
By default, resources in different Virtual Private Clouds (VPCs) are isolated from each other and cannot communicate with each other. The resources in different Virtual Private Clouds (VPCs) would need to use something like an Internet Gateway to communicate. For example, an EC2 instance in one Virtual Private Cloud (VPC) would have to send traffic onto the Internet via an Internet Gateway to talk to an EC2 instance in a different Virtual Private Clouds (VPC).
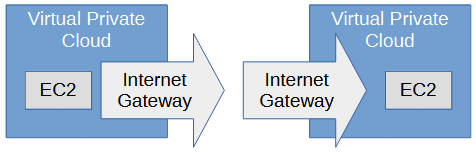
There are different ways for resources (such as EC2 instances) in different Virtual Private Clouds to communicate without having to use an Internet Gateway.
- VPC Peering (this article)
- Transit Gateway
For example, let's create two VPCs.
- foo-vpc
- bar-vpc
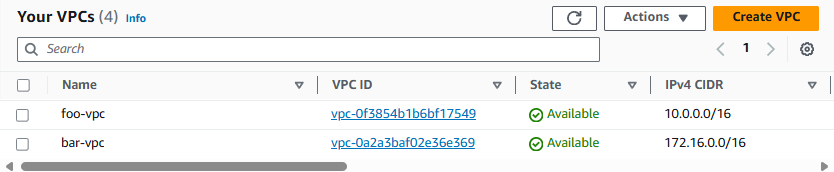
By default, a VPC will only have a local route and no Internet Gateway, so let's create an Internet Gateway for foo-vpc and bar-vpc. By default, the Internet Gateways will not be attached to any VPCs.
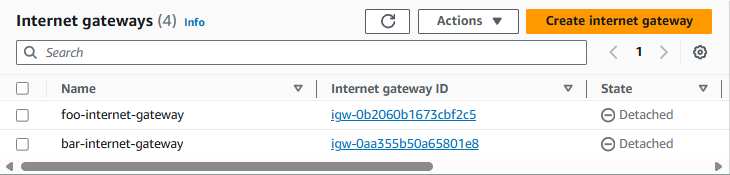
Let's attach the foo-internet-gateway to foo-vpc.
aws ec2 attach-internet-gateway --internet-gateway-id igw-0b2060b1673cbf2c5 --vpc-id vpc-0f3854b1b6bf17549
And attach the bar-internet-gateway to bar-vpc.
aws ec2 attach-internet-gateway --internet-gateway-id igw-0aa355b50a65801e8 --vpc-id vpc-0a2a3baf02e36e369
Now each Internet Gateway should be attached to each VPC.
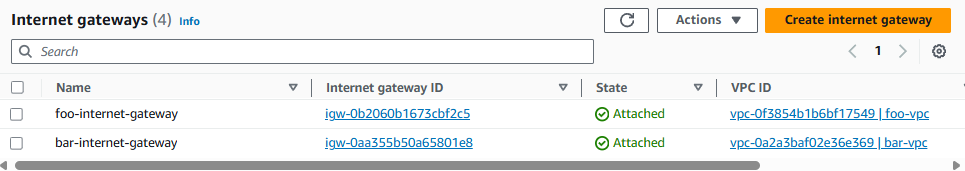
The Route Table in the Subnets in foo-vpc and bar should only have a local route.
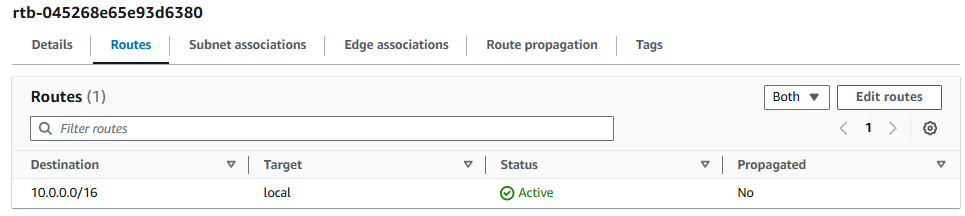
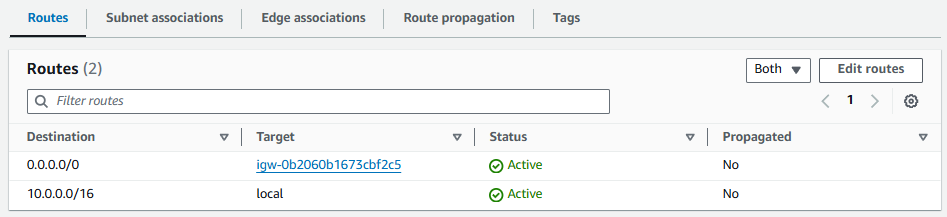
Let's update the Route Table being used by foo-vpc to have a route to the foo-internet-gateway.
