
Let's take an example of a page in your app that you want to secure, so that visitors must provide a username and password to be able to access the page. In this example, the "Sample" page is unsecured, meaning any visitor can go to with the Sample page without having to provide credentials.
In WebSphere, enable Application Security. This is usually done by checkmarking "Enable application security" at at Security > Global Security. Less often, this is done by creating a Security Domain that has application security enabled and then the security domain is assigned to the application server that contains the application.

Or, wsadmin can be used to determine if Application Security is enabled or disabled. You may want to use -conntype NONE when performing this task.
# jacl
$AdminTask isAppSecurityEnabled{}
# jython
AdminTask.isAppSecurityEnabled()
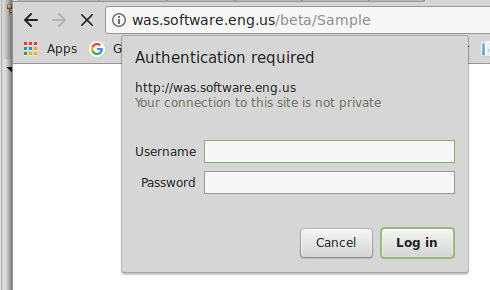
Define a security role in your Java applications web.xml file. In this example, a role named "Authenticated" is created, and the Sample page is protected.
<security-constraint>
<display-name>SampleConstraint</display-name>
<web-resource-collection>
<web-resource-name>Sample</web-resource-name>
<url-pattern>/Sample</url-pattern>
<http-method>GET</http-method>
<http-method>PUT</http-method>
<http-method>HEAD</http-method>
<http-method>TRACE</http-method>
<http-method>POST</http-method>
<http-method>DELETE</http-method>
<http-method>OPTIONS</http-method>
</web-resource-collection>
<auth-constraint>
<description>Authenticated</description>
<role-name>Authenticated</role-name>
</auth-constraint>
<user-data-constraint>
<transport-guarantee>NONE</transport-guarantee>
</user-data-constraint>
</security-constraint>
<login-config>
<auth-method>BASIC</auth-method>
</login-config>
<security-role>
<role-name>Authenticated</role-name>
</security-role>
Now, when navigating to the Sample page, there will be a prompt to provide a username and password. You will not be able to access the Sample page until you've provided a valid username and password. At this point, we've not yet developed the logic to validate the username and password against an authentication systems, thus the Sample page cannot be accessed.
When an application is configured with a security role, the role will need to be mapped to users and/or groups. In this example, the app has been configured with a security role called "Authenticated". There are a few different ways to map the security role to users / groups.
- Map users / groups to the security role in the WebSphere admin console
- Map users / groups to the security role using wsadmin
- Map users / groups to the security role using application.xml and ibm-application-bnd.xml in the Java app
Map users / groups to the security role in the WebSphere admin console
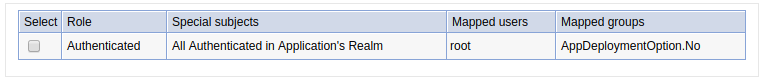
At Applications > All applications > your application > Security role to user/group mapping, by default, no user or group will be mapped to the role. In this example, user "root" has been mapped to the "Authenticated" role. After mapping the user / group to the role, you'll have to restart the app for this change to take effect.
Map users / groups to the security role using wsadmin
The following wsadmin command can be used to map user / group to your security role.
AdminApp.edit('your_ear', '[ -MapRolesToUsers [[ your_role AppDeploymentOption.No AppDeploymentOption.Yes your_username "" AppDeploymentOption.No user:defaultWIMFileBasedRealm/uid=your_username,o=defaultWIMFileBasedRealm "" ]]]' )
Map users / groups to the security role using application.xml and ibm-application-bnd.xml in the Java app
If you want to map users / groups to the role using application.xml and ibm-application-bnd.xml, in the EAR (not the WAR), create the application.xml and ibm-application-bnd.xml files in the META-INF directory, if they do not already exist. Add the following markup to each file.
application.xml
<?xml version="1.0" encoding="UTF-8"?>
<application xmlns="http://java.sun.com/xml/ns/javaee" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://java.sun.com/xml/ns/javaee http://java.sun.com/xml/ns/javaee/application_5.xsd" version="5">
<display-name>Sample</display-name>
<module>
<web>
<web-uri>Sample.war</web-uri>
<context-root>beta</context-root>
</web>
</module>
<security-role>
<role-name>Authenticated</role-name>
</security-role>
</application>
ibm-application-bnd.xml
<?xml version="1.0" encoding="UTF-8"?>
<application-bnd
xmlns="http://websphere.ibm.com/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://websphere.ibm.com/xml/ns/javaee http://websphere.ibm.com/xml/ns/javaee/ibm-application-bnd_1_0.xsd" version="1.0">
<security-role name="Authenticated">
<user name="john.doe" />
<special-subject type="ALL_AUTHENTICATED_USERS" />
</security-role>
</application-bnd>
Restart the application for these changes to take effect.
Now, when navigating to the Sample page, after providing a username and password that was mapped to the "Authenticated" users role, you should be able to get to the Sample page.

Did you find this article helpful?
If so, consider buying me a coffee over at 