
An IAM (Identity and Access Management) User, Group, or Role may have a Permission Policy and/or a Trust Policy. So, what's the difference?
Let's say you use aws sns list-topics command to list your Simple Notification Service (SNS) Topics.
aws sns list-topics --profile johndoe
Since the --profile option was used, the johndoe profile in your credentials file will be used.
~]$ cat ~/.aws/credentials
[johndoe]
aws_secret_access_key = Xw3kZVaxTfvDKBMGf6R79Unf5LG4kdf9piuHfhn13
aws_access_key_id = 34VGB4HYOC2ABCO67BKD
Let's say the johndoe credential maps to user john.doe, and john.doe does not have any Simple Notification Service (SNS) Permission Policies.
By the way, this is an identity-based policy, where a user account contains Permission Policies.
- A identity-based policy is attached to a User, Group or Role.
- A resource-based policy is attached to a Resource, such as Simple Notification Service (SNS), S3 Bucket, EC2, et cetera
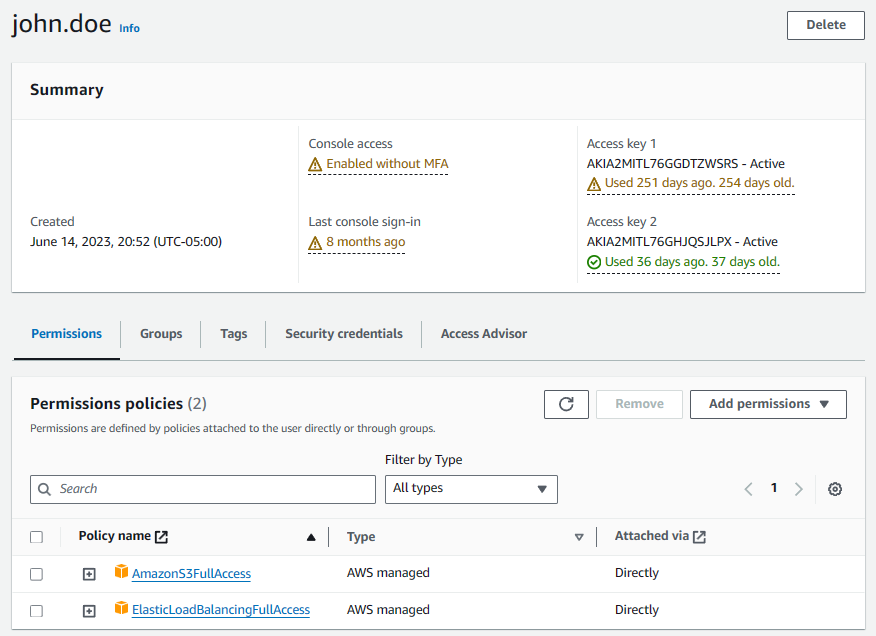
The aws iam list-attached-user-policies command can be used instead of the console.
]$ aws iam list-attached-user-policies --user-name john.doe
{
"AttachedPolicies": [
{
"PolicyName": "ElasticLoadBalancingFullAccess",
"PolicyArn": "arn:aws:iam::aws:policy/ElasticLoadBalancingFullAccess"
},
{
"PolicyName": "AmazonS3FullAccess",
"PolicyArn": "arn:aws:iam::aws:policy/AmazonS3FullAccess"
}
]
}
When attempting to list the Simple Notification Service (SNS) Topics using the aws sns list-topics command, something like this should be returned because john.doe does not have the SNS:ListTopics Permission Policy.
~]$ aws sns list-topics --profile johndoe
An error occurred (AuthorizationError) when calling the ListTopics operation: User: arn:aws:iam::123456789012:user/john.doe is not authorized to perform: SNS:ListTopics on resource: arn:aws:sns:us-east-1:123456789012:* because no identity-based policy allows the SNS:ListTopics action
There are a variety of errors that may be returned if a user attempts to do something on a resource that they don't have have access to.
- Access Denied
- An error occurred (MalformedPolicyDocument) when calling the CreateRole operation: Has prohibited field
- no identity-based policy allows the action
Let's use the aws iam attach-user-policy command to update john.doe to include an SNS Permission Policy that allows SNS:ListTopics.
Be aware that to do this, you will need to use some other profile that has the iam:AttachUserPolicy. For example, this could be done using the root profile which has AdministratorAccess. In this example, I used the root profile, which has AdministratorAccess.
aws iam attach-user-policy --user-name john.doe --policy-arn arn:aws:iam::aws:policy/AmazonSNSReadOnlyAccess --profile root
In the console, we should now see that john.doe has the AmazonSNSReadOnlyAccess Permission Policy.
