
If you are not familiar with AWS Application Load Balancers, check out my article FreeKB - Amazon Web Services (AWS) - Getting Started with Application Load Balancer (ALB).
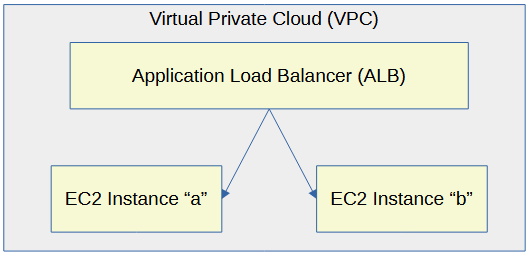
Let's say you have two or more EC2 instances that are producing web apps. An application load balancer can be used to load balance the requests for the web app.
This assumes you have already configured the aws command line tool. If not, check out my article on Getting Started with the AWS CLI.
To create an Elastic Load Balancer, you will need two different Virtual Private Cloud Subnets and a Security Group.
The aws ec2 describe-vpcs command can be used to list your EC2 Virtual Private Clouds (VPC).
aws ec2 describe-subnets
Something like this should be returned. In this example, the VPC has CIDR 172.31.0.0/20 CIDR.
{
"Vpcs": [
{
"CidrBlock": "172.31.0.0/16",
"DhcpOptionsId": "dopt-017f01234abcd2fc9",
"State": "available",
"VpcId": "vpc-014d2fc1234abcd01",
"OwnerId": "713541234252",
"InstanceTenancy": "default",
"IsDefault": true
}
]
}
The aws ec2 describe-subnets command can be used to list the EC2 subnets in your Virtual Private Clouds (VPC).
aws ec2 describe-subnets
Something like this should be returned. In this example, the 172.31.0.0/20 subnet is returned. I all liklihood, there are probably 3 (or more) subnets for these CIDRs.
- 172.31.0.0/20 (first available IP 172.31.0.1, last available IP 172.31.15.254)
- 172.31.16.0/20 (first available IP 172.16.0.1, last available IP 172.31.31.254)
- 172.31.32.0/20 (first available IP 172.32.0.1, last available IP 172.31.47.254)
{
"Subnets": [
{
"AvailabilityZone": "us-east-1d",
"AvailabilityZoneId": "use1-az6",
"AvailableIpAddressCount": 4091,
"CidrBlock": "172.31.0.0/20",
"DefaultForAz": true,
"MapPublicIpOnLaunch": true,
"MapCustomerOwnedIpOnLaunch": false,
"State": "available",
"SubnetId": "subnet-03f11411234f6abcd",
"VpcId": "vpc-014d2123433abcd01",
"OwnerId": "713512344252",
"AssignIpv6AddressOnCreation": false,
"Ipv6CidrBlockAssociationSet": [],
"SubnetArn": "arn:aws:ec2:us-east-1:711234074252:subnet/subnet-031234abcd0f6cdbc",
"EnableDns64": false,
"Ipv6Native": false,
"PrivateDnsNameOptionsOnLaunch": {
"HostnameType": "ip-name",
"EnableResourceNameDnsARecord": false,
"EnableResourceNameDnsAAAARecord": false
}
}
]
}
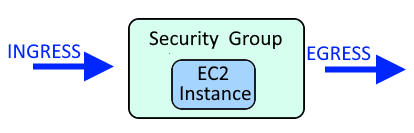
A Security Group is used to allow or deny requests coming in (ingress) and/or requests going out (egress). For example, a Security Group could be used to only allow requests within a certain IP address range to come in (ingress) and go out (egress) of an EC2 Instance.
The aws ec2 describe-security-groups command can be used to list your EC2 security groups.
aws ec2 describe-security-groups
The JSON output should include the Secrutiy Group ID.
{
"SecurityGroups": [
{
"GroupName": "MySecurityGroup",
"VpcId": "vpc-1a2b34aa",
"OwnerId": "123456789012",
"GroupId": "sg-0c3296123415abcd1"
}
]
}
The aws elbv2 create-load-balancer command can then be used to create an Elastic Load Balancer.
aws elbv2 create-load-balancer
--name my-application-load-balancer
--subnets subnet-03f11411234f6abcd subnet-03123451234f7ab34
--security-groups sg-0c3296123415abcd1
There are a few different types of load balancers. If --type is not used, an Application Load Balancer will be created.
- Application Load Balancers (e.g. you have a web app that you want to load balance)
- Network Load Balancers (e.g. you have SQL databases that you want to load balance)
- Gateway Load Balancers
- Classic Load Balancers (deprecated)
The scheme can either be internet facing or internal. If --scheme is not used, the load balancer scheme will be internet-facing.
- internet-facing requests a public subnet and is used to load balance requests coming in from the external internet.
- internal would be used to load balance requests inside of your AWS Virtual Private Cloud (VPC).
The IP Address Type can either be IPV4 only or dual stack for both IPv4 and IPv4.
aws elbv2 create-load-balancer
--name my-application-load-balancer
--type application
--subnets subnet-03f11411234f6abcd subnet-03123451234f7ab34
--security-groups sg-0c3296123415abcd1
--scheme <internet-facing|internal>
--IpAddressType <ipv4|dualstack>
Something like this should be returned
{
"LoadBalancers": [
{
"LoadBalancerArn": "arn:aws:elasticloadbalancing:us-east-1:123456789012:loadbalancer/app/my-load-balancer/ffd90871234abcde",
"DNSName": "my-load-balancer-371234535.us-east-1.elb.amazonaws.com",
"CanonicalHostedZoneId": "Z35SXDOTRQ7X7K",
"CreatedTime": "2023-03-28T01:23:28.410000+00:00",
"LoadBalancerName": "my-load-balancer",
"Scheme": "internet-facing",
"VpcId": "vpc-014d2fcfa335d3c01",
"State": {
"Code": "provisioning"
},
"Type": "application",
"AvailabilityZones": [
{
"ZoneName": "us-east-1b",
"SubnetId": "subnet-03f11411234f6abcd",
"LoadBalancerAddresses": []
},
{
"ZoneName": "us-east-1a",
"SubnetId": "subnet-03123451234f7ab34",
"LoadBalancerAddresses": []
}
],
"SecurityGroups": [
"sg-0c3296123415abcd1"
],
"IpAddressType": "ipv4"
}
]
}
Next you will usually need to :
- Create an Elastic Load Balancer Target Group
- Register Targets with an Elastic Load Balancer Target Group
- Create an Elastic Load Balancer Listener
Did you find this article helpful?
If so, consider buying me a coffee over at 