
This error appears in the web servers error log.
[Thu Feb 25 03:01:13.289527 2021] [ibm_ssl:error] [pid 17385:tid 139648960628480] [client 10.17.114.22:56618] [7f0280002920] [17385] SSL0208E: SSL Handshake Failed, Certificate validation error.[10.17.114.22:56618 -> 10.17.122.5:443]
As the error suggests, there is some SSL issue.
For the sake of this article, let's say you have a Key Database file named example.kdb. The GSKit command or iKeyman GUI can be used to list the certificates in the Key Database file (example.kdb). Let's say you are using the GSKit command, and the Key Database contains a certificate, such as *.example.com.
${ihs_install_root}/gsk8/bin/gsk8capicmd_64 -cert -list -db /path/to/example.kdb -stashed
Certificates found
* default, - personal, ! trusted, # secret key
*- *.example.com
Has the certificate expired?
Display the details of the certificate to ensure the certificate has not expired.
~]# ${install_root}/gsk8/bin/gsk8capicmd_64 -cert -details -db /path/to/example.kdb -pw your_password -label *.example.com
Label : example
Key Size : 2048
Version : X509 V3
Serial : abc123
Issuer : "CN=Some CA,O=CA Inc,C=US"
Subject : "CN=*.example.com,O=Your Organization,L=Guam,ST=Wisconsin,C=US"
Not Before : January 19, 2021 6:00:00 PM CST
Not After : February 20, 2022 5:59:59 PM CST
Is there a certificate chain?
A certificate chain contains the collection of root, intermediate and server certificates. In this example, root.example.com is the root certificate authority (CA). Typically, one or more intermediate certificates are children of the root CA, and one or more server certificates are children of the intermediate certificate. OpenSSL can be used to create a file that contains the root, intermediate and server certificate chain.
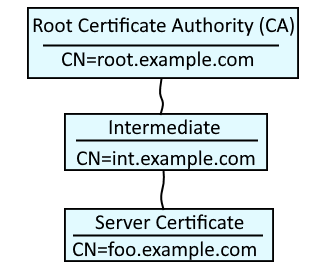
Notice in this example that the KDB file contains three certificates, which makes up the certificate chain.
${ihs_install_root}/gsk8/bin/gsk8capicmd_64 -cert -list -db /path/to/example.kdb -stashed
Certificates found
* default, - personal, ! trusted, # secret key
! root_certificate
! intermediate_certificate
*- *.example.com
Determine the Issuer of the "server" certificate. In this example, the "server" certificate (*.example.com) is issued by the "CN=Foo Intermediate,O=CA Inc,C=US" certificate.
~]# ${install_root}/gsk8/bin/gsk8capicmd_64 -cert -details -db /path/to/example.kdb -pw your_password -label *.example.com
Issuer : "CN=Foo Intermediate,O=CA Inc,C=US"
In this example, you want to confirm that the subject of the intermediate certificate is an exact match of the issuer of the server certificate (CN=Foo Intermediate,O=CA Inc,C=US). If not, then you'll have to import the intermediate certificate into the KDB file. If the intermediate certificate subject has a CN of "Foo Intermediate", then you'll want to make note of the issuer of the intermediate certifiate. In this example, the intermediate certificate is issued by "Foo Root CA".
~]# ${install_root}/gsk8/bin/gsk8capicmd_64 -cert -details -db /path/to/example.kdb -pw your_password -label intermediate_certificate
Issuer : "CN=Foo Root CA,O=CA Inc,C=US"
Subject : "CN=Foo Intermediate,O=CA Inc,C=US"
In this example, you want to confirm that the root certificate has a CN of "Foo Root CA". If not, then you'll have to import the "Foo Root CA" certificate into the KDB file.
~]# ${install_root}/gsk8/bin/gsk8capicmd_64 -cert -details -db /path/to/example.kdb -pw your_password -label root_certificate
Subject : "CN=Foo Root CA,O=CA Inc,C=US"
Is the httpd.conf file using default or specific certificate?
Notice in this example that the httpd.conf file does not include the SSLServerCert directive. In this scenario, the httpd.conf file will use the default certificate in the KDB file.
LoadModule ibm_ssl_module modules/mod_ibm_ssl.so
Listen 443
<VirtualHost *:443>
SSLEnable
</VirtualHost>
SSLDisable
KeyFile "/path/to/example.kdb"
SSLStashFile "/path/to/example.sth"
In this scenario, the httpd.conf file will use the SSLServerCert certificate.
LoadModule ibm_ssl_module modules/mod_ibm_ssl.so
Listen 443
<VirtualHost *:443>
SSLEnable
SSLServerCert *.example.com
</VirtualHost>
KeyFile "/path/to/example.kdb"
SSLStashFile "/path/to/example.sth"
SSLDisable
Did you find this article helpful?
If so, consider buying me a coffee over at 