
Both firewalld and iptables are common Linux firewalls. This tutorial is for iptables. If firewalld is enabled on your system, stop, mask, and disable firewalld, so that firewalld is permanently disabled, even after a reboot.
Use apt-get or yum to install iptables.
apt-get install iptables-services
yum install iptables-services
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to start and enable iptables.
systemctl enable iptables
systemctl start iptables
systemctl status iptables
If your system is using init, use the service command to start and enable iptables.
service iptables enable
service iptables start
service iptables status
The file that contains the configuration for iptables is located a /etc/sysconfig/iptables.
/etc/sysconfig/iptables
CHAINS
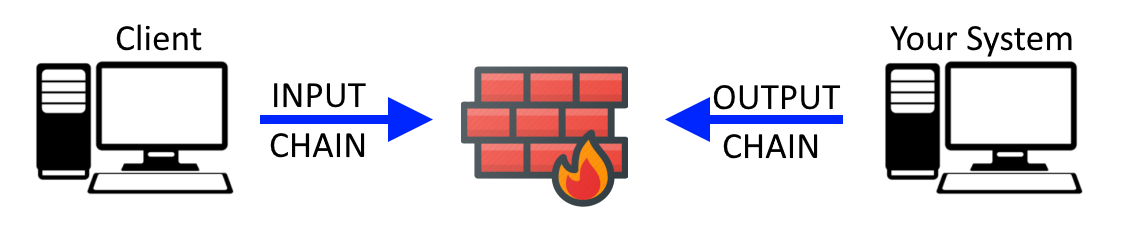
iptables uses chains to allow or deny certain types of requests. The default chains are:
- INPUT = Inbound request addressed to the host
- OUTPUT = Output request created by the host
- FORWARD = Neither addressed to the host nor created by the host. Forward is used to forward or route a packet to it's destination
FLUSHING RULES
Typically, after a clean install of iptables, iptables will already have default rules in place. The -F or --flush option can be used to flush all of the rules.
iptables --flush
LISTING RULES
The iptables command with the -L or --list option can be used to display the rules. If you flushed all the rules, there should be no rules.
iptables -L -v
. . .
Chain INPUT (policy ACCEPT)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT)
pkts bytes target prot opt in out source destination
Chain ACCEPT (policy ACCEPT)
pkts bytes target prot opt in out source destination
ADDING RULES
- The -I or --insert option can be used to add a rule at the beginning of a chain.
- The -A or -- append option can be used to add a rule at the end of a chain.
This is important, because the order in which the rules are listed matters. iptables will read the rules from the top down, meaning the first rule listed will be read, then the second rule, and so on, until the last rule is read. Typically, the first rule that is added is to allow traffic directed to the lo interface, which is the loopback interface, localhost, or 127.0.0.1.
iptables -I INPUT -i lo -j ACCEPT
Often, the second rule that is added is to allow SSH connections. Notice now that the -A (append) option is used, not the -I (insert) option, so that the ICMP rule is appended after the lo rule.
iptables -A INPUT -p tcp --dport 22 -m conntrack --ctstate NEW,ESTABLISHED --source 192.168.0.0/24 -j ACCEPT
iptables -A OUTPUT -p tcp --sport 22 -m conntrack --ctstate ESTABLISHED -j ACCEPT
Optionally, if you want to be able to ping the system, a rule is added to allow ICMP echo requests, so that the system can be pinged. Notice now that the -A (append) option is used, not the -I (insert) option, so that the ICMP rule is appended after the SSH rule.
iptables -A INPUT -p icmp --icmp-type echo-request -j ACCEPT
DELETING RULES
The -D or --delete option is used to delete a rule. In this example, the rule to allow ICMP echo requests is deleted.
iptables -D INPUT -p icmp --icmp-type echo-request -j ACCEPT
DROP
The end of a chain should have a DROP rule, so that any connection not matching a rule in the chain is dropped. However, the OUTPUT chain may not need the drop rule, as this can cause issues with some protocols.
iptables -A INPUT -j DROP
iptables -A FORWARD -j DROP
SAVE CHANGES
The following command will save the changes made to iptables.
iptables-save > /etc/sysconfig/iptables
RESTORE IPTABLES
The iptables-restore command can be used to restore iptables from the /etc/sysconfig/iptables file.
iptables-restore < /etc/sysconfig/iptables
COMMON RULES
25, 110, 143, 587, 993, 995 / Email
-A INPUT -p tcp -m tcp --dport 25 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 110 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 143 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 587 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 993 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 995 -j ACCEPT
53 / DNS
-A INPUT -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -p udp -m udp --sport 53 -j ACCEPT
67 / DHCP
-A INPUT -p tcp --dport 67 -j ACCEPT
80 / HTTP and 443 / HTTS
-A INPUT -p tcp --dport http -j ACCEPT
-A INPUT -p tcp --dport https -j ACCEPT
123 / NTP client
-A INPUT -p udp --dport 123 -j ACCEPT
-A OUTPUT -p udp --sport 123 -j ACCEPT
123 / NTP server
-A INPUT -p udp --sport 123 -j ACCEPT
-A OUTPUT -p udp --dport 123 -j ACCEPT
137, 138, 139, 445 / Samba, NetBIOS
-A INPUT -p udp --dport 137 -j ACCEPT
-A INPUT -p udp --dport 138 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 139 -j ACCEPT
-A INPUT -m state --state NEW -m tcp -p tcp --dport 445 -j ACCEPT
3128 / Proxy
-A INPUT -p tcp --dport 3128 -j ACCEPT
Did you find this article helpful?
If so, consider buying me a coffee over at 