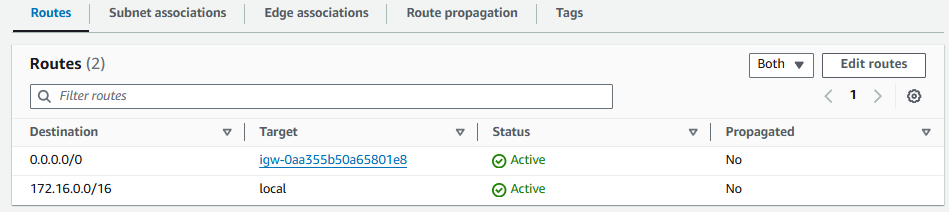
And let's update the Route Table being used by bar-vpc to have a route to the bar-internet-gateway.
Let's create an EC2 instance in foo-vpc and bar-vpc.
And update the Security Group being used by each EC2 instance to allow SSH connections from your local public IP address. In this example, my local public IP address was 65.17.88.90. You would instead use your local public IP address.
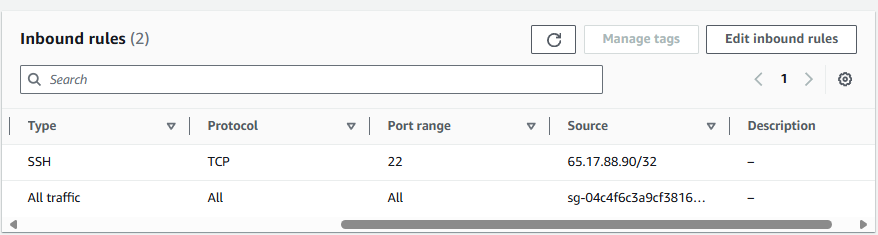
And you should now be able to SSH onto the EC2 instance in foo-vpc.
Using username "ec2-user".
Authenticating with public key "aws"
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Wed May 1 00:12:12 2024 from 65.17.88.90
[ec2-user@ip-10-0-4-185 ~]$
And the EC2 instance in bar-vpc. Nice!
Using username "ec2-user".
Authenticating with public key "aws"
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Wed May 1 00:12:12 2024 from 65.17.88.90
[ec2-user@ip-172-16-14-14 ~]$
On the EC2 instance in foo-vpc, there should be a public SSH key such as id_rsa.pub.
[ec2-user@ip-10-0-0-5 ~]$ cat /home/ec2-user/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDbhEwnvPWnCUthZh/pIhGm2/wHlpEcla4GNKvnti9voszQPQjZw9kksUOKW9ZQ5Ez24mrDmA8djUnwO9lKFZSM/qPfzVpeMkp6e6gYLD8yEmbepC8/TbgxuMa1He+jEFh7SXcaQwx6/Qx1/+RSFh+BcuaCoIJQumhsBuPKyNMknluRmxdU2aHzKjTlSdIzV1I6JmLvhqgFsD6JT3LJotEHNdpjFnu4nWSsFWfRFHKswtwoXvlQWH0g3Kz3fkmqnBSxcB+nCNmsy+zJ82WMBfLKl3UCUrcvjaJWgPSPfck9bB8zwEcixAszG+Atm7CRfg/oUebSauj93XKzgijXgnK3ZbM0nC8uB/l6S5OtbYxdBEalnh/Q/knS1xTItabrBuApQAc+aOR8Ah9hNV2PPVYHmQTuaXbyjTiU6KqERoABazfl0dYwjUq3ZnOJla749z6nqfYN1/2p7E6sCci08H2GbueiS75gufFDHvORpAgsabY/xNyNB5+FAVHJYoI9SeF2Lxp2WVc5I9GcymWQgtgec/yW/gl0TBmFhS1o4ybPOjSUor3UiDBnEXaxIyhPR0gQnpW6Y6s2VYKPeFRO1VKoJ0F/xv8I095OVskn2/j1qtN2OMXQQG7Y7InBzgg+PUdIGC/XxO/G7vAXmcOqKhX1RilVHb/iZEHU2NzDFQIe7w== ec2-user@ip-10-0-0-5.ec2.internal
Let's append the content of id_rsa.pub from the EC2 instance in foo-vpc to the /home/ec2-user/.ssh/authorized_keys file on the EC2 instance in bar-vpc.
