
If you are not familiar with the oc command, refer to OpenShift - Getting Started with the oc command.
There are different ways to configure a container with environment variables.
- In a deployment YAML file
- Using Config Map
- Using Secrets (this article)
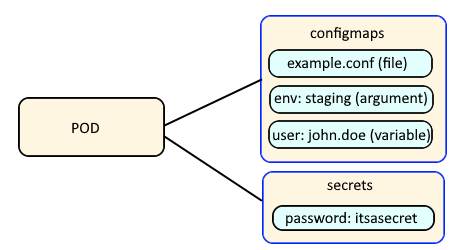
Config Maps are used to:
- mount configuration files in a container
- create environment variables in a container
- create command line option arguments in a container
Secrets are similar, used to create variables that contain encoded data (e.g. passwords). In this way, if a change is needed to a configuration file, variable, or command line option argument, you just need to update the config map or secret as opposed to having to make the change to your applications or deployments.
The oc get secrets command can be used the list the secrets in the currently selected project / namespace.
TIP
The -A or --all-namespaces flag can be used to list the secrets in every project / namespace.
The -n or --namespace flag can be used to list the secrets in a certain project / namespace.
~]# oc get secrets
NAME TYPE DATA AGE
my-secret1 Opaque 1 133d
my-secret2 kubernetes.io/tls 1 133d
my-secret3 kubernetes.io/service-account-token 1 127d
The oc get secret command followed by the name of a secret can be used to display an individual secret.
~]# oc get secret my-secret
NAME TYPE DATA AGE
my-secret Opaque 1 133d
The -o or --output yaml option can be used to display the contents of the secret. In this example, the secret contains a key named "myKey" and the key contains an encrypted value of "anRwL7VzZ4JpZDxna1F2dpFt9HNw7HZ0cK5wYXlzd29aZD1TTnMjZG75Rwa=".
~]# oc get secret my-secret --output yaml
apiVersion: v1
data:
my-key: SXQncyBhIFNlY3JldAo=
kind: Secret
metadata:
creationTimestamp: "2020-02-03T17:02:04Z"
name: my-secret
namespace: my-project
resourceVersion: "74792019"
selfLink: /api/v1/namespaces/my-project/secrets/my-secret
uid: e6e760ae-46a6-11aa-9928-005056a39855
type: Opaque
The encrypted value can be decrypted using this command, which will return the cleartext secret.
echo SXQncyBhIFNlY3JldAo= | base64 --decode
Better yet, this one liner can be used.
oc get secret my-secret --output jsonpath="{.data.my-key}" | base64 --decode
Did you find this article helpful?
If so, consider buying me a coffee over at 