
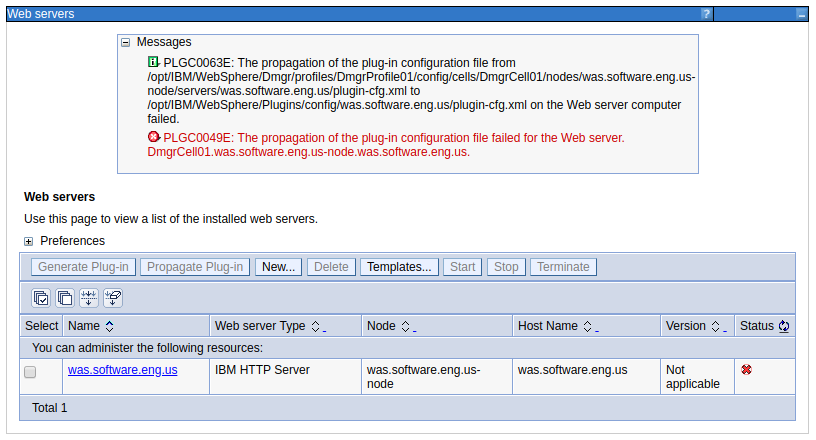
PLGC0063E and PLGC0049E appears when attempting to propagate the web server plugin in WebSphere.
Or on the command line.
~]$ /opt/WebSphere/AppServer/profiles/my_profile/bin/GenPluginCfg.sh -cell.name Cell01 -node.name Node01 -webserver.name WebServer1 -propagate yes
*** Initiating original genplugincfg call using args of: -cell.name Cell01 -node.name Node01 -webserver.name WebServer1 -propagate yes
IBM WebSphere Application Server, Release 8.5
WebSphere Plugin Configuration Generator
Copyright IBM Corp., 1997-2012
PLGC0005I: Plug-in configuration file = /opt/WebSphere/AppServer/profiles/my_profile/config/cells/Cell01/nodes/Node01/servers/WebServer1 /plugin-cfg.xml
PLGC0052I: Plug-in configuration file generation is complete for the Web server. Cell01.Node01.WebServer1.
PLGC0063E: The propagation of the plug-in configuration file from
/opt/WebSphere/AppServer/profiles/my_profile/config/cells/Cell01/nodes/Node01/servers/WebServer1/plugin-cfg.xml to /opt/WebSphere/Plugins/config/WebServer1/plugin-cfg.xml on the Web server computer failed.
PLGC0049E: The propagation of the plug-in configuration file failed for the Web server. Cell01.Node01.WebServer1.
==========================================================================
PLGC0032E: An exception occurred while generating plug-in configuration:
PLGC0049E: The propagation of the plug-in configuration file failed for the Web server. Cell01.Node01.WebServer1.
==========================================================================
PLGC0034E: Root exception:
No Connection
==========================================================================
PLGC0004E: An exception occurred while running the GenPluginCfg utility.
This can occur if the IBM IHS Admin Server is not running.
- Start IBM IHS Admin Server using the adminctl command
- Start IBM IHS Admin Server using the systemctl command
- Start IBM IHS Admin Server using the httpd command
Deployment Manager Log Level
Update the deployment manager to log events at the following log levels and restart the deployment manager for this change to take effect.
*=info:
com.ibm.ws.console.web.*=all:
com.ibm.ws.management.webserver.*=all:
com.ibm.ws.process.*=all:
com.ibm.websphere.plugincfg.*=all:
com.ibm.websphere.management.filetransfer.*=all:
com.ibm.ws.management.filetransfer.*=all:
com.ibm.ws.management.fileservice.*=all
IBM IHS Admin Server Log Level
Update the admin.conf file to log events at log level debug. stop and then start the admin server for this change to take effect.
LogLevel debug
Ensure the admin server is running.
~]# ps -ef | grep -i httpd | grep -i admin
root 35417 1 0 02:39 ? 00:00:00 /opt/IBMIHS/bin/httpd -f /opt/IBMIHS/conf/admin.conf -k start
root 35418 35417 0 02:39 ? 00:00:00 /opt/IBMIHS/bin/httpd -f /opt/IBMIHS/conf/admin.conf -k start
nobody 35419 35417 0 02:39 ? 00:00:00 /opt/IBMIHS/bin/httpd -f /opt/IBMIHS/conf/admin.conf -k start
Admin Server Config
Read the admin.passwd file to determine the admin server username (john.doe in this example).
~]# cat /opt/IBMIHS/conf/admin.passwd
john.doe:tgf9FzBnFm16Z
Use the htpasswd command line tool to verify the admin server password.
~]# /opt/IBMIHS/bin/htpasswd -v /opt/IBMIHS/conf/admin.passwd john.doe
Enter password:
Password for user admin correct.
Determine the port being used by the admin server.
~]# grep ^Listen /opt/IBMIHS/conf/admin.conf
Listen 8008
Ensure you can access the admin server over HTTP, and that the admin server URL produces a page prompting you for your username and password.