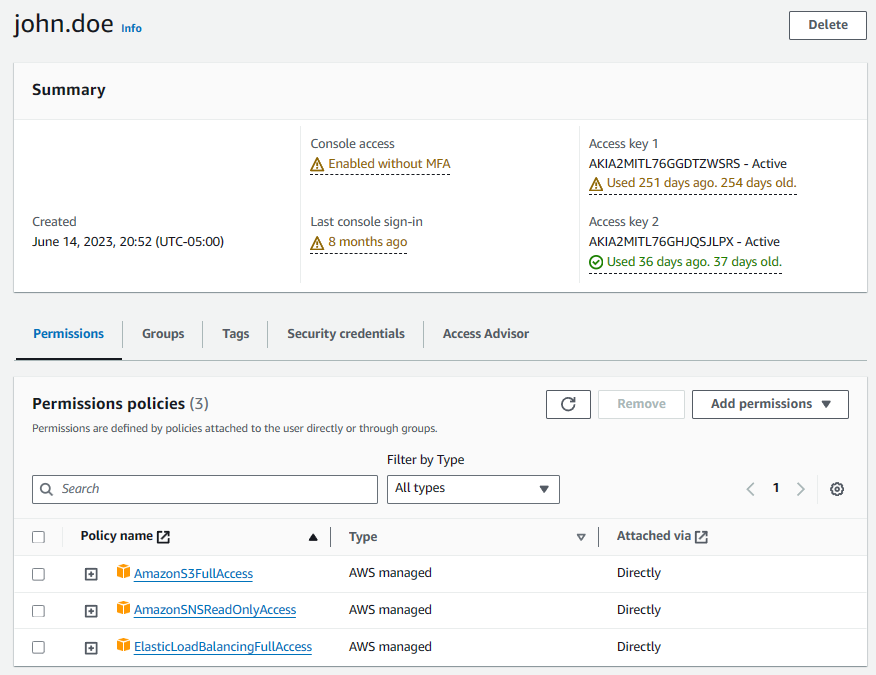
Now, john.doe is able to list the Simple Notification Service (SNS) Topics.
~]$ aws sns list-topics --profile johndoe
{
"Topics": [
{
"TopicArn": "arn:aws:sns:us-east-1:123456789012:my-topic"
}
]
}
In laymen terms, a Permission Policy grants a user permission to do something (such as list, create, delete, et cetera) on a resource (such as a Simple Notification Service (SNS) Topic or EC2 or Elastic Load Balancers, et cetera).
cool.
But what then is a trust policy?
Let's say john.doe does not have any Simple Notification Service (SNS) Permission Policies.

When attempting to list the Simple Notification Service (SNS) Topics using the aws sns list-topics command, something like this should be returned because john.doe does not have the SNS:ListTopics Permission Policy.
~]$ aws sns list-topics --profile johndoe
An error occurred (AuthorizationError) when calling the ListTopics operation: User: arn:aws:iam::123456789012:user/john.doe is not authorized to perform: SNS:ListTopics on resource: arn:aws:sns:us-east-1:123456789012:* because no identity-based policy allows the SNS:ListTopics action
Instead of updating john.doe account to include an SNS Permission Policy that allows SNS:ListTopics, you can instead create a Role that includes an SNS Permission Policy that allows SNS:ListTopics and also a Trust Policy.
For example, I have a Role named my-sns-full-access-role that contains Permission Policy AmazonSNSFullAccess.
