
While PHP is definitely more powerful than HTML, it is also more vulnerable. As an example, let’s say we have an input form on our website, which allows users to create a username for our website. Then after the user is registered, we will display the users name on the page. Let’s steps through this with both an innocent users, and a nefarious user.
First, our innocent user goes to our registration page, and creates their username. The data entered into the input form would be inserted into our MySQL database. Notice this form posts the data to the insert.php page.
<form method='post' action='insert.php'>
<p>Username: <input type='text' name='username'>
<button>Submit</button>
</p>
</form>
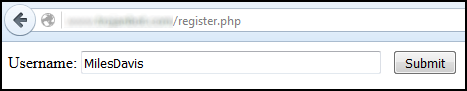
The insert.php page has the following code, which inserts the form data into MySQL, and then redirects back to the welcome.php page.
<?php
include includes/mysql_includes.php;
$con = new mysqli($mysql_domain,$mysql_user,$mysql_pass,userpass);
$username = $_POST['username'];
$insert = "insert into userpasstbl (username) values ('$username');
$processing = $con->query($insert);
Header('location:welcome.php');
?>
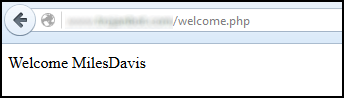
The welcome.php page displays the username.
<?php
include Includes/mysql_includes.php;
$con = new mysqli($mysql_domain,$mysql_user,$mysql_pass,userpassdb);
$select = "select username from userpasstbl where id=$id";
$select_query = mysqli_query($con,$select);
while($row = mysqli_fetch_array($select_query) {
echo 'Welcome'; echo $row['username'];
}
?>
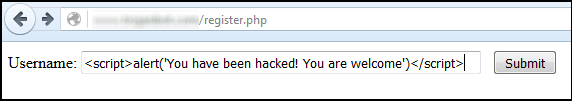
Now it’s our nefarious users turn. Our nefarious user is naughty. Instead of entering an innocent username, the nefarious user enters the following JavaScript.
<script>alert(‘You have been hacked! You are welcome.)</script>
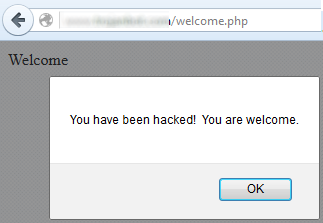
The insert.php page inserts the JavaScript into MySQL. This causes the JavaScript alert to appear on the welcome.php page. While not a very sophisticated attack, it demonstrates some of the possible vulnerabilities when using PHP and MySQL.
Fortunately, these types of attacks are known, and PHP has some variables to prevent these types of attacks. Following this example, we could append the htmlspecialchars code to the insert.php page.
<?php
include includes/mysql_includes.php;
$con = new mysqli($mysql_domain,$mysql_user,$mysql_pass,userpassdb);
$username = htmlspecialchars($_POST['username']);
$insert = "insert into userpasstbl (username) values ('$username');";
$processing = $con->query($insert);
Header('location:welcome.php');
?>
This would convert the opening brackets < to their HTML of > and the closing brackets > to $lt; . This way, instead of the literal JavaScript being inserted into MySQL, >script<alert(‘You have been hacked! You are welcome.) >/script> would be inserted. In this format, the JavaScript would fail to function, thus we have mitigated this attack.
This is only scratching the surface of security. As an example, following are some other very useful features of PHP to prevent malicious users from compromising our MySQL database.
- mysqli_real_escape_string (a package that prevents many attacks, such as escaping – very good at resolving issues with apostrophes)
- stripslahes (eliminates back-slahes \\ from being inserted into MySQL)
- trim (removes leading/ending whitespaces from data)
- SHA1 / MD5 / Encrypt (encrypts data, such as passwords)
- salt (adds random data to data, such as passwords, so they cannot be reverse engineered)
Did you find this article helpful?
If so, consider buying me a coffee over at 