
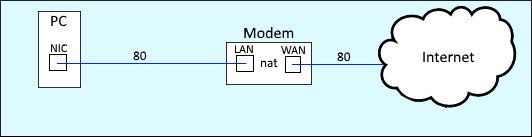
Let's take an example of a PC in your LAN that wants to go to an HTTP website being hosted on a remote server on the Internet. In the most basic configuration possible, you could connect your PC to your modem, and then request the HTTP website. When HTTP is being used, the connection would use port 80.
Building upon this simple configuration, a proxy server could be placed between your PC and your modem, to proxy requests to and from the Internet. In order to configure Squid to be a transparent proxy, the Squid server will need to have at least two interfaces. The interfaces will be configured to forward traffic to and from each interface, and there will also be a configuration to forward traffic from a standard port, such as 80 for HTTP to a new port, such as 3128 (the default Squid http port).
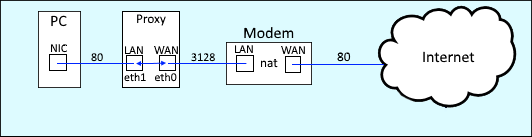
What you will want to do is to configure the LAN interface with a private IP address and subnet mask, but not default gateway. The WAN interface will be configured with a private IP address, subnet mask, and default gateway. For example:
| Tytpe | Interface | IP address | Prefix | Gateway |
|---|---|---|---|---|
| WAN | eth0 | 192.168.0.2 | /24 | 192.168.0.1 |
| LAN | eth1 | 192.168.0.3 | /24 | n/a |
Ensure each interface is working as expected. To test the LAN interface, bring down the WAN interface or disconnect the ethernet cable from the WAN interface. Then, ensure you are able to ping another device in your LAN, but that you are not able to ping a remote server, such as www.google.com.
~]# ping -c1 www.google.com
connect: Network is unreachable
Next ensure the WAN interface is working as expected. Bring down the LAN interface or disconnect the ethernet cable from the LAN interface. Then, ensure you are able to ping another device in your LAN, and that you are also able to ping a remote server, such as www.google.com.fOnce the WAN interface is configured and connected to your router, you will be able to ping remote servers, such as google.
~]# ping -c4 www.google.com
64 bytes from ord38s01-in-f4.1e100.net (172.217.6.4): icmp_seq=1 ttl=55 time=21.9ms
64 bytes from ord38s01-in-f4.1e100.net (172.217.6.4): icmp_seq=2 ttl=55 time=19.0ms
64 bytes from ord38s01-in-f4.1e100.net (172.217.6.4): icmp_seq=3 ttl=55 time=18.9ms
64 bytes from ord38s01-in-f4.1e100.net (172.217.6.4): icmp_seq=4 ttl=55 time=20.6ms
Forwarding
By default, Linux is not configured to forward traffic from one NIC interface to another. We need the system so that requests to the LAN interface are forwarded to the WAN interface. In this example, HTTP requests on port 80 will be forwarded from the LAN to the WAN interface, and the WAN interface will use the default Squid port 3128.
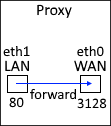
In the /etc/sysctl.conf file, add the following line to enable fowarding.
net.ipv4.ip_forward=1
Reload sysctl.
~]# sysctl -p
If using firewalld, configure the WAN interface (eth0 in this example) to be bound to the public zone, and configure the LAN interface (eth1 in this example) to be bound ot the internal zone.
firewall-cmd --zone=public --add-interface=eth0 --permanent
firewall-cmd --zone=internal --add-interface=eth1 --permanent
Allow traffic on port 3128.
firewall-cmd --zone=internal --add-port=3128/tcp --permanent
Forward HTTP traffic (port 80) from your LAN interface to the WAN interface. Replace x.x.x.x with the IP address of your WAN interface.
firewall-cmd --zone=internal --add-forward-port=port=80:proto=tcp:toport=3128:toaddr=x.x.x.x --permanent
Configure firewalld to use masquerading.
firewall-cmd --zone=internal --add-masquerade --permanent
Reload the firewalld.
firewall-cmd --reload
Your firewall should now have somthing similar to this.
~]# firewall-cmd --list-all --zone=internal
internal
target: default
icmp-block-inversion: no
interfaces: eth0 eth1
sources:
services: ssh dhcpv6-client
ports:
protocols: 3128/tcp
masquerade: port=80:proto=tcp:toport=3128:toaddr=192.168.0.2
forward-ports:
sourceports:
icmp-blocks:
rich rules:
If using iptables, add the following rules. Replace x.x.x.x/xx with the IP address and prefix of the Squid proxy server.
iptables -t nat -A PREROUTING -i eth1 -p tcp --dport 80 -j DNAT --to x.x.x.x:3128
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 3128
iptables -I INPUT -s x.x.x.x/xx -p tcp --dport 3128 -j ACCEPT
iptables -t nat -A POSTROUTING -o eth1 -j MASQUERADE
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT
iptables -A FORWARD -i eth0 -o eth1 -j ACCEPT
Squid.conf
In the /etc/squid/squid.conf file, configure port 3128 to intercept traffic that will be forwarded to the squid proxy server. Ensure the hostname of the Squid proxy server is visible. Replace your.hostname with the actual hostname of the Squid proxy server.
http_port 3128 intercept
visible_hostname your.hostname
Allow all http access.
http_access allow all
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to restart squid.
systemctl restart squid
If your system is using init, use the service command to restart squid.
service squid restart
You can now use Wireshark to verify that traffic is being routed through your Squid proxy server.
Did you find this article helpful?
If so, consider buying me a coffee over at 