[ec2-user@ip-172-31-0-5 ~]$ cat /home/ec2-user/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDbhEwnvPWnCUthZh/pIhGm2/wHlpEcla4GNKvnti9voszQPQjZw9kksUOKW9ZQ5Ez24mrDmA8djUnwO9lKFZSM/qPfzVpeMkp6e6gYLD8yEmbepC8/TbgxuMa1He+jEFh7SXcaQwx6/Qx1/+RSFh+BcuaCoIJQumhsBuPKyNMknluRmxdU2aHzKjTlSdIzV1I6JmLvhqgFsD6JT3LJotEHNdpjFnu4nWSsFWfRFHKswtwoXvlQWH0g3Kz3fkmqnBSxcB+nCNmsy+zJ82WMBfLKl3UCUrcvjaJWgPSPfck9bB8zwEcixAszG+Atm7CRfg/oUebSauj93XKzgijXgnK3ZbM0nC8uB/l6S5OtbYxdBEalnh/Q/knS1xTItabrBuApQAc+aOR8Ah9hNV2PPVYHmQTuaXbyjTiU6KqERoABazfl0dYwjUq3ZnOJla749z6nqfYN1/2p7E6sCci08H2GbueiS75gufFDHvORpAgsabY/xNyNB5+FAVHJYoI9SeF2Lxp2WVc5I9GcymWQgtgec/yW/gl0TBmFhS1o4ybPOjSUor3UiDBnEXaxIyhPR0gQnpW6Y6s2VYKPeFRO1VKoJ0F/xv8I095OVskn2/j1qtN2OMXQQG7Y7InBzgg+PUdIGC/XxO/G7vAXmcOqKhX1RilVHb/iZEHU2NzDFQIe7w== ec2-user@ip-10-0-0-5.ec2.internal
And vice versa. Let's the content of id_rsa.pub from the EC2 instance in bar-vpc to the /home/ec2-user/.ssh/authorized_keys file on the EC2 instance in foo-vpc.
But when attempting to SSH from the EC2 instance in foo-vpc to the EC2 instance in bar-vpc, the SSH connection should eventually time out. And vice versa, when attempting to SSH from the EC2 instance in bar-vpc to the EC2 instance in foo-vpc, the SSH connection should eventually time out. Because we have not yet created and setup a Virtual Private Cloud (VPC) Peering Connection to allows communication between resources in foo-vpc and bar-vpc.
[ec2-user@ip-10-0-4-185 ~]$ ssh -o ConnectTimeout=5 ec2-user@172.16.14.14
ssh: connect to host 172.16.14.14 port 22: Connection timed out
In the AWS console, let's select Virtual Private Clouds > Peering connections > Create peering connection.
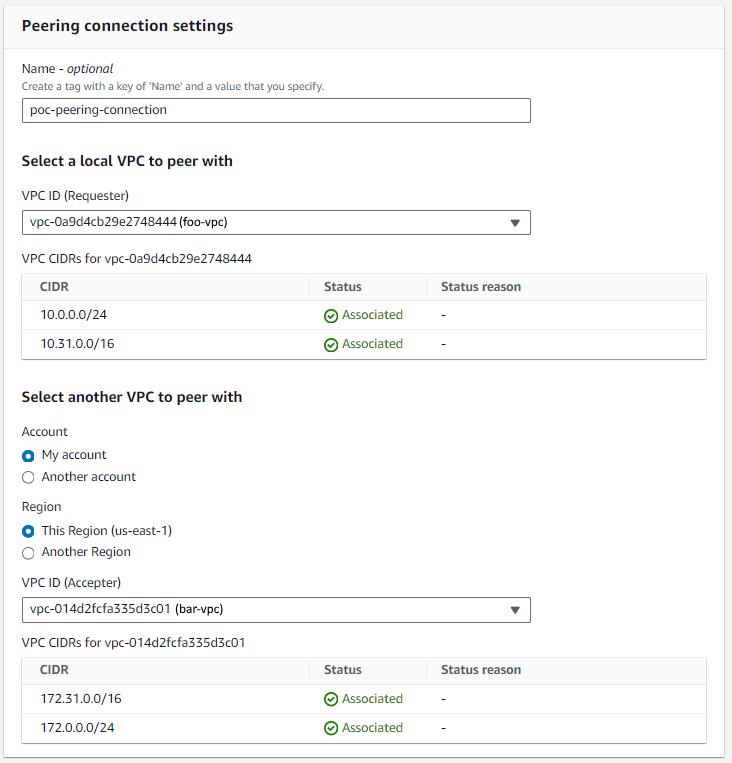
And then let's create a peering connection from foo-vpc to bar-vpc.
