
This assumes you have used the REST API to obtain an OAuth bearer token. Let's say the bearer token is sha256~0Rs__hPuXmBD3TJTXNDisC7wRBN-nrFnYTxgdBrFT-U.
Here is an illustration of how a user, group or service account get mapped to permissions. There are a number of different ways to design this, typically based on your organizations needs.
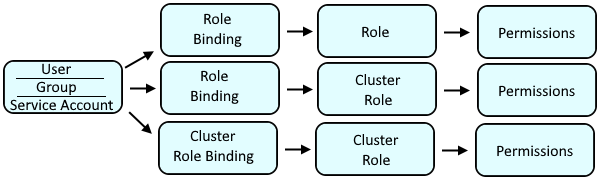
Cluster Role Binding maps a user, group or service account to a Cluster Role which will have policies that allow certain actions (such as create or delete or list) on certain resources (such as deployments, pods)
Role Bindings maps a user, group or service account to a Role or to a Cluster Role which will have policies that allow certain actions (such as create or delete or list) on certain resources (such as deployments, pods)
Cluster Role is often used by a number of different users, groups and service accounts in various projects, thus a Cluster Role contains the default actions (such as list, get, watch) on certain resources (such as deployments, pods) that users, groups, or service accounts are allowed to do across namespaces.
Role if isolated to a user, group or service account in a specific project, as a way of granting specific actions (such as create and delete and update) on certain resources (such as services and routes).
Here is an example of how you could return all role bindings in all namespaces.
curl \
--insecure \
--request GET \
--header "Accept: application/json" \
--header "Authorization: Bearer sha256~0Rs__hPuXmBD3TJTXNDisC7wRBN-nrFnYTxgdBrFT-U" \
--url https://api.openshift.example.com:6443/apis/rbac.authorization.k8s.io/v1/rolebindings
Here is an example of how you could return all cluster role bindings in all namespaces.
curl \
--insecure \
--request GET \
--header "Accept: application/json" \
--header "Authorization: Bearer sha256~0Rs__hPuXmBD3TJTXNDisC7wRBN-nrFnYTxgdBrFT-U" \
--url https://api.openshift.example.com:6443/apis/rbac.authorization.k8s.io/v1/clusterrolebindings
Here is an example of how you could return all role bindings in a specific namespace.
curl \
--insecure \
--request GET \
--header "Accept: application/json" \
--header "Authorization: Bearer sha256~0Rs__hPuXmBD3TJTXNDisC7wRBN-nrFnYTxgdBrFT-U" \
--url https://api.openshift.example.com:6443/apis/rbac.authorization.k8s.io/v1/namespaces/my-project/rolebindings
Here is an example of how you could return a single role bindings in a specific namespace.
curl \
--insecure \
--request GET \
--header "Accept: application/json" \
--header "Authorization: Bearer sha256~0Rs__hPuXmBD3TJTXNDisC7wRBN-nrFnYTxgdBrFT-U" \
--url https://api.openshift.example.com:6443/apis/rbac.authorization.k8s.io/v1/namespaces/my-project/rolebindings/my-role-binding
Here is an example of how you could return a single cluster role binding.
curl \
--insecure \
--request GET \
--header "Accept: application/json" \
--header "Authorization: Bearer sha256~0Rs__hPuXmBD3TJTXNDisC7wRBN-nrFnYTxgdBrFT-U" \
--url https://api.openshift.example.com:6443/apis/rbac.authorization.k8s.io/v1/clusterrolebindings/my-cluster-role-binding
Something like this should be returned.
{
"kind": "RoleBinding",
"apiVersion": "rbac.authorization.k8s.io/v1",
"metadata": {
"name": "my-role-binding",
"namespace": "my-project",
"uid": "a258c923-aa64-45bb-b0d1-51bf3610c7b0",
"resourceVersion": "1570882638",
"creationTimestamp": "2024-01-26T03:59:22Z",
"managedFields": [
{
"manager": "oc",
"operation": "Update",
"apiVersion": "rbac.authorization.k8s.io/v1",
"time": "2024-01-26T03:59:22Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:roleRef": {},
"f:subjects": {}
}
}
]
},
"subjects": [
{
"kind": "Group",
"apiGroup": "rbac.authorization.k8s.io",
"name": "my-group"
}
],
"roleRef": {
"apiGroup": "rbac.authorization.k8s.io",
"kind": "ClusterRole",
"name": "basic-user"
}
}
The following DELETE request could then be used to delete a Role Binding or Cluster Role Binding.
curl \
--insecure \
--request DELETE \
--header "Authorization: Bearer sha256~0Rs__hPuXmBD3TJTXNDisC7wRBN-nrFnYTxgdBrFT-U" \
--url https://api.openshift.example.com:6443/apis/rbac.authorization.k8s.io/v1/namespaces/my-project/rolebindings/my-role-binding
Did you find this article helpful?
If so, consider buying me a coffee over at 