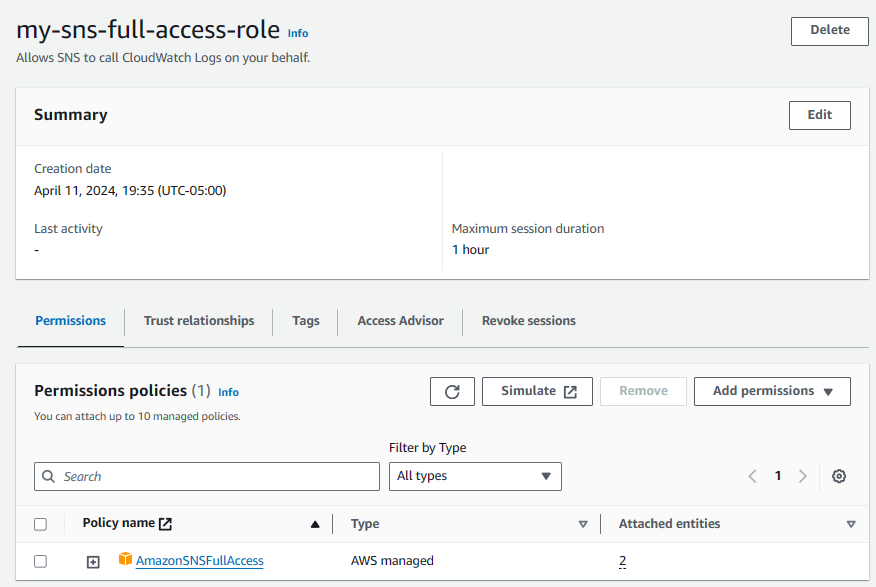
The AmazonSNSFullAccess Policy contains the following JSON.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sns:*"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
And the Role also contains a Trust Policy with the following JSON.
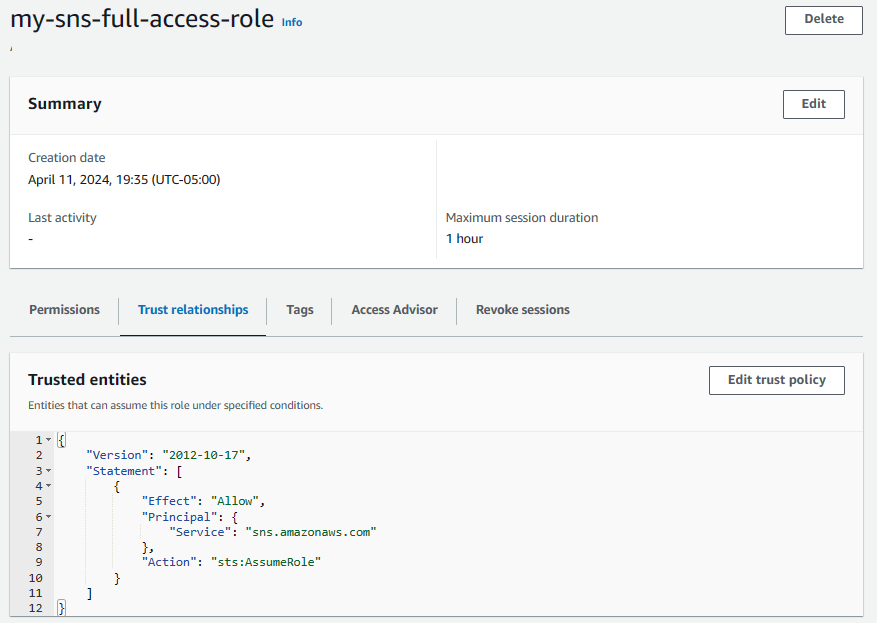
And here is the JSON. Notice in this example that this allows sns.amazonaws.com (Simple Notification Service) via assume role.
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service":"sns.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
Since we are using the AWS CLI in this example, let's update our users .aws/config file with a profile that contains the Amazon Resource Number (ARN) of my-sns-full-access-role.
[profile assume_sns_full_access_role]
role_arn = arn:aws:iam::123456789012:role/my-sns-full-access-role
source_profile = johndoe
region = us-east-1
output = json
Now, when attempting to list the Simple Notification Service (SNS) Topics using the aws sns list-topics command with --profile johndoe, the same error is returned because john.doe still does not have the SNS:ListTopics Permission Policy.
~]$ aws sns list-topics --profile johndoe
An error occurred (AuthorizationError) when calling the ListTopics operation: User: arn:aws:iam::123456789012:user/john.doe is not authorized to perform: SNS:ListTopics on resource: arn:aws:sns:us-east-1:123456789012:* because no identity-based policy allows the SNS:ListTopics action
However, if using assume_sns_full_access_role, then john.doe will assume the my-sns-full-access-role, and like majic, john.doe is able to list the Simple Notification Service (SNS) Topics. Awesome!
~]$ aws sns list-topics --profile assume_sns_full_access_role
{
"Topics": [
{
"TopicArn": "arn:aws:sns:us-east-1:123456789012:my-topic"
}
]
}
By the way, this is the concept of assuming a role.
- Assume Role or Switch Role using the AWS CLI
- Assume Role or Switch Role using Python boto3
- Assume Role or Switch Role using Terraform
Did you find this article helpful?
If so, consider buying me a coffee over at 