
Long round trip time (RTT) during the 3 way handshake could result in an application taking a long time to respond. To identify long RTT in Wireshark, ensure the Time column in Wireshark is configured to display the time since the previous displayed packet.
- Select View > Time Display Format > Seconds Since Previous Displayed Packet.
It can also be helpful to configure the Time column to only display milliseconds instead of nanoseconds.
- Select View > Time Display Format > Milliseconds: 0.123.
If the capture was done on the client, view the value in the time column of the SYN, ACK packet from the server to the client. The value in this packet is the RTT. In this example, the RTT time is 0.018 ms, which is an extremely fast RTT.
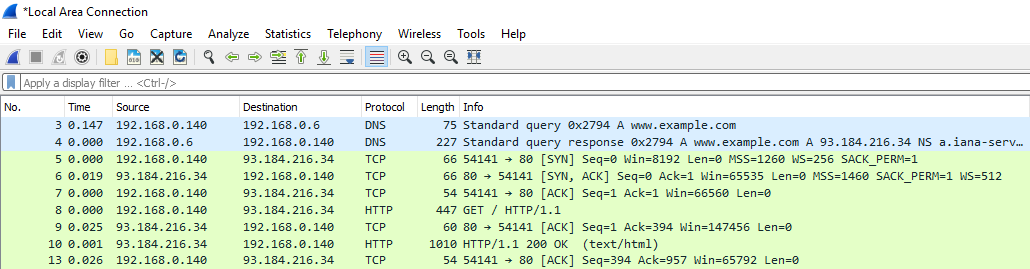
To determine if the RTT is higher than normal, you will need to know what the RTT baseline is. If the RTT is much higher than the RTT baseline, then there is RTT latency.
If the traffic between the client and server is isolated to your network, you should be able to identify the cause of the latency and do something about it. If the traffic between the client and server includes Internet traffic, you may not be able to do anything about the latency, because the latency may be with the Internet routers. When there is high RTT, you can check for a firewall with a very high number of rules. The more rules a firewall has, the more time it will take packets to traverse through a firewall.
Did you find this article helpful?
If so, consider buying me a coffee over at 