
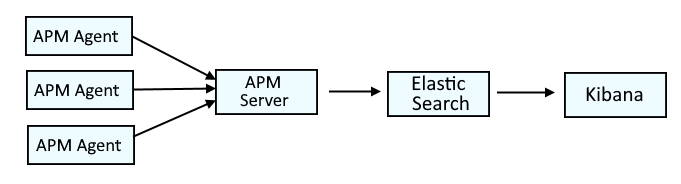
This diagram illustrates the systems that are typically used with Elastic APM (Application Performance Monitoring). APM agents send monitoring data to an APM server. The APM server pass the monitoring data onto Elastic Search. In other words, the APM Server receives data from APM agents and transforms them into Elastic Search documents that can be visualised in Kibana
This is similar to the ELK stack (Elastic Search, Logstash, Kibana), but would actually be the EAK stack (Elastic Search, APM, Kibana).
To monitor an application server in Elastic APM (Application Performance Monitoring), such as a Tomcat or WebSphere application server, the elastic-apm-agent-<version>.jar file will need to reside on the system that contains the application server. In this example, the elastic-apm-agent-<version>.jar file is located in the /usr/local/elastic directory (on a Linux system).
/usr/local/elastic/elastic-apm-agent-1.20.0.jar
Additionally, the elasticapm.properties file will contain directives. If you place the elasticapm.properties file in the same directory as the elastic-apm-agent-<version>.jar file, the agent will use the elasticapm.properties file. Here is an example of the elasticapm.properties file.
server_urls=https://apm.example.com:443
secret_token=<token>
application_packages=com.example
log_level=ERROR
log_file=/var/logs/elasticapm/elasticapm.log
verify_server_cert=true
central_config=false
When verify_server_cert is set to true, an SSL certificate will be needed to establish communication to Elastic APM over HTTPS on port 443. For example, a Tomcat application server usually stores certificates in a trust store, and the Java keytool command can be used to list the certificates in the trust store.
keytool -keystore truststore.p12 -storetype pkcs12 -list
In this example, the trust store contains a certificate with an alias of foo.example.com, thus the Tomcat application server would present the foo.example.com certificate to the Elastic APM system when attempting to connect to Elastic APM system. If the Elastic APM system is configured to established an SSL connection with the foo.example.com certificate, then the connection should be established.
Keystore type: jks
Keystore provider: SUN
Your keystore contains 1 entry
foo.example.com, Aug 21, 2031, trustedCertEntry,
Certificate fingerprint (SHA1): 1E:0C:EB:DC:CA:E3:DC:16:76:77:EE:BE:91:9B:43:3D:9D:10:15:8E
Add the following options to each application servers startup arguments, such as the setenv.sh file for a Tomcat application server, and then restart the application server for this change to take effect.
-javaagent:/usr/local/elastic/elastic-apm-agent-1.20.0.jar
-Delastic.apm.service_name=<name of your Tomcat Application Server>
When the agent starts, the Elastic APM log should contain something like this.
[apm-server-healthcheck] INFO co.elastic.apm.agent.report.ApmServerHealthChecker - Elastic APM server is available: {"build_date":"2018-11-05T07:58:08Z","build_sha":"dffb98a72a262ca22adad0152f0245ea743ea904","version":"7.0.0-alpha1"}
Did you find this article helpful?
If so, consider buying me a coffee over at 