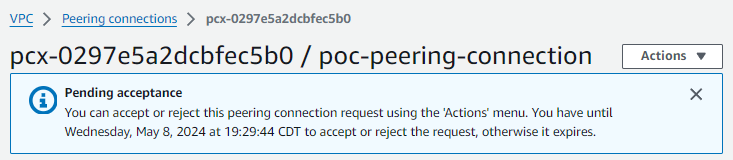
You will then need to accept the peering connection request.
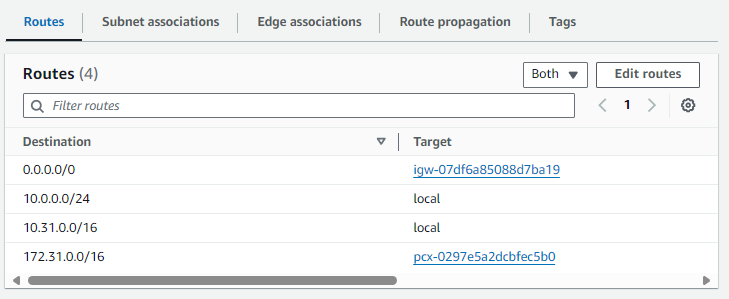
The Route Table being used by the EC2 instance in foo-vpc will need to be updated with a peering connection route to bar-vpc. For example, let's say the EC2 instance in foo-vpc has an IP address 172.31.0.5, which means the IP address is in CIDR 172.31.0.0/16. In this scenario, the Route Table being used by the EC2 instance in bar-vpc would need a peering connection to CIDR 172.31.0.0/16.
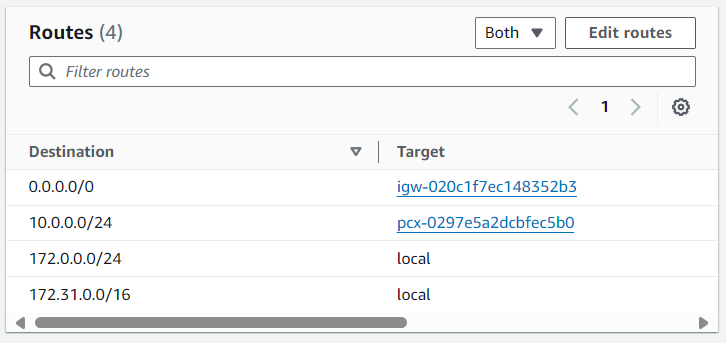
Likewise, the Route Table being used by the EC2 instance in bar-vpc will need to be updated with a peering connection route to foo-vpc. For example, let's say the EC2 instance in foo-vpc has an IP address 10.0.0.5 which means the IP address is in CIDR 10.0.0.0/24. In this scenario, the Route Table being used by the EC2 instance in foo-vpc would need a peering connection to CIDR 10.0.0.0/24.
Since what we are trying to do here is to make an SSH connection from the EC2 instance in bar-vpc to the EC2 instnace in foo-vpc the Security Group attached to the EC2 instance in bar-vpc will need to allow SSH connections from the EC2 instance in foo-vpc.
This is often done by adding a Security Group rule to the Security Group attached to the EC2 instance in foo-vpc that allows SSH connections from the Security Group attached to the EC2 instance in bar-vpc.
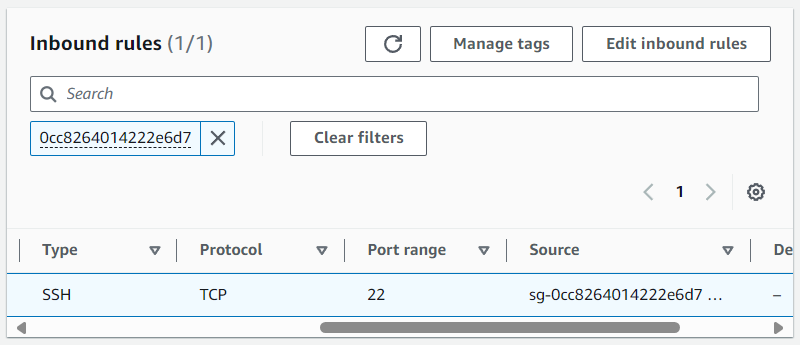
In this example the Security Group being used by the EC2 instance is sg-0cc8264014222e6d7 so I updated the Security Group being used by EC2 instance in foo-vpc to allow SSH connections from sg-0cc8264014222e6d7.
On the EC2 instance in bar-vpc, there should be a public SSH key such as id_rsa.pub.
