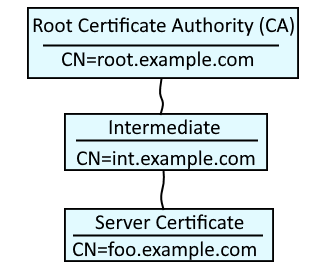
A certificate chain contains the collection of root, intermediate and server/child certificates. In this example, root.example.com is the root certificate authority (CA). Typically, one or more intermediate certificates are children of the root CA, and one or more server certificates are children of the intermediate certificate. OpenSSL can be used to create a file that contains the root, intermediate and server certificate chain.
Use apt-get on a Debian distribution (Debian, Ubuntu, Mint) or dnf or yum on a Red Hat distribution (CentOS, Fedora, Red Hat) to install the OpenSSL package.
dnf install openssl
Root Certificate Authority (CA) certificate
First you will need to create the root certificate authority (CA) certificate. Check out my article on creating a self signed RSA certificate. Let's say you use this one liner to create ca.cer, the root certificate authority (CA) certificate.
openssl req -x509 -sha512 -nodes -days 9999 -newkey rsa:4096 -keyout ca.key -out ca.cer -subj "/C=US/ST=California/L=Los Angeles/O=FreeKB/OU=IT/CN=FreekB Root CA"
Intermediate certificate
Then create the Certificate Signing Request (CSR) for the intermediate certificate. You may also want to check out my article on creating a Certificate Signing Request (CSR).
openssl req -new -key ca.key -out intermediate.csr -subj "/C=US/ST=California/L=Los Angeles/O=FreeKB/OU=IT/CN=FreeKB Intermediate CA"
And now you can create the intermediate certificate using the root CA certificate as the issuer of the intermediate certificate.
openssl x509 -req -sha512 -days 999 -set_serial 01 -CAkey ca.key -CA ca.cer -in intermediate.csr -out intermediate.cer
And you can now see that the intermediate certificate has been issued by the root CA.
~]$ openssl x509 -in intermediate.cer -noout -subject -issuer
subject=C = US, ST = California, L = Los Angeles, O = FreeKB, OU = IT, CN = FreeKB Intermediate CA
issuer=C = US, ST = California, L = Los Angeles, O = FreeKB, OU = IT, CN = FreeKB Root CA
Server / Child certificate
Then create the Certificate Signing Request (CSR) for the server / child certificate.
openssl req -new -key ca.key -out child.csr
And now you can create the child certificate using the intermediate certificate authority (CA) certificate as the issuer of the child certificate.
openssl x509 -req -sha512 -days 365 -CAcreateserial -CAkey ca.key -CA intermediate.cer -in child.csr -out child.cer
And you can now see that the server certificate has been issued by the intermediate certificate authority (CA).
~]$ openssl x509 -in child.cer -noout -subject -issuer
subject=C = US, ST = California, L = Los Angeles, O = FreeKB, OU = IT, CN = FreeKB Child Certificate
issuer=C = US, ST = California, L = Los Angeles, O = FreeKB, OU = IT, CN = FreeKB Intermediate CA
Did you find this article helpful?
If so, consider buying me a coffee over at 