
This assumes you have already configured the aws command line tool. If not, check out my article on Getting Started with the AWS CLI.
An S3 Bucket is similar to an NFS share in that it is a mountable storage volume.
The aws s3control list-access-point command can be used to list the S3 Bucket Access Points in your AWS Account. By default, there are typically no S3 Bucket Access Points.
~]$ aws s3control list-access-points --account-id 123456789012
{
"AccessPointList": []
}
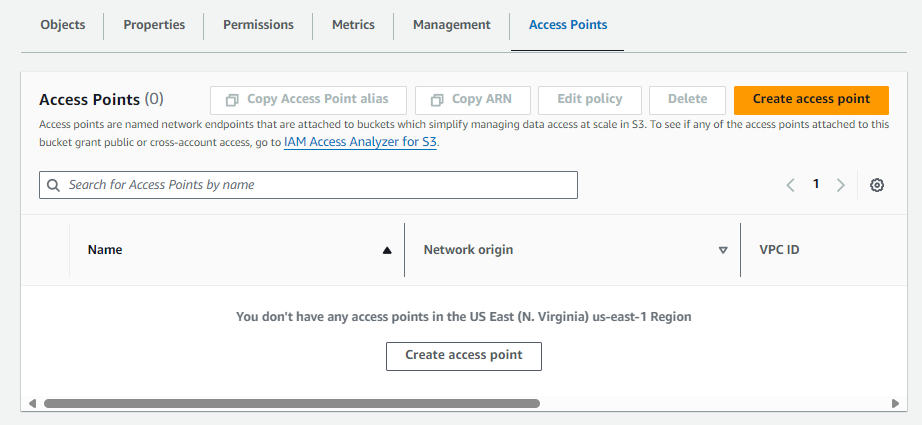
And in the AWS Console, you should see something like this.
The aws s3api list-buckets command can be used to list your S3 buckets.
~]$ aws s3api list-buckets
{
"Buckets": [
{
"Name": "my-bucket-abc123",
"CreationDate": "2023-06-02T02:22:19+00:00"
}
],
"Owner": {
"DisplayName": "john.doe",
"ID": "ab0e0a411234d5103a77c82240d5abcdc41ff11cc325c65b5c777a5123443743"
}
}
The aws s3control create-access-point command without the --vpc-configuration will create an Internet Access Point, meaning the Access Point would be accessible from outside of your Virtual Private Cloud (VPC).
~]$ aws s3control list-access-points --account-id 123456789012
{
"AccessPointList": [
{
"Name": "poc",
"NetworkOrigin": "Internet",
"Bucket": "my-bucket-abc123",
"AccessPointArn": "arn:aws:s3:us-east-1:123456789012:accesspoint/poc",
"Alias": "poc-z6yoa35gxbjnxxwihg5ejrtqm9z7yuse1a-s3alias",
"BucketAccountId": "123456789012"
}
]
}
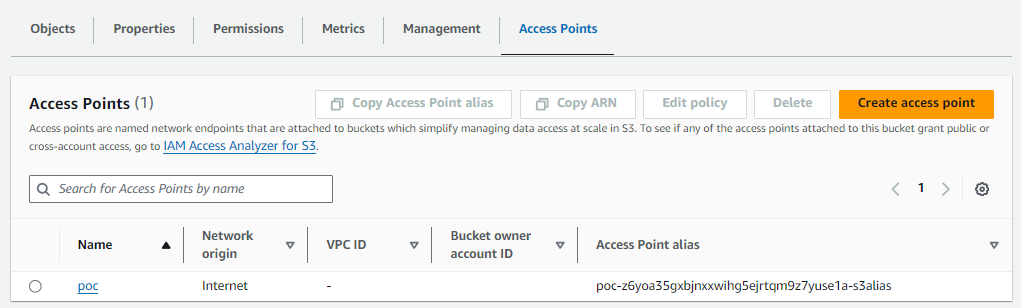
And the AWS Console should look like this, where we can see Network origin is Internet.
The aws s3control create-access-point command with the --vpc-configuration will create a Virtual Private Cloud (VPC) Access Point, meaning the Access Point would only be accessible in your Virtual Private Cloud (VPC).
~]$ aws s3control create-access-point --account-id 123456789012 --bucket my-bucket-abc123 --name poc --vpc-configuration '{"VpcId": "vpc-0a9d4cb29e2748444"}'
{
"AccessPointArn": "arn:aws:s3:us-east-1:123456789012:accesspoint/poc",
"Alias": "poc-yxf5eodcy7nqmqdjqgnj66ci5tcgeuse1a-s3alias"
}
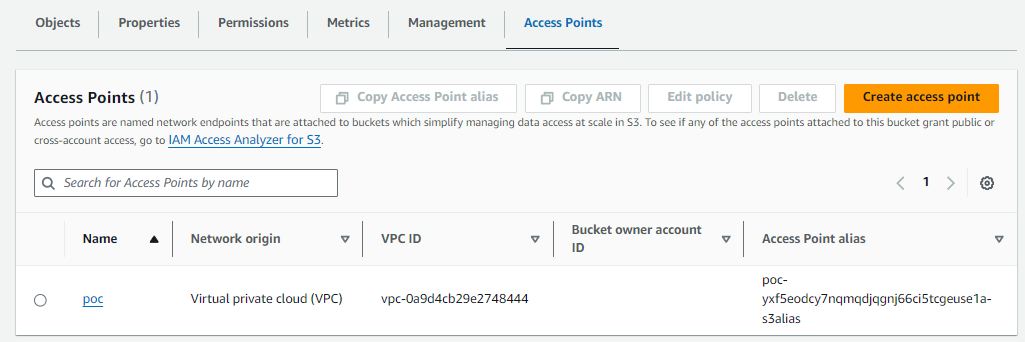
And the AWS Console should look like this, where we can see Network origin is Virtual Private Cloud (VPC).
By default, the Access Point will not have a Permission Policy. The Access Point Permission Policy works in conjunction with the underlying buckets Permission Policy. For example, let's says the underlying bucket has the following Permission Policy, allowing john.doe to get and put objects in the bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:user/john.doe"
},
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::my-bucket-abc123",
"arn:aws:s3:::my-bucket-abc123/*",
]
}
]
}
The Access Point could then have a similar Permission Policy, but would instead only allow getting objects from the bucket, as an additional layer of access control.
{
"Version":"2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:user/john.doe"
},
"Action": ["s3:GetObject"],
"Resource": "arn:aws:s3:us-east-1:123456789012:accesspoint/poc/object/*"
}
]
}
Did you find this article helpful?
If so, consider buying me a coffee over at 