
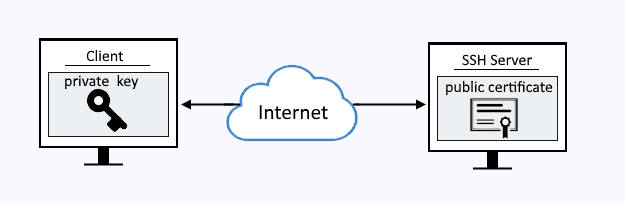
Public key authentication can be used to connect to an OpenSSH server without having to provide your password.
Client
Use the mkdir (make directory) command to create the users hidden .ssh directory.
mkdir /home/JohnDoe/.ssh
In this example, ssh-keygen is used to create the public certificate and private key. The public certificate is named id_rsa.pub and the private key is id_rsa.
ssh-keygen -t rsa -b 4096 -N '' -C $(whoami)@$(hostname) -f $HOME/.ssh/id_rsa 2>&1 >/dev/null
Use the usermod command to make JohnDoe a member of the wheel group (on a Red Hat system).
usermod -aG wheel JohnDoe
OpenSSH server
On the OpenSSH server, ensure the /etc/ssh directory has -rwxr-xr-x (0755) permissions and is owned by root:root.
chmod 0755 /etc/ssh
Configure your /etc/ssh/sshd_config file to have the following settings. You can chose any filename and directory for the authorized keys file.
PubkeyAuthentication yes
AuthorizedKeysFile /etc/ssh/authorized_keys
Create the authorized_keys file.
touch /etc/ssh/authorized_keys
Set the authorized_keys file to have -rw-r----- (0640) permissions and is owned by root:wheel.
chmod 640 /etc/ssh/authorized_keys
chown root /etc/ssh/authorized_keys
chgrp wheel /etc/ssh/authorized_keys
Restore the SELinux context of the files in the /etc/ssh directory.
restorecon -FRvv /etc/ssh
Ensure the authorized_keys file has the following SELinux context.
ls -lZ /etc/ssh
-rw-r-----. root wheel system_u:object_r:etc_t:s0 authorized_keys
Copy the content of id_rsa.pub on the "client" machine and paste the content into the authorized keys file on the OpenSSH server machine. In this example, the authorized_keys file would have the following (without the line breaks). The ssh-copy-id command can be used.
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAqphOmkv0RPMn48EwCRED/eSSYsbyrRlxymWdEA/
rYuq4eqZAVzTYxJxnTuCTLnrr5hvVMYstcEnwFB+uXZut8UoCtOlrqA7gyy0EjdRh1qay1YXIbB
QZxpHDmAy9D3aSDoa5sVwrC1GQzNN4nH58pGnoGF+Df/A76LlZeBfmO1hP/a7hLIf8L+2o4LfKM
NBvqf37tlYDOKUA+mU+XSCmBbMk3/4UgYxuQ3HdE8w5RhFZf9Mbvb5GqubCy7N8zp6v/hRRfT0j
pWqR8kr2qauQttd9+q1n5pKCCjUO+/+jeLDdhtJ7Pls8O7motxJoNsqxKof1lJKvtt44VxYpdoY
K6w== JohnDoe@client
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to restart sshd.
systemctl restart sshd
systemctl status sshd
If your system is using init, use the chkconfig and service commands to restart sshd.
service sshd restart
service sshd status
Now the OpenSSH server has a way to authenticate the client. When the client requests the connection using the private key, the OpenSSH server has the corresponding public certificate.

Make the SSH connection without a password
If connecting using the ssh command, use the -i option followed by the path to the private key.
ssh -i /home/JohnDoe/.ssh/id_rsa JohnDoe@server1.example.com
If connecting using the scp command, use the -i option followed by the path to the private key.
scp -i /home/JohnDoe/.ssh/id_rsa '/home/john.doe/example.jpg' jane.doe@server2:'/home/jane.doe'
If using PuTTY, add the private key to PuTTY.
- Launch PuTTY.
- In the left panel, expand +SSH and highlight auth.
- Enter the path to the private key.
Log files
By default, the LogLevel directive in sshd_config is commented out. You may want to set the log level to VERBOSE when attempting to debug an issue. Since this is a configuration change, you will have to restart the SSHD server for this change to take effect.
LogLevel VERBOSE
The journalctl command can then be used to spot SSH issues. If public key authentication fails, the log should have something like this.
Feb 19 22:28:22 server1 sshd[25196]: Failed publickey for john.doe from 10.45.11.23 port 34522 ssh2: RSA SHA256:ylNytckBXocPLHDNQB6l29WayK787FGm/odk
If public key authentication is successful, the log should have something like this.
Feb 21 05:44:56 dns1 sshd[23955]: Accepted publickey for john.doe from 10.45.11.23 port 34522 ssh2: RSA SHA256:ylNytckBXocPLHDNQB6l29WayK787FGm/odk
For absolute assurance that only a public private key pair are being used for authentication, view the PuTTY log file.
- In PuTTY, select Logging, and select the following:
- SSH packets and raw data
- Type the path to the file that will contain the log data
- Remove the tick from Omit known password fields
Connect to the OpenSSH server, and then open the log file. In the log, the first outgoing packet from the client to the server is ....root....ssh-connection....none, and the incoming packet from the server to the client is ....publickey.....
- publickey means that the server is configured to allow the use of a public key for authentication requests.
- none means that no public key was provided in the request.
Because no public key was provided, the SSH server failed to authenticate the request. This is normal, and not suggestive of some problem. By default, PuTTY makes the first authentication attempt with no public key. Notice publickey and ssh-rsa in the last attempt.
Did you find this article helpful?
If so, consider buying me a coffee over at 