
HTTPD can be configured to use HTTPS to encrypt the traffic between the client and server using either a certificate purchased from a trusted CA (certificate authority), such as www.verisign.com, or using a self signed certificate. The main difference between a certificate from a trusted CA and a self signed certificate is that web browsers will display a warning message when a self signed certificate is used.
Use apt-get or yum to install the SSL module. The installation of the SSL module will add the ssl.conf file to the /etc/httpd/conf.d/ directory.
yum install mod_ssl
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to start and enable httpd.
systemctl enable httpd
systemctl start httpd
systemctl status httpd
If your system is using init, use the chkconfig and service commands to start and enable httpd.
chkconfig httpd on
service httpd start
service httpd status
Ensure iptables is configured to allow traffic on port 443.
If your /etc/httpd/conf/httpd.conf file contains ServerName www.example.com and DocumentRoot "/var/www/html", you should now be able to access your site using HTTPS.
If your server uses virtual hosts, edit the /etc/httpd/conf.d/ssl.conf file to mirror your virtual host configuration.
SELinux
Use the ls -Z command to view the SELinux permissions of the files in the /var/www/html directory. In this example, the index.php context is admin_home_t. HTTPD needs the type to be httpd_sys_content_t.
ls -Z /var/www/html
. . .
-rwxrwxrwx. root root unconfined_u:object_r:admin_home_t:s0 index.php
Use the restorecon command to update all of the directories and files used by HTTPD to have httpd_sys_content_t.
restorecon -Rv /var/www/html
Use the ls -Z command again to confirm the context is httpd_sys_content_t.
ls -Z /var/www/html
. . .
-rwxrwxrwx. root root unconfined_u:object_r:httpd_sys_content_t:s0 index.php
Create a public / private key pair
The installation of the SSL module will add the localhost.crt (public certificate) and localhost.key (private key), as well as the server-chain and ca-bundle certificates.
- /etc/pki/tls/certs/locahost.crt
- /etc/pki/tls/private/localhost.key
- /etc/pki/tls/certs/server-chain.crt
- /etc/pki/tls/certs/ca-bundle.crt
If you would prefer to use your own self signed certificate, OpenSSL can be used to create the self signed public certificate and private key. Then, the localhost.csr and localhost.key can be replaced with your own public certificate and private key in the /etc/httpd/conf.d/ssl.conf file.
AVOID TROUBLE
The certificate Common Name (CN) will almost always need to match the DNS hostname of the web server the certificate is being used for. For example, if the certificate will be used for SSL / HTTPS on the web server producing www.freekb.net, then the certificates common name (CN) will need to be www.freekb.net or *.freekb.net.
If your system is using systemd, use the systemctl command to start and enable httpd.
systemctl enable httpd
systemctl start httpd
systemctl status httpd
If your system is using init, use the service command to start and enable httpd.
service httpd enable
service httpd start
service httpd status
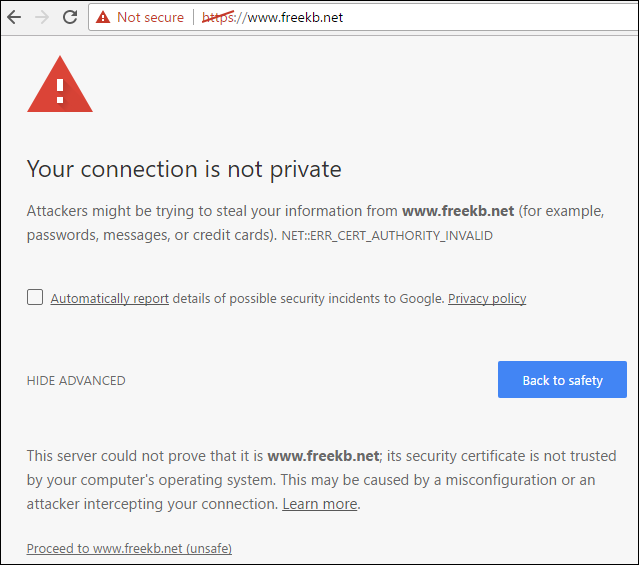
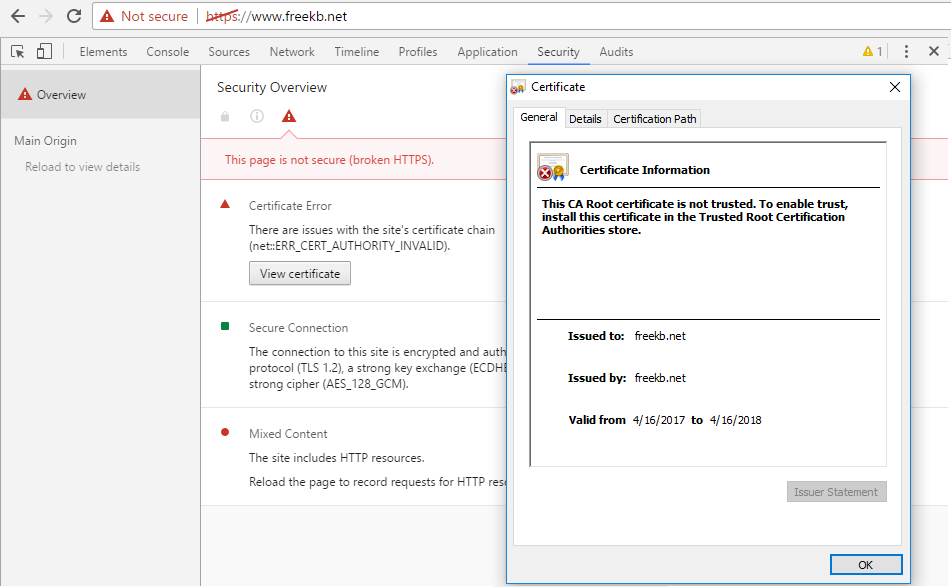
In this example, a self signed public certificate was created for freekb.net, and Chrome compalins that the root certificate is not trusted, because the certificate is not in the trusted root certificate authorities store. This is the expected behavior of a self signed certificate.
Did you find this article helpful?
If so, consider buying me a coffee over at 