
There are a couple ways to get the OpenShift API Server public certificates.
- Using the openssl s_client command
- Using oc and OpenSSL commands
- Using the OpenShift console and OpenSSL command (this article)
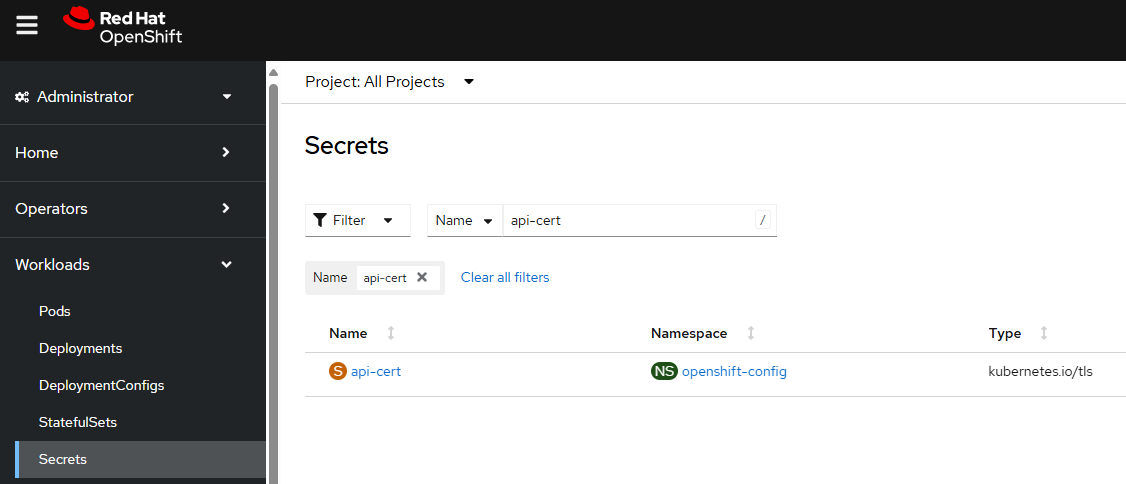
In the OpenShift console, at Workloads > Secrets there should be a secret named api-cert in the openshift-config namespace.
The details of the api-cert secret should contain a few different keys, the Certificate Authority certificate (ca.crt), the public certificate chain (tls.crt) and the private key (tls.key).
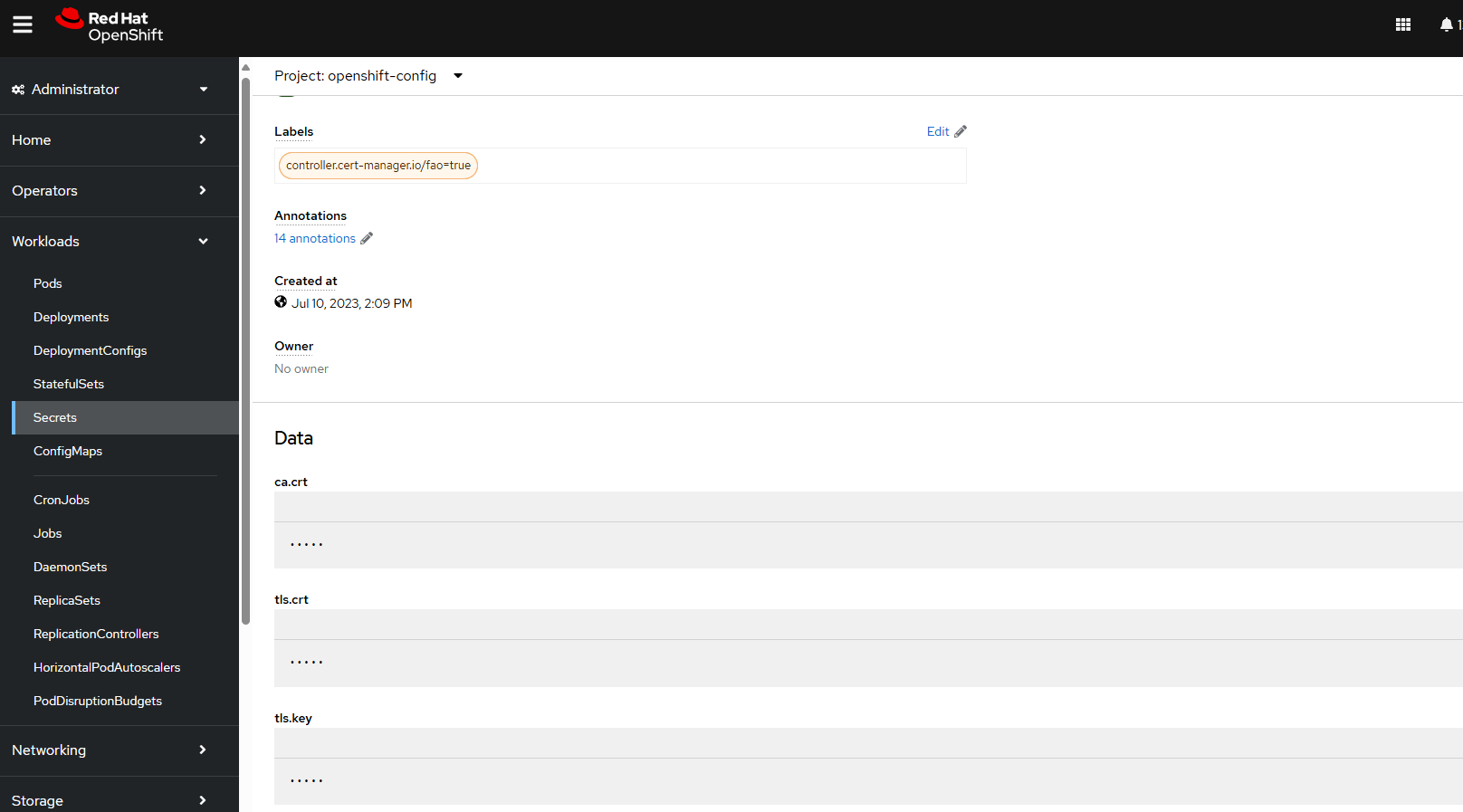
You can copy the content of ca.crt or tls.crt to your clipboard and then create a file containing the clipboard content. For example, let's say you create a file on a Linux system named ca.crt that contains the clipboard content of ca.crt. The ca.crt file would contain something like this.
-----BEGIN CERTIFICATE-----
MIIGeDCC...vvnEPb7hvJasdfasdfasdfadfscKeDKA==
-----END CERTIFICATE-----
The openssl CLI can be used to view the human readable certificate content.
openssl x509 -in ca.crt -text -noout
Which should return something that begins like this.
Certificate:
Data:
Version: 3 (0x2)
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC = com, DC = example
Validity
Not Before: Jun 18 12:59:36 2024 GMT
Not After : Jun 18 12:59:36 2025 GMT
Subject: C = US, ST = CA, L = Los Angeles, O = Example, OU = Information Technology, CN = api.openshift.example.com
Did you find this article helpful?
If so, consider buying me a coffee over at 