
Let's say you have created an API Gateway. By default, the API Gateway will NOT log events to CloudWatch. To update an API Gateway to log events to CloudWatch, first you'll have to create an IAM (Identity and Access Management) Roles with a Permission Policy and Trust Policy that will allow the API Gateway to append it's logs to CloudWatch.
Let's create a file with the following JSON. It can be named anything, such as my.json. Notice this will allow the apigateway.amazonaws.com service to assume the role. This is a Trust Policy. It's basically a way of saying "I trust you" or "I trust the apigateway.amazonaws.com service.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "apigateway.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
And then the aws iam create-role command can be used to create the role.
aws iam create-role --role-name my-role --assume-role-policy-document file://my.json
And then the aws iam attach-role-policy can be used to attach the AmazonAPIGatewayPushToCloudWatchLogs Permission Policy to the role.
aws iam attach-role-policy --policy-arn arn:aws:iam::aws:policy/AmazonAPIGatewayPushToCloudWatchLogs --role-name my-role
Then in the AWS console, you can go to Settings to update your API Gateway with the role.
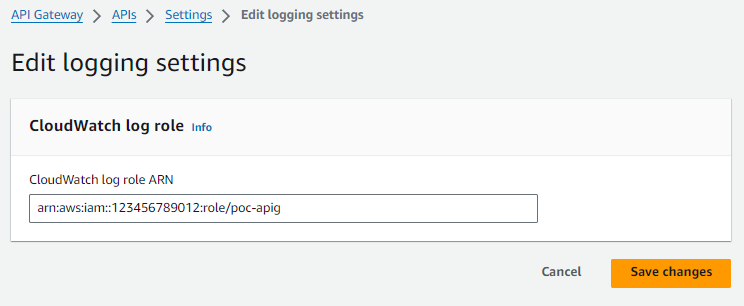
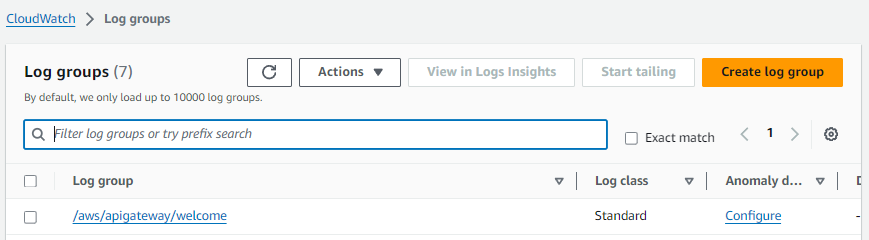
You should see something like this over in CloudWatch. This simply just confirms that CloudWatch is enabled for your API Gateways.
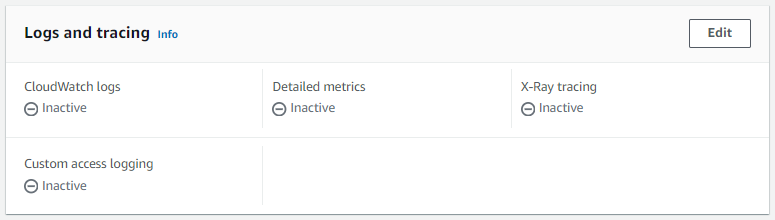
But this will not log actual GET/POST requests to your API Gateway. In your API Gateway Stage, by default, CloudWatch logs are Inactive. Click on Edit and update this to Active.
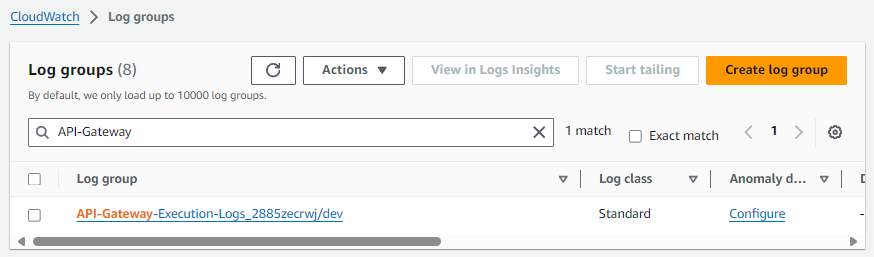
Now there should be another log group in CloudWatch for your API Gateway API.
Did you find this article helpful?
If so, consider buying me a coffee over at 