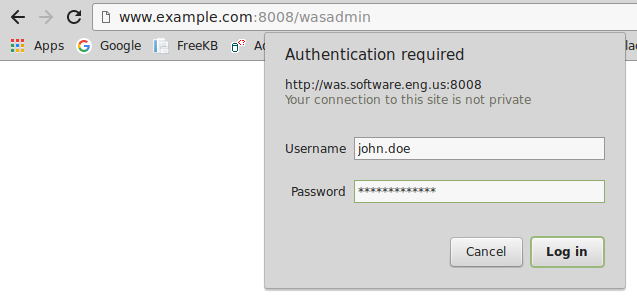
If the wasadmin page produces something like "page cannot be displayed", SSL may be enabled in admin.conf. You could comment out the SSL directives in admin.conf and then restart the admin server so that you can access the admin server over HTTP.
#SSLEnable
#SSLServerCert default
#Keyfile "/path/to/keyfile.kdb"
If the wasadmin page produces 403 Forbidden, you probably have a syntax error in your URL, such as "wsadmin" instead of "wasadmin". Or, refer to this article.
Once you can get to the admin page URL over HTTP, when you provide your username and password, the following page should be displayed. This is normal, and not suggestive of a problem. This confirms you are using the appropriate username and password.

Admin Server Port
Typically the Admin Server is configured to communicate on port 8008.
- If using firewalld (on a Linux system), ensure port 8008 is allowed
- If using iptables (on a Linux system), ensure port 8008 is allowed
Node
In the WebSphere console, at System administration > Nodes, the hostname of the IBM IHS web server will be listed. Use the nslookup command to determine the IP address being returned by DNS.
C:\>nslookup server1.example.com
Name: server1.example.com
Address: 10.75.217.61
On the IBM IHS web server, ensure the ServerName and Listen match the output of the nslookup command.
~]$ egrep -i 'ServerName|Listen' /opt/IBMIHS/conf/httpd.conf
ServerName server1.example.com
Listen 10.75.217.61
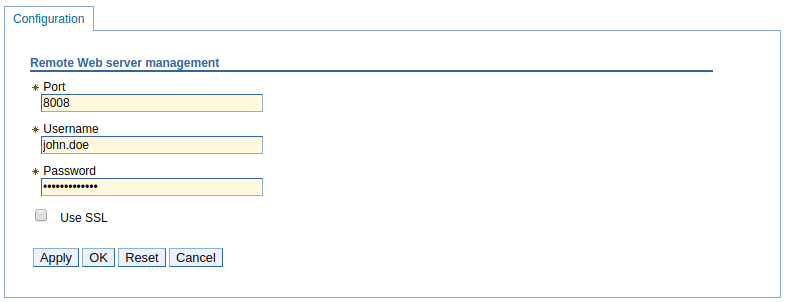
Remote web server management
In the WebSphere console, at Servers > Server types > Web servers > your web server > Remote web server management, ensure the correct port and username are listed for the admin server.
Directory Permissions
Let's say you are attempting to propagate the plugin-cfg.xml file from the deployment manager to the /opt/IBM/WebSphere/Plugins/config/webserver directory on the IBM IHS web server. In this scenario, every directory leading up to the /opt/IBM/WebSphere/Plugins/config/webserver directory will need to have the x (execute) permission for the other user, like this.
chmod o+x /opt
chmod o+x /opt/IBM
chmod o+x /opt/IBM/WebSphere
chmod o+x /opt/IBM/WebSphere/Plugins
chmod o+x /opt/IBM/WebSphere/Plugins/config
chmod o+x /opt/IBM/WebSphere/Plugins/config/webserver
Move or Remove the plugin-cfg.xml file
If the plugin-cfg.xml file already exists in the target directory, remove the plugin-cfg.xml file, because when the plugin-cfg.xml file already exists, there will be an attempt to overwrite the plugin-cfg.xml. Removing the plugin-cfg.xml file will elminate any permissions issues with the plugin-cfg.xml file.
rm /opt/IBM/WebSphere/Plugins/config/webserver/plugin-cfg.xml
Check the Logs
Now, try to propogate the plugin again. If the propagation still fails, check the SystemOut.log and SystemErr.log and FFDC logs on the deployment manager and also check the admin_error.log on the admin server.
Then, check the admin_error.log file. To resolve the following issue, I had to update the admin.password file to be owned by the user that started the admin server.
AH01620: Could not open password file: /opt/IBM/WebSphere/IHS/conf/admin.password
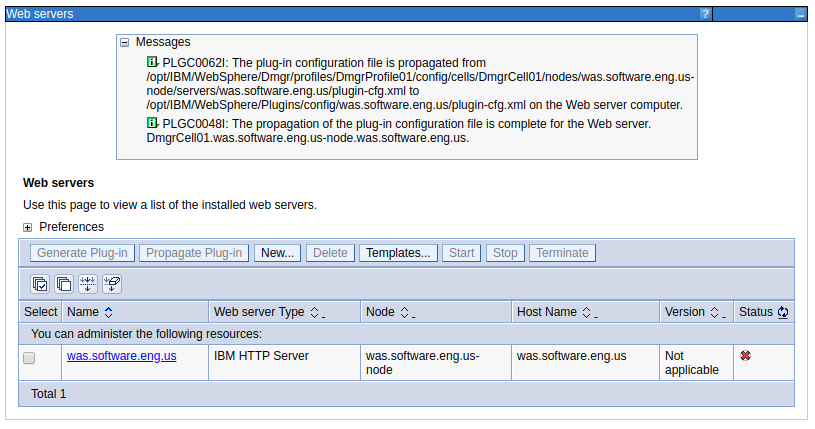
You should now be able to propagate the plugin.
Did you find this article helpful?
If so, consider buying me a coffee over at 