
If you are not familiar with the oc command, refer to OpenShift - Getting Started with the oc command.
By default, all services in a project / namespace are accessible from other pods in any namespace. A network policy can be used to allow or deny incoming (ingress) access to the services in a namespace.
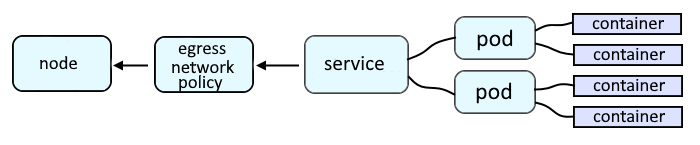
Egress provides a way for an application deployed on OpenShift to access an external URL, such as http://www.example.com.
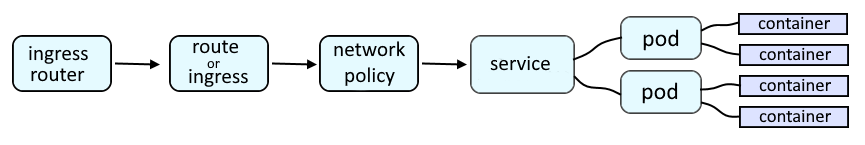
An OpenShift route or an Ingress route will provide a URL such as http://route001-project001.apps.openshift.example.com:8080 which is used to route a request onto a service, which is then routed onto a pod, and then to the container in the pod, and finally to the application running in the container.
A JSON or YAML file that contains key value pairs used to create an object, such as a config map, deployment, a project, a pod, a route, a secret, a service, et cetera. These files are known as templates. The oc explain command can be used to get the list of keys that can be used in the JSON or YAML template file.
oc explain networkpolicy
And then more details on each key can be displayed.
oc explain networkpolicy.spec
Following are the common types of Network Policies.
- Allow or deny all requests coming in (ingress) to a project / namespace
- Allow or deny all requests going out (egress) of a project / namespace
- Allow or deny requests coming in (ingress) to a project / namespace from some other project / namespace
- Allow or deny requests coming in (ingress) to a project / namespace that do not match a pods label (e.g. region=east)
- Allow or deny requests coming in (ingress) to a project / namespace from an IP address outside of a certain IP subnet (e.g. 172.17.0.0/16)
- Allow or deny requests going out (egress) of a project / namespace to an IP subnet (e.g. 10.0.0.0/24) and a specific Port (e.g. 8080) or a Port range (e.g. 30000 - 31000)
For example, let's say you have a YAML file named networkpolicy.yml that contains the following markup. This network policy will allow ingress and egress traffic in the project that this network policy exists in from my-project.
- podSelector: {} selects all pods in the project that this network policy exists in
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-my-project
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
ingress:
- from:
- namespaceSelector:
matchLabels:
project: my-project
The oc apply or oc create command with the -f or --filename option can be used to create the network policy using the template JSON or YAML file.
The oc replace command can be used to replace a network policy using a new or updated template JSON or YAML file.
The oc edit command can be used to update a network policy template YAML file.
~]$ oc create --filename networkpolicy.yml
networkpolicy.networking.k8s.io/allow-my-project created
The oc get networkpolicies command can then be used to list the network policies that have been created in the project.
Did you find this article helpful?
If so, consider buying me a coffee over at 