[ec2-user@ip-10-0-0-5 ~]$ cat /home/ec2-user/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDbhEwnvPWnCUthZh/pIhGm2/wHlpEcla4GNKvnti9voszQPQjZw9kksUOKW9ZQ5Ez24mrDmA8djUnwO9lKFZSM/qPfzVpeMkp6e6gYLD8yEmbepC8/TbgxuMa1He+jEFh7SXcaQwx6/Qx1/+RSFh+BcuaCoIJQumhsBuPKyNMknluRmxdU2aHzKjTlSdIzV1I6JmLvhqgFsD6JT3LJotEHNdpjFnu4nWSsFWfRFHKswtwoXvlQWH0g3Kz3fkmqnBSxcB+nCNmsy+zJ82WMBfLKl3UCUrcvjaJWgPSPfck9bB8zwEcixAszG+Atm7CRfg/oUebSauj93XKzgijXgnK3ZbM0nC8uB/l6S5OtbYxdBEalnh/Q/knS1xTItabrBuApQAc+aOR8Ah9hNV2PPVYHmQTuaXbyjTiU6KqERoABazfl0dYwjUq3ZnOJla749z6nqfYN1/2p7E6sCci08H2GbueiS75gufFDHvORpAgsabY/xNyNB5+FAVHJYoI9SeF2Lxp2WVc5I9GcymWQgtgec/yW/gl0TBmFhS1o4ybPOjSUor3UiDBnEXaxIyhPR0gQnpW6Y6s2VYKPeFRO1VKoJ0F/xv8I095OVskn2/j1qtN2OMXQQG7Y7InBzgg+PUdIGC/XxO/G7vAXmcOqKhX1RilVHb/iZEHU2NzDFQIe7w== ec2-user@ip-10-0-0-5.ec2.internal
Let's append the content of id_rsa.pub from the EC2 instance in bar-vpc to the /home/ec2-user/.ssh/authorized_keys file on the EC2 instance in foo-vpc.
[ec2-user@ip-172-31-0-5 ~]$ cat /home/ec2-user/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDbhEwnvPWnCUthZh/pIhGm2/wHlpEcla4GNKvnti9voszQPQjZw9kksUOKW9ZQ5Ez24mrDmA8djUnwO9lKFZSM/qPfzVpeMkp6e6gYLD8yEmbepC8/TbgxuMa1He+jEFh7SXcaQwx6/Qx1/+RSFh+BcuaCoIJQumhsBuPKyNMknluRmxdU2aHzKjTlSdIzV1I6JmLvhqgFsD6JT3LJotEHNdpjFnu4nWSsFWfRFHKswtwoXvlQWH0g3Kz3fkmqnBSxcB+nCNmsy+zJ82WMBfLKl3UCUrcvjaJWgPSPfck9bB8zwEcixAszG+Atm7CRfg/oUebSauj93XKzgijXgnK3ZbM0nC8uB/l6S5OtbYxdBEalnh/Q/knS1xTItabrBuApQAc+aOR8Ah9hNV2PPVYHmQTuaXbyjTiU6KqERoABazfl0dYwjUq3ZnOJla749z6nqfYN1/2p7E6sCci08H2GbueiS75gufFDHvORpAgsabY/xNyNB5+FAVHJYoI9SeF2Lxp2WVc5I9GcymWQgtgec/yW/gl0TBmFhS1o4ybPOjSUor3UiDBnEXaxIyhPR0gQnpW6Y6s2VYKPeFRO1VKoJ0F/xv8I095OVskn2/j1qtN2OMXQQG7Y7InBzgg+PUdIGC/XxO/G7vAXmcOqKhX1RilVHb/iZEHU2NzDFQIe7w== ec2-user@ip-10-0-0-5.ec2.internal
And we should now be able to make the SSH connection from the EC2 instance in bar-vpc to the EC2 instance in foo-vpc. It works!
[ec2-user@ip-10-0-0-5 ~]$ ssh -i /home/ec2-user/.ssh/id_rsa ec2-user@172.31.0.5
, #_
~\_ ####_ Amazon Linux 2
~~ \_#####\
~~ \###| AL2 End of Life is 2025-06-30.
~~ \#/ ___
~~ V~' '->
~~~ / A newer version of Amazon Linux is available!
~~._. _/
_/ _/ Amazon Linux 2023, GA and supported until 2028-03-15.
_/m/' https://aws.amazon.com/linux/amazon-linux-2023/
[ec2-user@ip-172-31-0-5 ~]$
Did you find this article helpful?
If so, consider buying me a coffee over at 